Ayush Anand
@securityinbits
I tweet about my learning in Malware analysis and DFIR journey.
Opinions are mine only!
ID: 3483789552
https://www.securityinbits.com/ 07-09-2015 17:04:43
389 Tweet
1,1K Takipçi
256 Takip Edilen




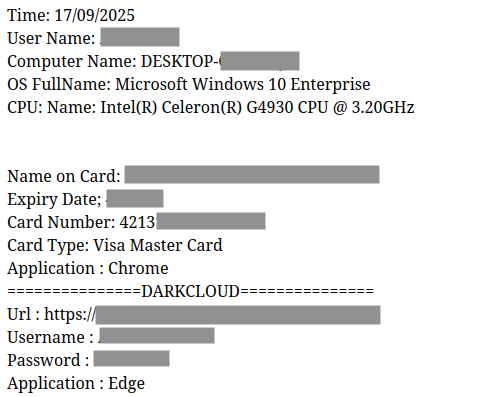
Attackers are still dumping LSASS - comsvcs.dll is showing up in real breaches. What's Inside: ✅ Exact cmd ✅Visual Sigma mapping ✅ Microsoft (Kusto) + Splunk queries Thanks to Florian Roth ⚡️, Nasreddine Bencherchali & Swachchhanda Poudel for the Sigma rules 👇 Full blog link in reply