Jonathan Peters
@cod3nym
Threat Researcher | Detection Engineer @nextronsystems
#Yara enthusiast | C# Developer
ID: 1695738489973735424
https://github.com/cod3nym 27-08-2023 10:02:36
298 Tweet
621 Takipçi
85 Takip Edilen












Related "x-ray-health-records-qdf.bat": 69ae32f8fa7bdda3f215db7f0bf57305e82ed38a28974884b75b7015dbfa43b4 AV vendors on VT not detected this too, but at least there is a THOR APT Scanner comment... 🤷♂️


New blog post from Gameel Ali 🤘 and me: we analyze Katz Stealer. Focusing on bypassing App-Bound Chrome Encryption and compromising Electron apps; and how those behaviors can be leveraged for detection. We highlight key detection vectors uncovered during our analysis and provide


'Villa - Home Decor - Architectural Design Drawing - Prinsiri Developement - 2605h01.bat' abuse.ch bazaar.abuse.ch/sample/43a8084… Jonathan Peters Nextron Research ⚡️


Introducing Havoc Professional: A Lethal Presence We’re excited to share a first look at Havoc Professional, a next-generation, highly modular Command and Control framework, and Kaine-kit our fully Position Independent Code agent engineered for stealth! infinitycurve.org/blog/introduct…

A trojanized Autoruns DLL loading shellcode from its .data section. Currently, only THOR APT Scanner detects it on VirusTotal. virustotal.com/gui/file/1c962… #shellcode #peb Nextron Research ⚡️



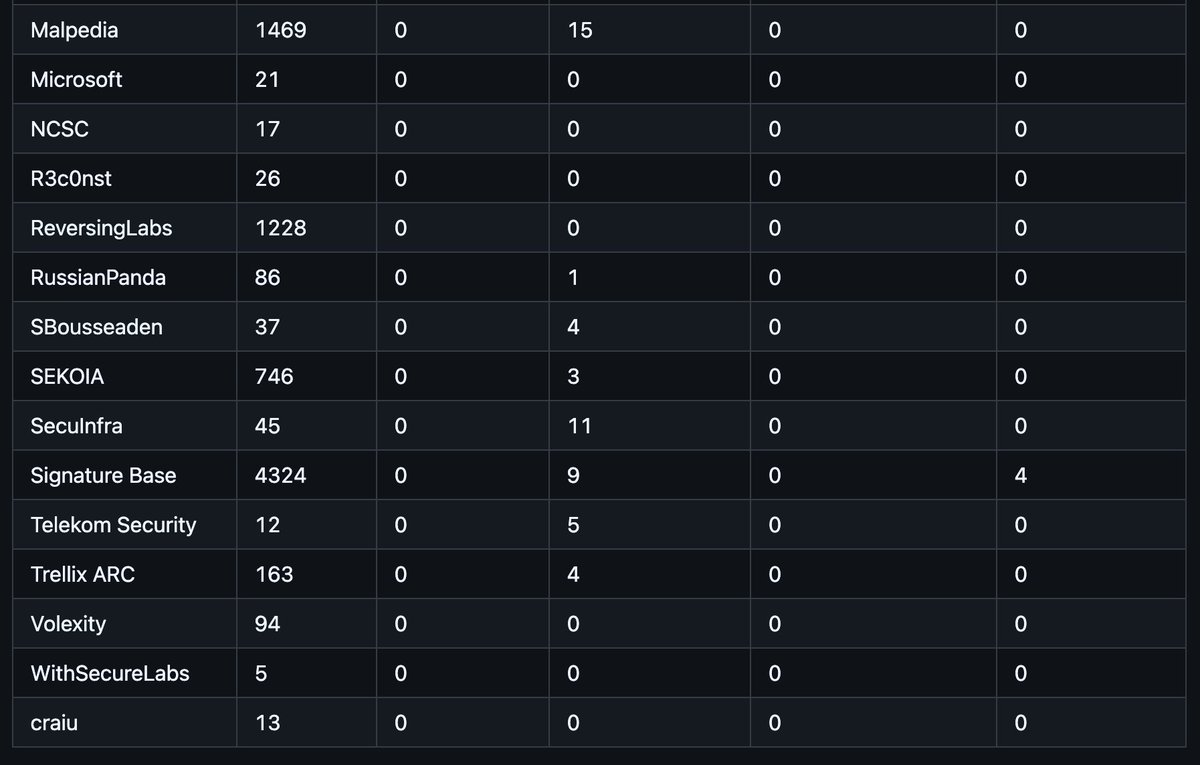
There are plenty of malware‑analysis tools - but pe‑sieve (hasherezade) + YARA Forge (Florian Roth ⚡️) is one of the sharpest offline combos to identify malware families. Dump → PE‑sieve Scan → YARA Forge ID → Malware family Step‑by‑step walkthrough in the video below 👇