Nosa Shandy
@localhost31337
another infosec guy | {insert your certification here}
ID: 3170412307
https://whoami.apapedulimu.click/ 24-04-2015 07:46:36
6,6K Tweet
1,1K Takipçi
1,1K Takip Edilen




Browser vulnerability research is probably one of the toughest areas for AI to automate. It's a great skill to learn. Here's an awesome intro to browser security research by Ivan Fratric 💙💛: docs.google.com/presentation/d… The talk is full of great practical examples, and good advice.
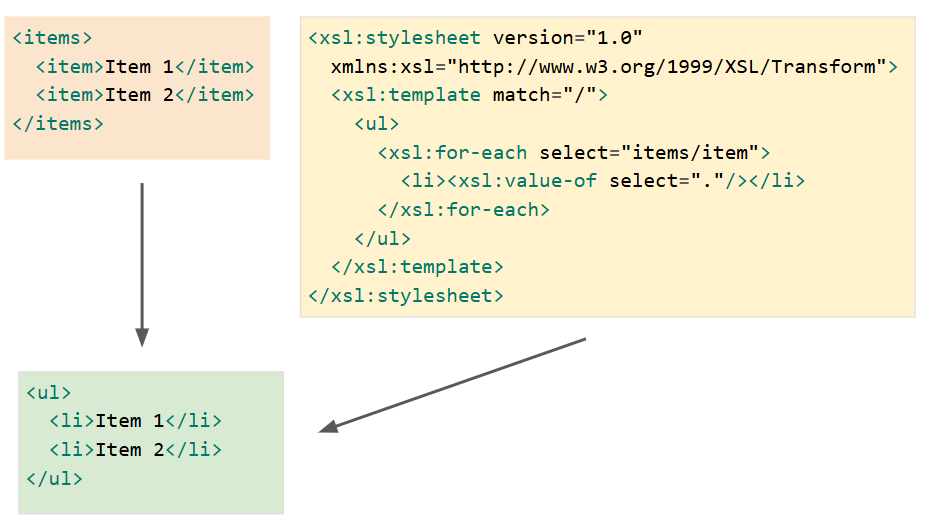








Google VRP (Google Bug Hunters) disclosed my most impactful client-side report to date: bughunters.google.com/reports/vrp/wG… TL;DR An attacker could've gained access to Gemini Code Assist Tools (GitLab, GitHub etc.) configured by the victim


Google VRP (Google Bug Hunters) No writeup yet but the report got disclosed: bughunters.google.com/reports/vrp/HR…






![Sergey Toshin (@_bagipro) on Twitter photo New Android host validation bypass technique!
[1/4] All parsed URIs in Android are android.net.Uri.StringUri objects. However, the scheme parser only looks for the ":" delimiter New Android host validation bypass technique!
[1/4] All parsed URIs in Android are android.net.Uri.StringUri objects. However, the scheme parser only looks for the ":" delimiter](https://pbs.twimg.com/media/GxR5F8AXwAAfTxY.jpg)