RedDrip Team
@reddrip7
Technical Twitter of QiAnXin Technology, leading Chinese security vendor. It is operated by RedDrip Team which focuses on malware, APT and threat intelligence.
ID: 986796925612470272
http://ti.qianxin.com 19-04-2018 02:41:35
392 Tweet
15,15K Takipçi
29 Takip Edilen



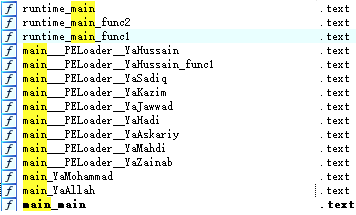
![RedDrip Team (@reddrip7) on Twitter photo #APT #Patchwork targets Nepal with Spyder malware
dcd38befbaff3b153c40cd9c2858e72a
myprivatedrives[.]com
hxxp://myprivatedrives.com/ticket_line/openai.php
hxxp://myprivatedrives.com/ticket_line/certificate.php #APT #Patchwork targets Nepal with Spyder malware
dcd38befbaff3b153c40cd9c2858e72a
myprivatedrives[.]com
hxxp://myprivatedrives.com/ticket_line/openai.php
hxxp://myprivatedrives.com/ticket_line/certificate.php](https://pbs.twimg.com/media/GlVmpLBa4AI-fRq.png)