nkx
@nek0x_
IT security evaluator @jtsecES
ID: 1274709008000208896
http://nek0x.github.io 21-06-2020 14:21:33
108 Tweet
250 Takipçi
1,1K Takip Edilen






I have just obtained a new Certified Red Team Professional (CRTP) certification from Altered Security


Malware Analysis Series has exactly 450 pages so far: MAS_1: exploitreversing.com/2021/12/03/mal… MAS_2: exploitreversing.com/2022/02/03/mal… MAS_3: exploitreversing.com/2022/05/05/mal… MAS_4: exploitreversing.com/2022/05/12/mal… MAS_5: exploitreversing.com/2022/09/14/mal… MAS_6: exploitreversing.com/2022/11/24/mal… MAS_7: exploitreversing.com/2023/01/05/mal…









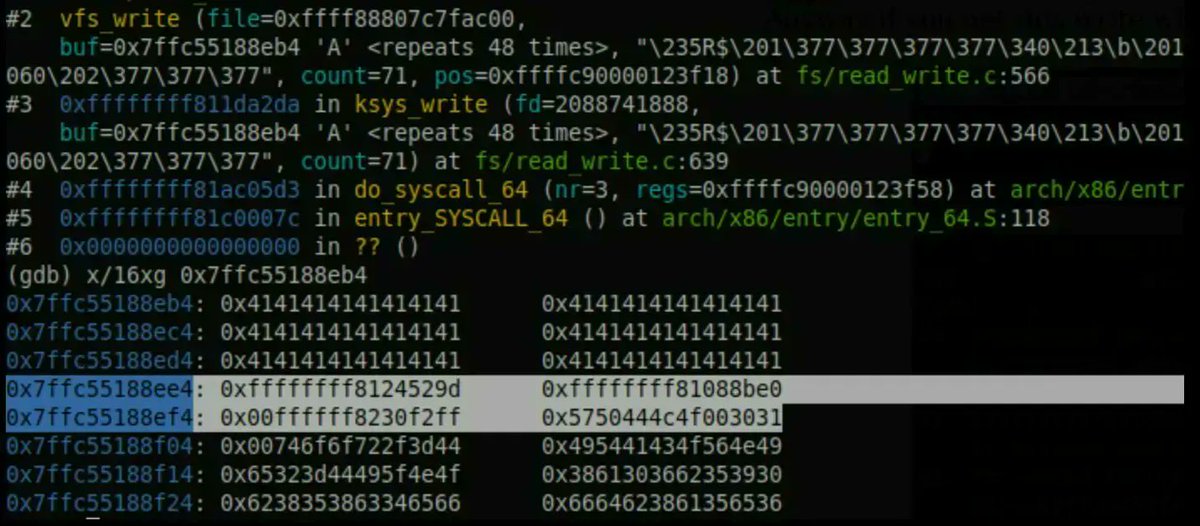
Learning the basics of Linux kernel exploitation Excellent series by I write about security stuff Debugging with QEMU: blog.k3170makan.com/2020/11/linux-… Stack Overflows: blog.k3170makan.com/2020/11/linux-… RIP control: blog.k3170makan.com/2021/01/linux-… #cybersecurity #infosec #Linux #kernel