
Dr Andrew Fasano
@andrewfasano
Account inactive as of 2022
ID: 15323094
https://andrewfasano.com 05-07-2008 03:51:43
438 Tweet
549 Takipçi
618 Takip Edilen


Okay Brandon Falk just blew my mind with this knowledge that x86 is an octal machine. How is this not more commonly understood. The opcode mods use values that are obvious enums when you see them displayed as octal. gist.github.com/seanjensengrey…

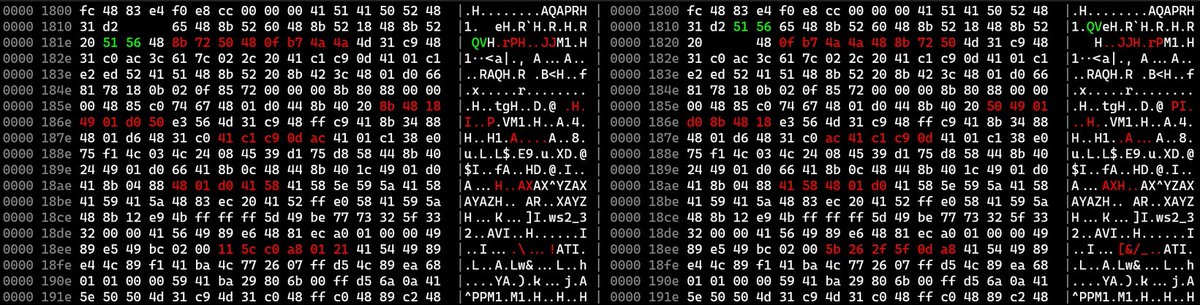
short post introducing `biodiff`, a tool by 8051 enthusiast for diffing binary files, and how you might use it to find malware configuration changes. the UI is really quick and the algorithms handle file alignment very well. williballenthin.com/post/2022-03-0…



vaguely burnt waffle Tyson Key Diadem Salawu Like x86 CPUs booting in real mode, the LLAM (Low Level Actual Machine) will boot in LLVM 1, with higher versions enabled gradually during the boot process





In just 10 minutes, Zhenghao Hu will be presenting IRQDebloat, which automatically reverse engineers interrupt handling on embedded devices so that unwanted peripherals can be disabled! If you're at S&P, be sure to check it out in G.Ballroom A!


Some cool-looking work on vulnerability injection at USENIX Sec by Mike Hicks et al. this year! Looking forward to reading it! usenix.org/conference/use…


About our USENIX Security paper: HTTP/2-to-HTTP/1 conversion anomalies were first looked at by James Kettle and Emil Lerner in the context of Request Smuggling. To take an in-depth look at the conversion anomalies and their security implications, we developed an HTTP/2 (1/3)



Recently Northeastern U. decided to install an IoT surveillance system in our lab that researches the security and privacy of IoT devices. Turns out these devices lack privacy, security, and more importantly good adhesives.



Today, thanks to President Trump’s AI Action Plan, U.S. Commerce Dept. and National Institute of Standards and Technology’s Center for AI Standards and Innovation have released a groundbreaking evaluation of American vs. adversary AI. Result: American AI models dominate. Our systems outperform DeepSeek across nearly every



