Josiah Smith
@josiahsecurity
ID: 1057430523746889729
31-10-2018 00:34:17
172 Tweet
64 Takipçi
193 Takip Edilen



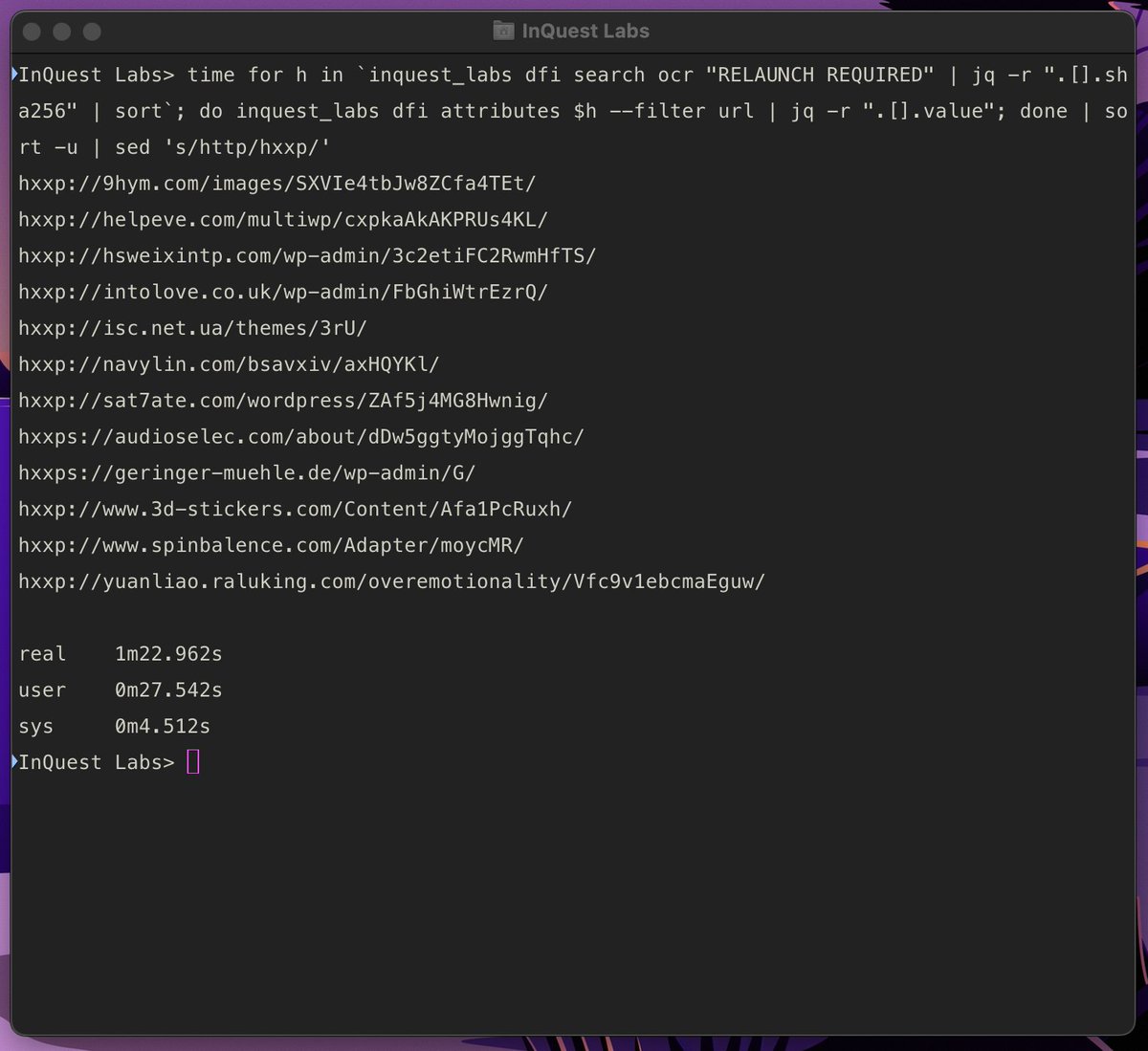
A rather interesting obfuscated #maldoc uploaded from the IR country code. InQuest Labs: labs.inquest.net/dfi/hash/2f796… Macro downloads and runs 114f0a73818653616d41cf4380d3d987 from hxxps://windowsupdates.global.ssl.fastly[.]net/README.md #cobaltstrike #malware Dmitry Melikov 👏
![InQuest (@inquest) on Twitter photo A rather interesting obfuscated #maldoc uploaded from the IR country code.
InQuest Labs: labs.inquest.net/dfi/hash/2f796…
Macro downloads and runs
114f0a73818653616d41cf4380d3d987 from hxxps://windowsupdates.global.ssl.fastly[.]net/README.md
#cobaltstrike #malware
<a href="/DmitriyMelikov/">Dmitry Melikov</a> 👏 A rather interesting obfuscated #maldoc uploaded from the IR country code.
InQuest Labs: labs.inquest.net/dfi/hash/2f796…
Macro downloads and runs
114f0a73818653616d41cf4380d3d987 from hxxps://windowsupdates.global.ssl.fastly[.]net/README.md
#cobaltstrike #malware
<a href="/DmitriyMelikov/">Dmitry Melikov</a> 👏](https://pbs.twimg.com/media/FVKFgafWAAEfzah.png)

🤖 Potentially malicious RTF document found hosted at: hxxps://[email protected]/mee/giv[.]doc SHA256: 3c0c6b9e259384a24123fa8d0f33366b0d6a99de759ac14af0c354a555443339 IOC extracted from sample: labs.inquest.net/dfi/hash/42f0a… (Automated Tweet, maybe a FP)






File-borne attacks are a mainstay of the threat landscape and InQuest’s Pedram Amini takes a deep dive into File Detection and Response (FDR) as a way to prevent such attacks. He describes what automated threat hunting is and how it can make a difference. youtube.com/watch?v=G4rfzA…



Excited to show part 4 of the File Detection and Response #FDR blog series from Pedram Amini How FDR Helps with the SecOps Staffing Dilemma inquest.net/blog/2022/09/0… #secops #CyberSecurityExpert






🚀 InQuest & ThreatConnect, Inc. unite to revolutionize threat intelligence and cybersecurity. 🌐✨ bwnews.pr/48sqvVW 🔍 InQuest's unparalleled file-based analysis and unique threat intel now integrates seamlessly with ThreatConnect's TI Ops Platform. This powerful


Huge shout out to Peter Stewart, Yashraj Solanki, and Denice 🤠 for completing the #100DaysOfYARA challenge. We've published an overview post on the second half: inquest.net/blog/100-days-… ICYMI, our first post from the halfway mark can be found here: inquest.net/blog/100-days-…





![InQuest (@inquest) on Twitter photo Password cracking for the win:
labs.inquest.net/dfi/sha256/60c…
Arabic language lure uploaded from Palestine. Passwords include "decrypt-zip2022" and "decrypt-office". Zero AV detections. The payload domain 'rep-console[.]com' is unresponsive, potentially geofenced, registered on 7/18. Password cracking for the win:
labs.inquest.net/dfi/sha256/60c…
Arabic language lure uploaded from Palestine. Passwords include "decrypt-zip2022" and "decrypt-office". Zero AV detections. The payload domain 'rep-console[.]com' is unresponsive, potentially geofenced, registered on 7/18.](https://pbs.twimg.com/media/Fe1Iq8QX0AM4k13.jpg)