Arris Huijgen
@bitsadmin
Windows Offensive Security Enthusiast 🤠
Blog: blog.bitsadmin.com
GitHub: github.com/bitsadmin
ID: 713108856679841792
https://bitsadmin.com/ 24-03-2016 21:02:55
223 Tweet
1,1K Takipçi
106 Takip Edilen


Dropping a new initial access technique via RDP that I dubbed "Rogue RDP". Use malicious .RDP files to bypass email/servers/security gateways and then run code to binary plant/exfil from your own RDP server, blinding EDR. Bonus: Target runs HyperV? RCE! blackhillsinfosec.com/rogue-rdp-revi…




Per suggestion of Jelle Vergeer, added the memory-efficient json2csv.py script to the dir2json repository. As a bonus also added dir2csv.py to convert the output of cmd.exe's dir /s /a command to csv. Useful to avoid PowerShell's logging mechanisms 😉 Enjoy!








The S is for Security. How to use WinRMS as a solid NTLM relay target, and why it’s less secure than WinRM over HTTP. By Aurélien Chalot Writeup: sensepost.com/blog/2025/is-t… PR to impacket: github.com/fortra/impacke… Demo: youtu.be/3mG2Ouu3Umk


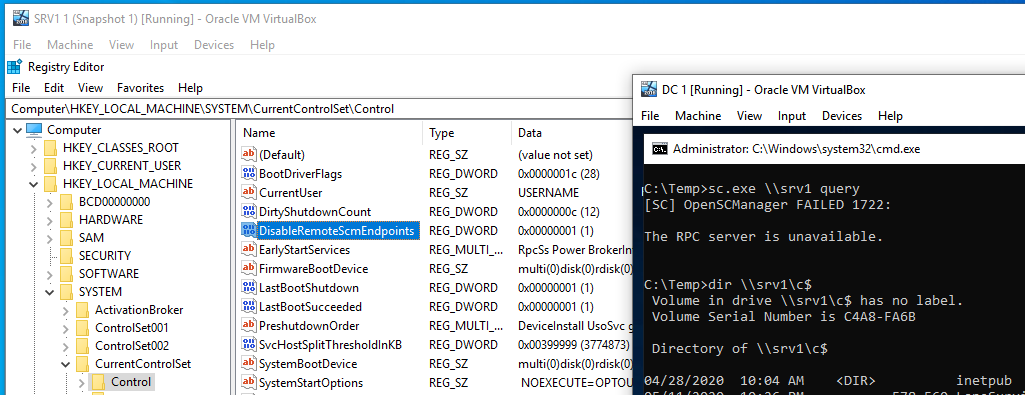
Cool, novel, lateral movement technique by William Knowles by dropping a .dll file on a remote host obtaining code execution! 💡