
Security Chat
@phishsecurity
Keeping an eye on the cyber security sector. How much is marketing nonsense?
ID: 3727316441
21-09-2015 10:34:28
8,8K Tweet
1,1K Takipçi
807 Takip Edilen



404media.co/a-network-of-a… Very interesting watering hole attack by Fin7- going for the AI nude audience #ThreatIntelligence #cybersecuritytips initial investigation by Silent Push

Nice and Simple Scattered Spider Pivots - Thanks to Initial Intel and previous posts from Chris Duggan 1⃣ Regex Pattern And Server Header 2⃣ Regex, Server Header and ASN 3⃣ Regex, Dates, ASN and Name Server Utilising Domain Search and Web Scanner from Silent Push



Definite threat alert: https://d[.]goldmansachserfd[.]top/?jp=1 found on app.silentpush.com/shared/eb03c13… via Silent Push Goldman Sachs
![Silent Push (@silentpush) on Twitter photo Definite threat alert: https://d[.]goldmansachserfd[.]top/?jp=1 found on app.silentpush.com/shared/eb03c13… via <a href="/silentpush/">Silent Push</a> <a href="/GoldmanSachs/">Goldman Sachs</a> Definite threat alert: https://d[.]goldmansachserfd[.]top/?jp=1 found on app.silentpush.com/shared/eb03c13… via <a href="/silentpush/">Silent Push</a> <a href="/GoldmanSachs/">Goldman Sachs</a>](https://pbs.twimg.com/media/GdRDilzbAAAjZ6C.jpg)

In this type of field its important to never rely on one tooling. Nothing is the holy grail in my opinion. So combine the bunch to that overview going. I just learned that you can use several datasources Silent Push Lets see what I can find with open-dir datasource.
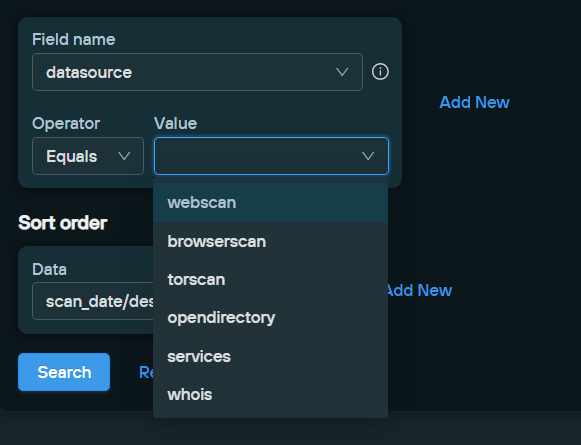

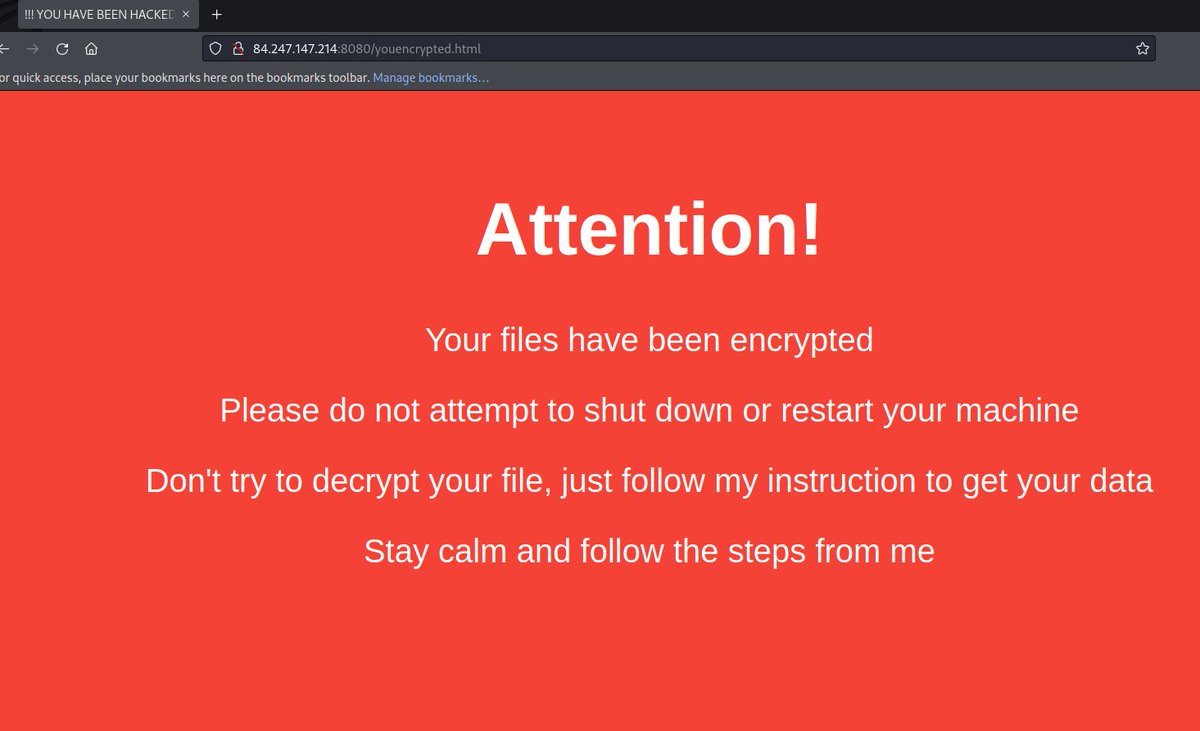
Silent Push searching on keywords that are often used by threatactors can bring you to juicy open directories! hxxp://84.247.147.214:8080/ uhoh, the worst ransomware I have seen.

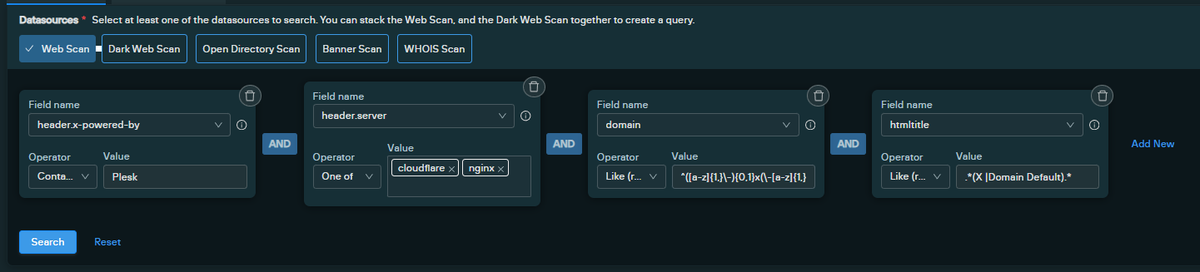
We're seeing lots of similar #phishing domains to those reported by John Hammond 🚨 The actors are using consistent naming schemes and web hosting software that we can capture with a search query. The actors have also made two other woopsies that we'll show down below👇


Pivoting on a file named google-privacy-policy-Cb0CGVRT.svg was used in a ClickFix campaign. hash: 51da32d8582706c6229f9a548da21b9845cb51ee55736a252addcdf2b1df5848 Silent Push Fox_threatintel WatchingRac Squiblydoo ܛܔܔܔܛܔܛܔܛ Mikhail Kasimov Demon Szabolcs Schmidt


Our team Silent Push just dropped a definitive look at SocGholish (operated by TA569) and the initial access broker ecosystem they are facilitating. Big thanks to past researchers who have worked on SocGholish! We've got details about our visibility @ silentpush.com/blog/socgholis… 🖖🏻






Rumors are spreading about a mayor #LawEnforcement operation against #Rhadamanthys #Stealer. Who said what? and me have been monitoring the situation closely. -Rhada domains under active law enforcement control - Customers are adviced to delete all servers Image via club1337




![MalwareHunterTeam (@malwrhunterteam) on Twitter photo Fake Google Chrome download site: https://google.[tw].cn/
The SSL cert for this domain has been given by "Google Trust Services". Not think I have to say anything about it...
🤷♂️ Fake Google Chrome download site: https://google.[tw].cn/
The SSL cert for this domain has been given by "Google Trust Services". Not think I have to say anything about it...
🤷♂️](https://pbs.twimg.com/media/Gc2cY68XwAAoR3z.jpg)
![ܛܔܔܔܛܔܛܔܛ (@skocherhan) on Twitter photo #NetSupportRat #C2
5[.]181[.]159[.]204
94[.]158[.]244[.]161
AS39798 MivoCloud SRL 🇺🇸
<a href="/Huntio/">Hunt.io</a> <a href="/abuse_ch/">abuse.ch</a> <a href="/JAMESWT_WT/">JAMESWT</a> <a href="/500mk500/">Mikhail Kasimov</a> <a href="/anyrun_app/">ANY.RUN</a> <a href="/silentpush/">Silent Push</a> <a href="/MivoCloud/">MivoCloud</a> #NetSupportRat #C2
5[.]181[.]159[.]204
94[.]158[.]244[.]161
AS39798 MivoCloud SRL 🇺🇸
<a href="/Huntio/">Hunt.io</a> <a href="/abuse_ch/">abuse.ch</a> <a href="/JAMESWT_WT/">JAMESWT</a> <a href="/500mk500/">Mikhail Kasimov</a> <a href="/anyrun_app/">ANY.RUN</a> <a href="/silentpush/">Silent Push</a> <a href="/MivoCloud/">MivoCloud</a>](https://pbs.twimg.com/media/GvjRjwpWwAECAOn.jpg)

![Lontz (@lontze7) on Twitter photo Expanding Google Careers phishing indicators with <a href="/ValidinLLC/">Validin</a> Lookalike Domains & <a href="/silentpush/">Silent Push</a> WHOIS Scanner
807 total indicators - This campaign is massive.
sample regex: /^(apply|hire|start)\.g(recruit|talent|team|app|hiring|hire|career)[a-z]+\.com$/
pastebin.com/UxmPwpQJ Expanding Google Careers phishing indicators with <a href="/ValidinLLC/">Validin</a> Lookalike Domains & <a href="/silentpush/">Silent Push</a> WHOIS Scanner
807 total indicators - This campaign is massive.
sample regex: /^(apply|hire|start)\.g(recruit|talent|team|app|hiring|hire|career)[a-z]+\.com$/
pastebin.com/UxmPwpQJ](https://pbs.twimg.com/media/G2UJ4gFWsAAfRhv.png)
![MalasadaTech (@malasadatech808) on Twitter photo Some more PoisonSeed domains! The ones at the top were created just 30 minutes ago! They don't appear to be up yet. Block it proactively!
ytcareersstaffing[.]com
ytcareersprospect[.]com
ytcareersdesk[.]com
ytcareersjob[.]com
ytcareersgroup[.]com
ytcareersopportunity[.]com Some more PoisonSeed domains! The ones at the top were created just 30 minutes ago! They don't appear to be up yet. Block it proactively!
ytcareersstaffing[.]com
ytcareersprospect[.]com
ytcareersdesk[.]com
ytcareersjob[.]com
ytcareersgroup[.]com
ytcareersopportunity[.]com](https://pbs.twimg.com/media/G3OUmxUXUAABkay.jpg)


