Jason Frank
@jasonjfrank
Father. Husband. COO @SpecterOps
ID: 73285507
11-09-2009 02:19:50
3,3K Tweet
1,1K Takipçi
942 Takip Edilen

Kamala Harris didn't lose, America did. As a nation, we collectively failed her—and in doing so we failed girls and women, the LGBTQ community, people of color, Muslims, Jewish people, immigrants, the sick, the poor, the elderly, the people of Ukraine, and Gaza, and the planet.















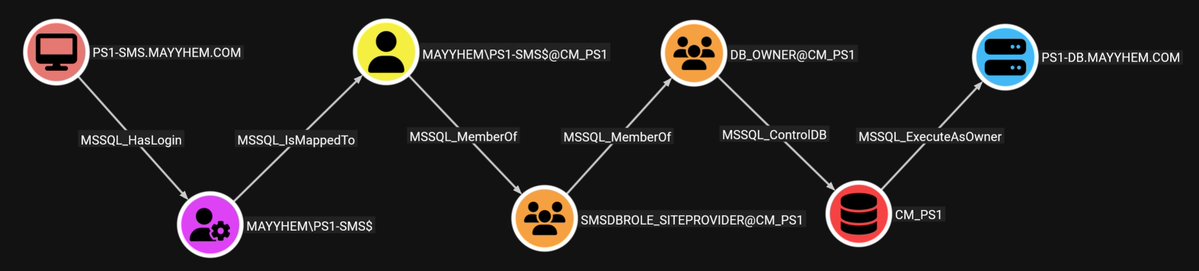
BloodHound v8.0 is here! 🎉 This update introduces BloodHound OpenGraph, revolutionizing Identity Attack Path Management by exposing attack paths throughout your entire tech stack, not just AD/Entra ID. Read more from Justin Kohler: ghst.ly/bloodhoundv8 🧵: 1/7



The AD CS security landscape keeps evolving, and so does our tooling. 🛠️ Valdemar Carøe drops info on Certify 2.0, including a suite of new capabilities and refined usability improvements. ghst.ly/45IrBxI