
ps-aux-grep root
@auxgrep
cybersecurity | Ethical hacker | Consultant | Linux Programmer 🇹🇿
ID: 1249999434169159681
https://github.com/AuxGrep 14-04-2020 09:54:43
3,3K Tweet
5,5K Takipçi
141 Takip Edilen











Mshikaji wangu Ayeem Ndimbo aliniambia kaka embu nusa mac pc hutotoka , nimeamini aseeee Nikasema nivuute angalau 2021 M1 pro ya 16GB aseee Nimeweka vms leo kama zoteeee , aseee hawa jamaa kwenye memory management wanajua.









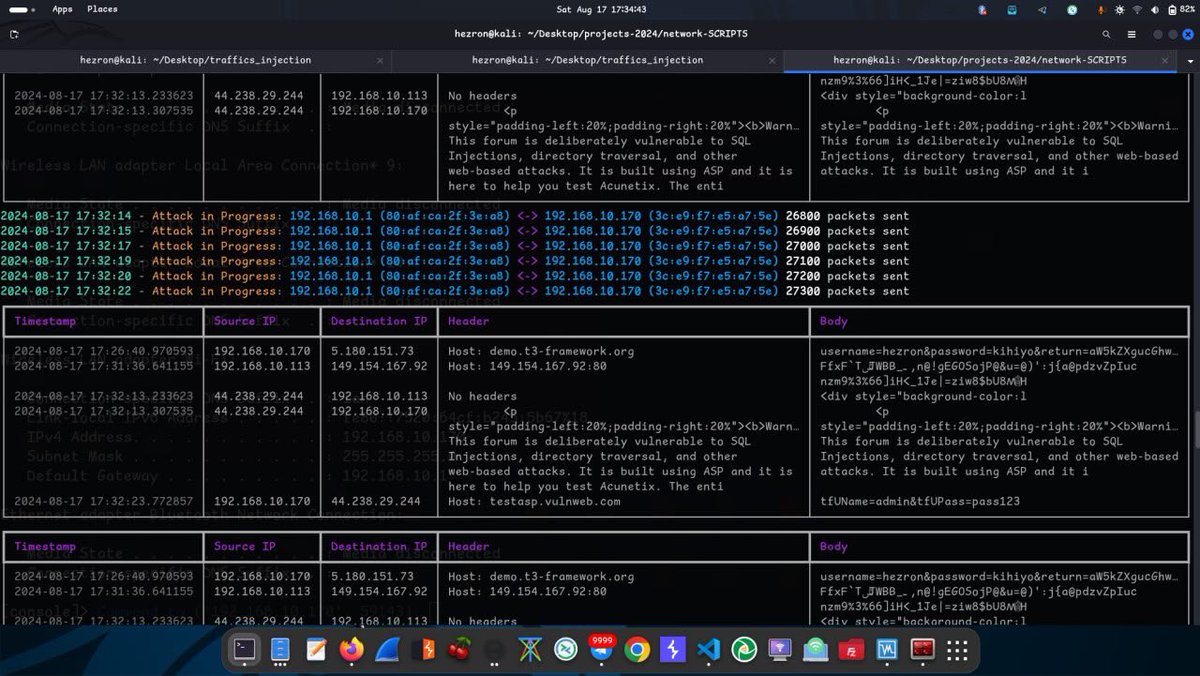
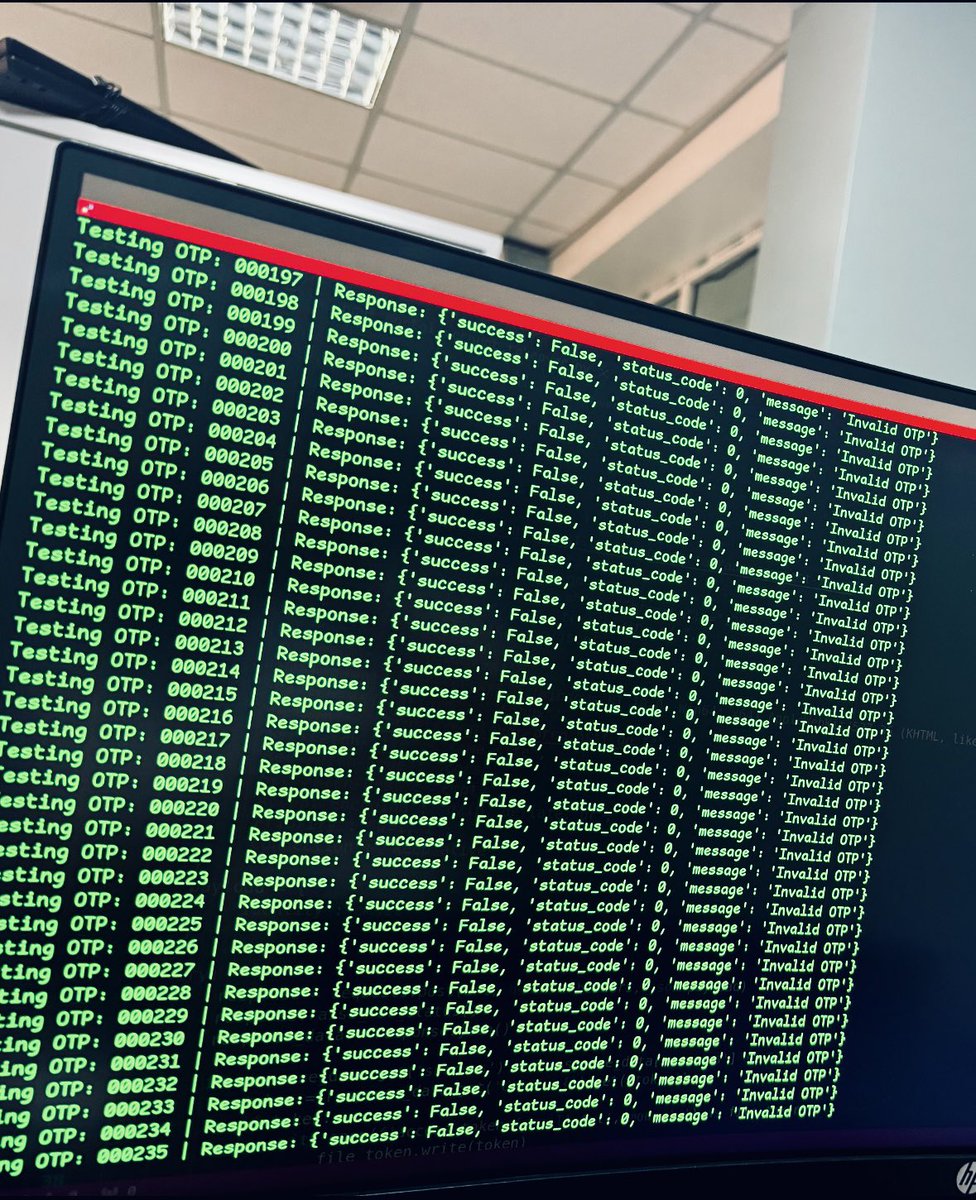

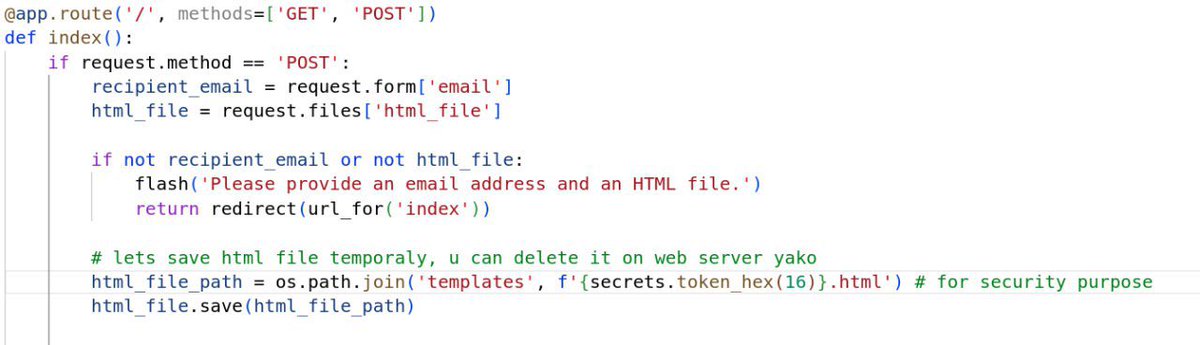
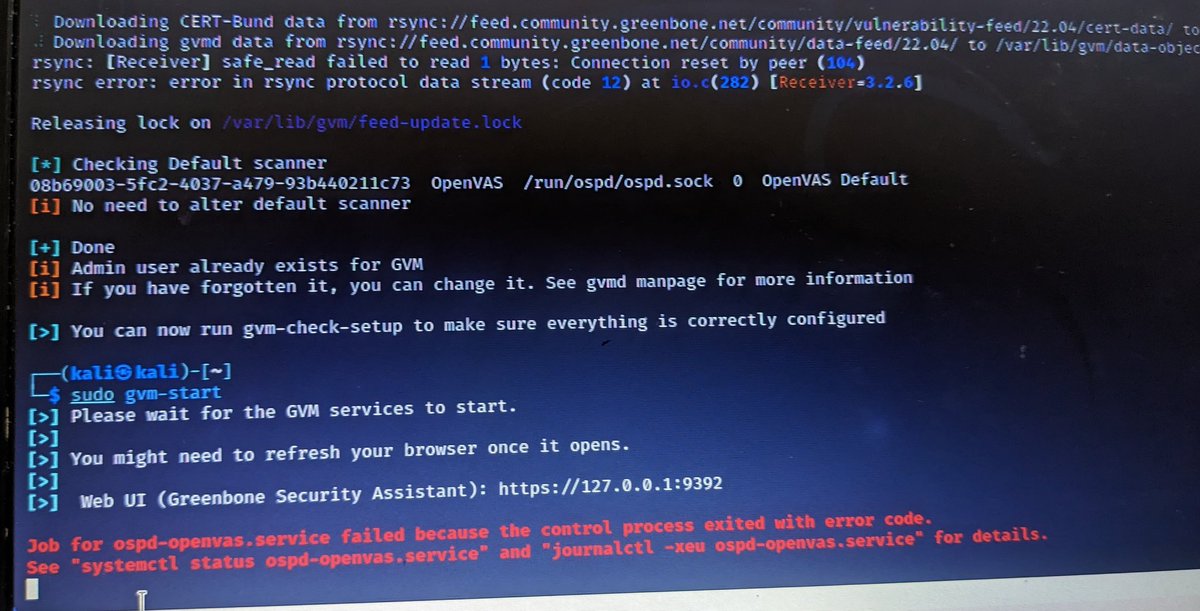
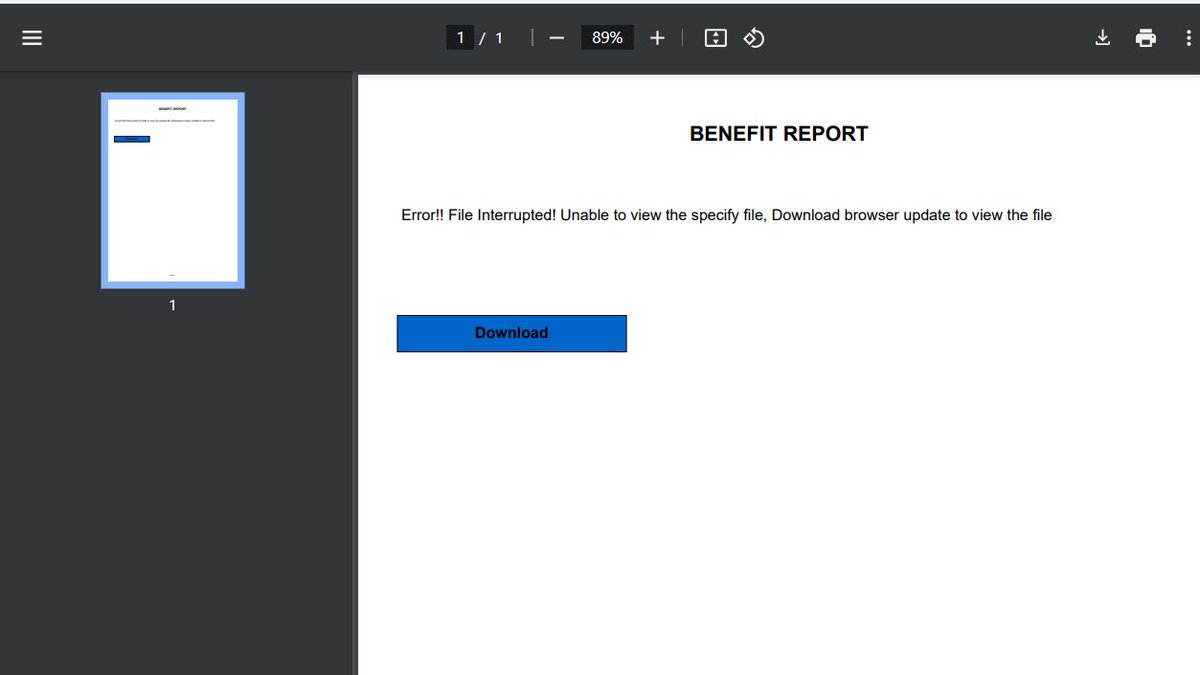
![ps-aux-grep root (@auxgrep) on Twitter photo Day 1: [email] The attacker sends “receipt.jpg”with hidden malware in its metadata, posing as proof of a payment error.
Day 2: [email] Attacker sends an Excel file with a hidden macro code,
the macro extracts the malware from “receipt.jpg” and runs it silently in memory. Day 1: [email] The attacker sends “receipt.jpg”with hidden malware in its metadata, posing as proof of a payment error.
Day 2: [email] Attacker sends an Excel file with a hidden macro code,
the macro extracts the malware from “receipt.jpg” and runs it silently in memory.](https://pbs.twimg.com/media/Gmk9i1FaoAAaWfd.jpg)