Silent Signal
@silentsignalhu
Professional ethical hacking services
ID: 2241207936
http://silentsignal.eu 11-12-2013 18:49:27
232 Tweet
1,1K Takipçi
55 Takip Edilen





2 new vulnerabilities in core components of the #IBMi operating system were disclosed last week. Silent Signal itjungle.com/2023/07/24/ser…





It was an honor to present our #IBMi exploits at #TROOPERS24 today! You'll have to wait until TROOPERS Conference releases the recordings for the full show (incl. live demos), until then you can find our slides here: silentsignal.hu/docs/S2-TROOPE…


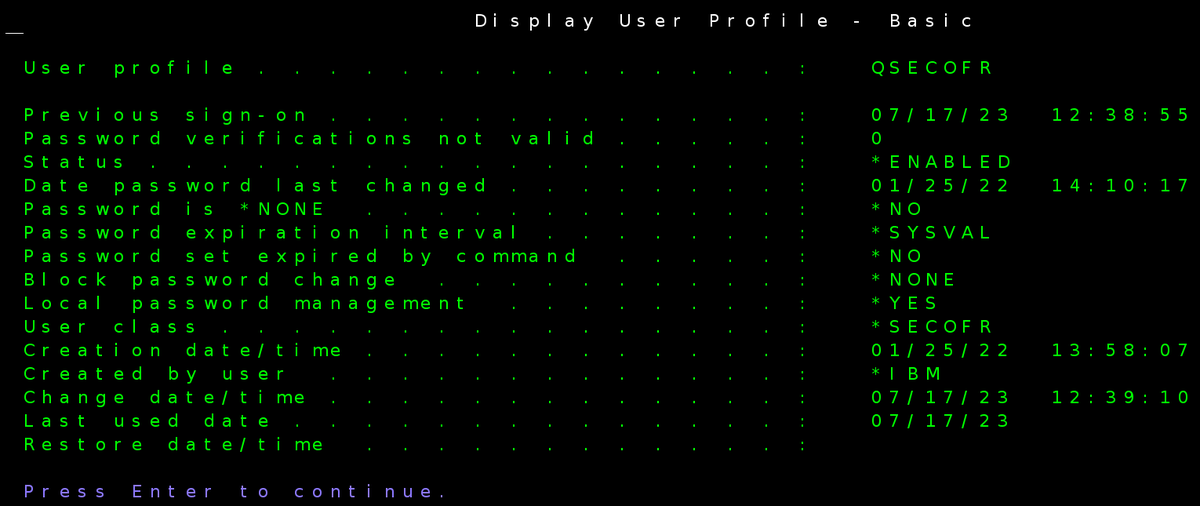
IBM issued a fix to CVE-2024-27275 that mitigates an #IBMi privilege escalation technique we published last year: 🥷blog.silentsignal.eu/2023/03/30/boo… 🧑🏭ibm.com/support/pages/… The PTF restricts the use of the ADDPFTRG command - this is a breaking change documented in the Memo to Users.

The recording of our TROOPERS Conference presentation is now online, enjoy! #TROOPERS24 - IBM i for Wintel Hackers youtube.com/watch?v=t4fUvf… #IBMi