Amit Kumar🇮🇳
@amitlt2
Microsoft Q1 Top Researcher 2022 & Secured 100+ Applications | Web, API and Android Pentester | Security Analyst | Philophobia Guy |
ID: 1284258564484108288
https://amit-lt.medium.com 17-07-2020 22:48:12
297 Tweet
437 Takipçi
372 Takip Edilen



🛑 GIVEAWAY ALERT 🛑 Today is DAY TWO of FIVE DAYS of Arcanum Information Security and friends Black Friday and Cyber Monday giveaways! Today we are giving away FIVE seats to our flagship training: "The Bug Hunter's Methodology Live" TBHM is one of the BEST trainings in the industry for







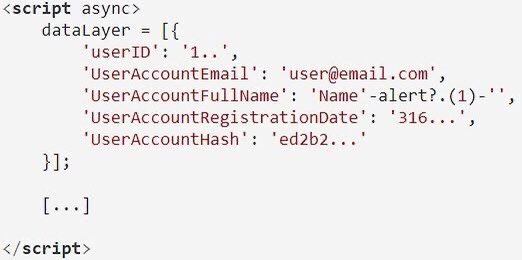
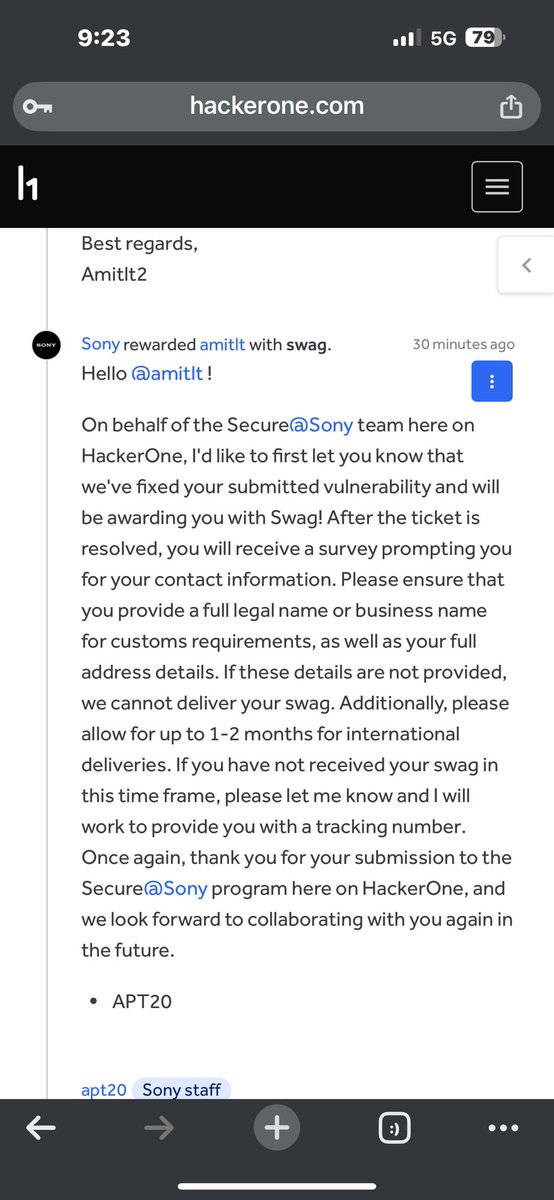
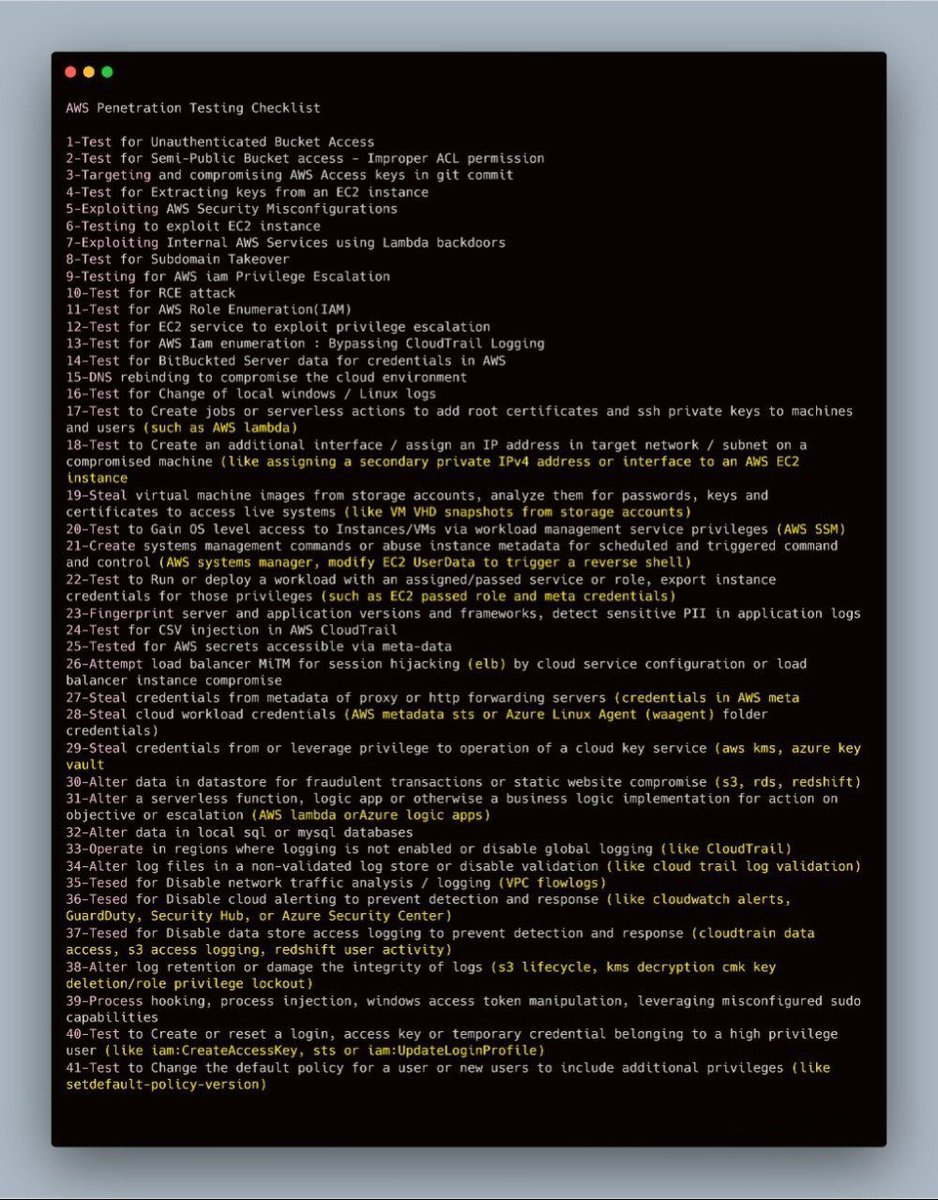
Simple LFI using my path traversal script on GitHub. Used Devansh (⚡, 🥷)’s ParamSpider to gather URLs, filtered for relevant parameters, slightly modified the script to inject payloads into parameters like ?path and ?file, & ran the script — got 1 hit out of 20k+ URLs. The target is







🚨 CVE-2025-55315 (CVSS 9.9) – Critical HTTP Request Smuggling in ASP. NET Kestrel Our Cyber Security Engineer Amit Kumar🇮🇳 discovered & added a severe chunked encoding bypass leading to smuggling to ProjectDiscovery zurl.co/PHSTP #infosec #bugbountytips #bugbounty