
security_dumpster
@securitydumpstr
303: @ securitydumpster.bsky.social Life long snowboarder and opportunist threat hunter | my views are my own
ID: 1684912605578539008
28-07-2023 13:04:57
72 Tweet
144 Takipçi
340 Takip Edilen





📣SPEAKER ANNOUNCEMENT📣 We're excited to announce our next #BlueHat speakers: Mark Parsons (security_dumpster) and Colin Cowie from Sophos. They will be presenting a talk titled “Patterns in the Shadows: Scaling Threat Hunting and Intelligence for Modern Adversaries.” Mark is a



Recent trick related to .RDP files used by the SVR 🇷🇺 is worth threat hunting for. Basically they’re doing what this Black Hills Information Security blog demoed in 2022: blackhillsinfosec.com/rogue-rdp-revi… Reports: 1. cert.gov.ua/article/6281076 2. aws.amazon.com/blogs/security… 3. microsoft.com/en-us/security…




Hey :) We published a blog talking about ORB networks and a summarise of the purpose, use cases and more: team-cymru.com/post/an-introd… This blog is also a teaser for more blogs to come 👀 Team Cymru Threat Research


🔥 New from Phil Stokes ⫍🐠⫎ , Raffaele Sabato and Tom Hegel: 🇰🇵 BlueNoroff Hidden Risk | Threat Actor Targets Macs with Fake Crypto News and Novel Persistence sentinelone.com/labs/bluenorof…

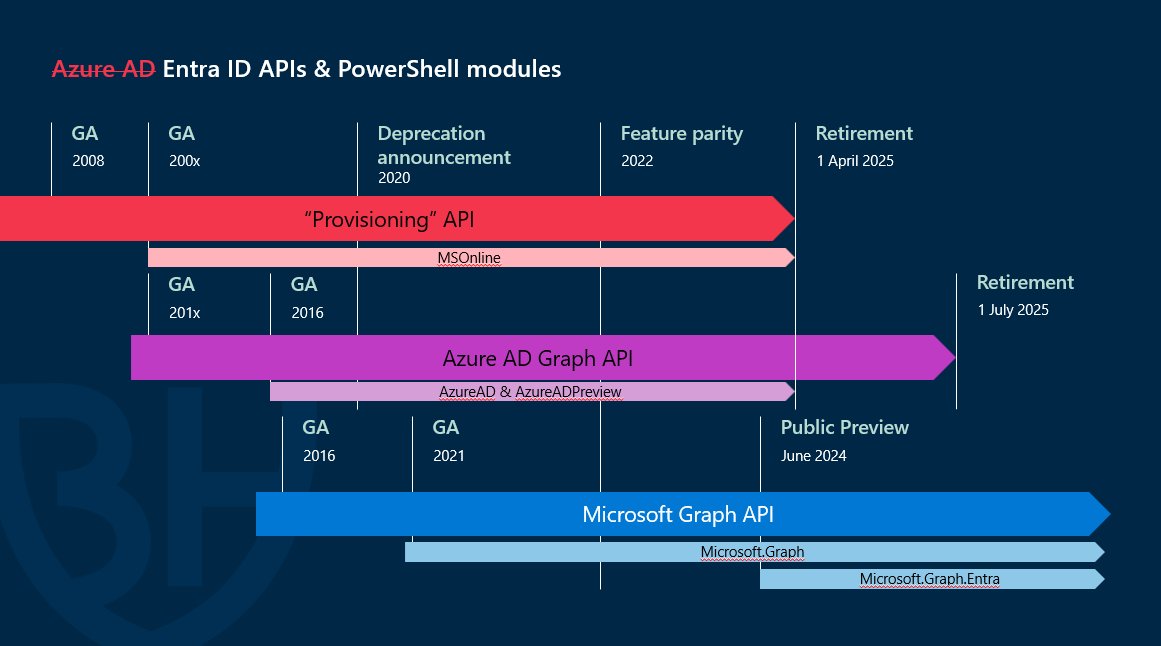
My Microsoft BlueHat talk "Deprecating Azure AD Graph API is Easy and Other Lies We Tell Ourselves" is now on Youtube! Link to recording & slide deck at aadinternals.com/talks/

My (and my copresenter Colin Cowie) Microsoft BlueHat talk “Patterns in the Shadows: Scaling Threat Hunting and Intelligence for the Modern Adversary” is on YouTube, hope you enjoy! youtu.be/n7GVxDxwOUc?fe…





