
Back Engineering Labs
@backengineerlab
CodeDefender Discord: discord.gg/sgedeapTMm
ID: 1617397198681157632
http://back.engineering 23-01-2023 05:42:30
20 Tweet
935 Takipçi
4 Takip Edilen



Recently, Back Engineering Labs released the crackme obfuscated by the CodeDefender and I reversed the binary: gist.github.com/5unKn0wn/24fa0…. The crackme implemented modified SipHash24, and the goal is to find the input that matches the hash. The obfuscation was nice and quite a challenge !



We are very excited to sponsor Duncan Ogilvie 🍍 with 500$ His open source contributions have made it possible to do what we do. If you have ever benefited from using x64dbg.com or other tools developed by Duncan Ogilvie 🍍 consider sponsoring him on github. Special thanks to all of




what is CodeDefender and who is the handsome man in the corner? find out tomorrow when we drop our interview with the Back Engineering Labs team
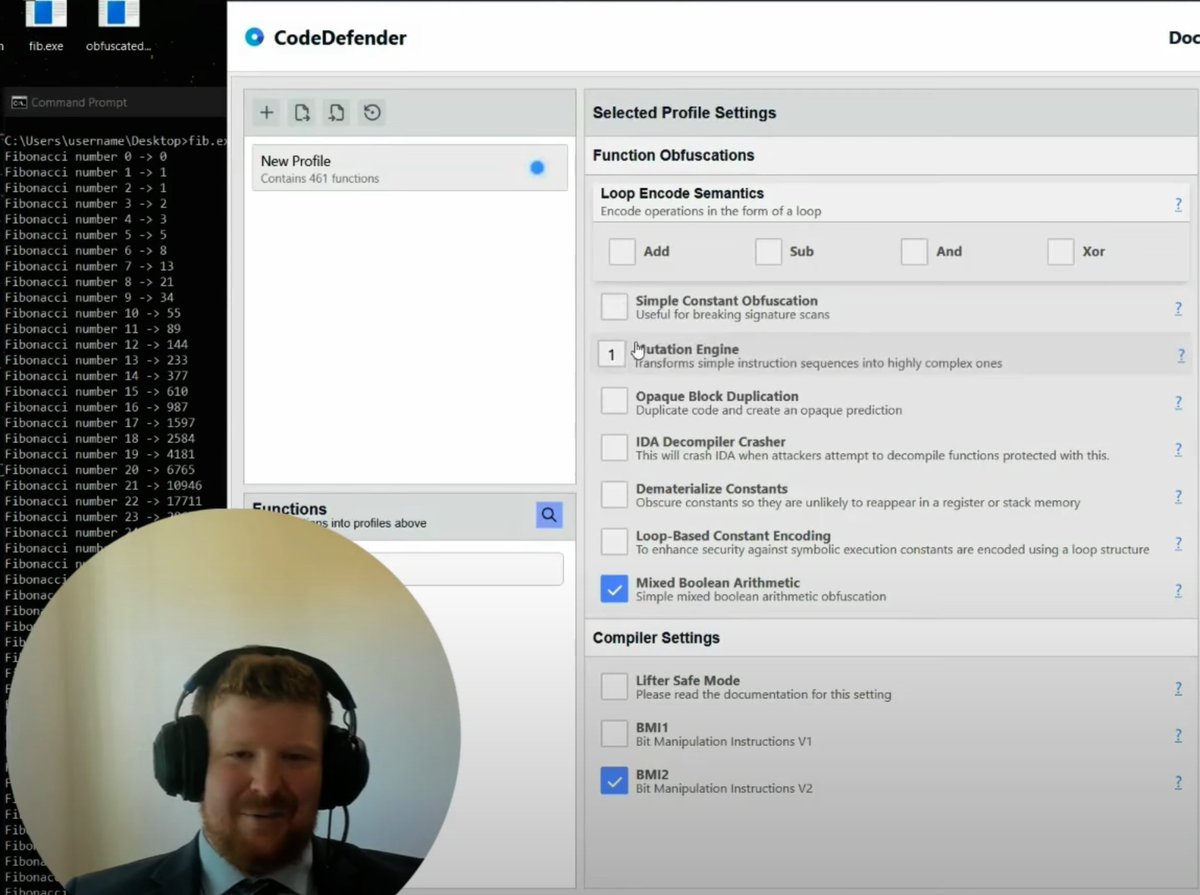

🚨 How are the geniuses at Back Engineering Labs revolutionizing binary obfuscation with CodeDefender.io? Learn about the unique challenges & solutions in bin2bin, virtualization & anti-tamper. See CodeDefender in action with a demo at the end! 👉youtu.be/3LOGxOHfUHg







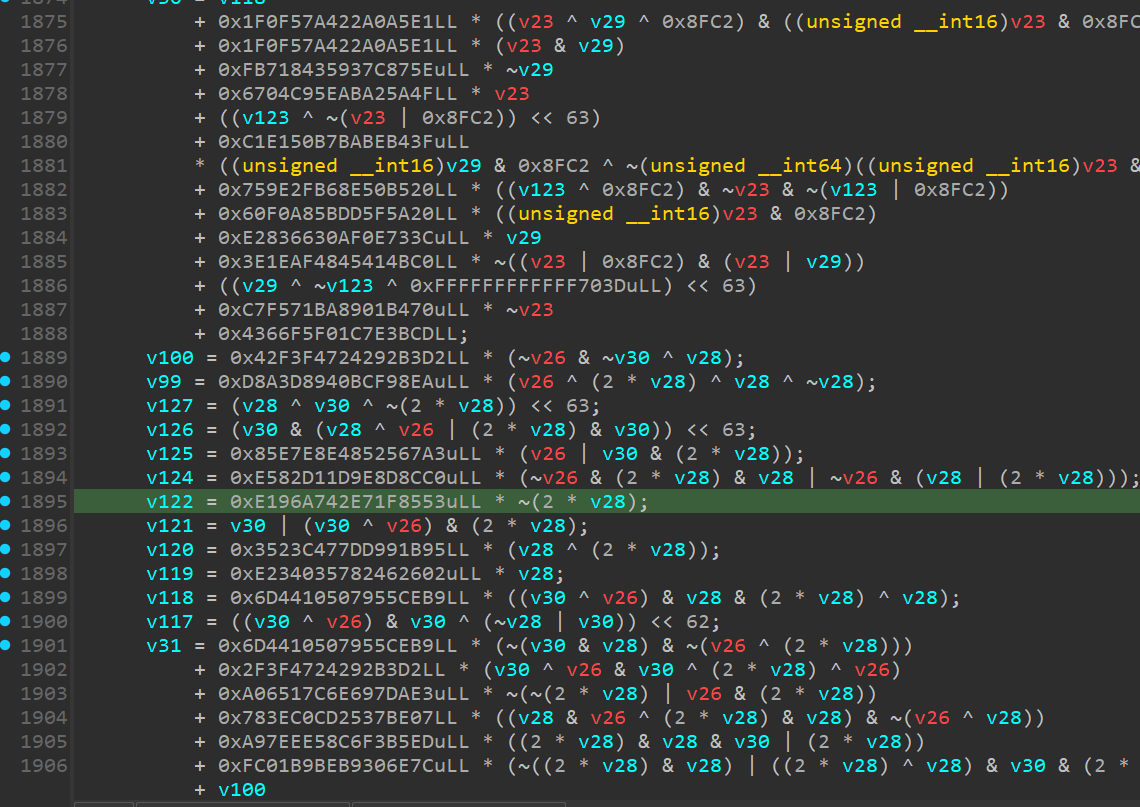
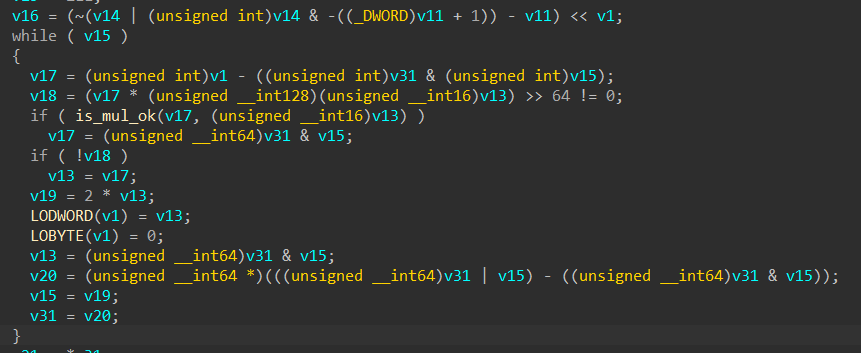
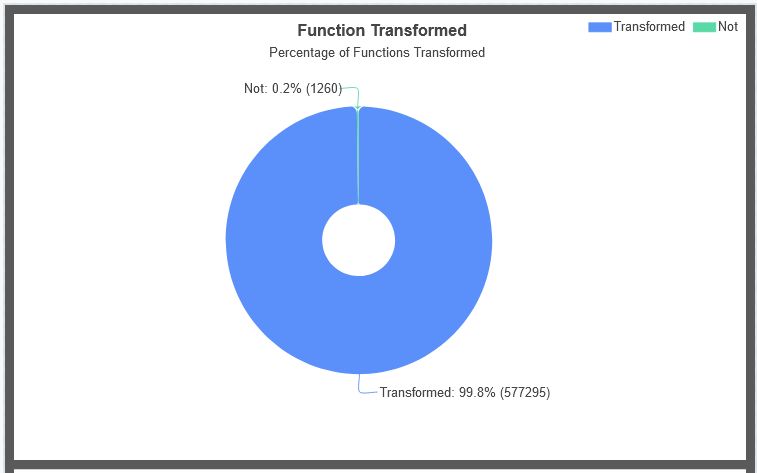






![Back Engineering Labs (@backengineerlab) on Twitter photo 🚀 CodeDefender SDK now supports source-level macros!
Obfuscate functions in Rust/C/C++ by tagging them with your pre-defined obfuscation profile.
🦀 #[codedefender("Profile1")]
💻 CODEDEFENDER("Profile1", ...)
Docs + examples 👉 github.com/codedefender-i…
#infosec #rustlang 🚀 CodeDefender SDK now supports source-level macros!
Obfuscate functions in Rust/C/C++ by tagging them with your pre-defined obfuscation profile.
🦀 #[codedefender("Profile1")]
💻 CODEDEFENDER("Profile1", ...)
Docs + examples 👉 github.com/codedefender-i…
#infosec #rustlang](https://pbs.twimg.com/media/GviPpReakAYoNKy.png)

