Izy
@izysec
Learning to break, working to secure.
ID: 883200352740179968
07-07-2017 05:45:47
475 Tweet
329 Takipçi
352 Takip Edilen

So far I've written 559 pages to help the security community: 1. exploitreversing.com/2021/12/03/mal… 2. exploitreversing.com/2022/02/03/mal… 3. exploitreversing.com/2022/05/05/mal… 4. exploitreversing.com/2022/05/12/mal… 5. exploitreversing.com/2022/09/14/mal… 6. exploitreversing.com/2022/11/24/mal… 7. exploitreversing.com/2023/01/05/mal… 8. exploitreversing.com/2023/04/11/exp…










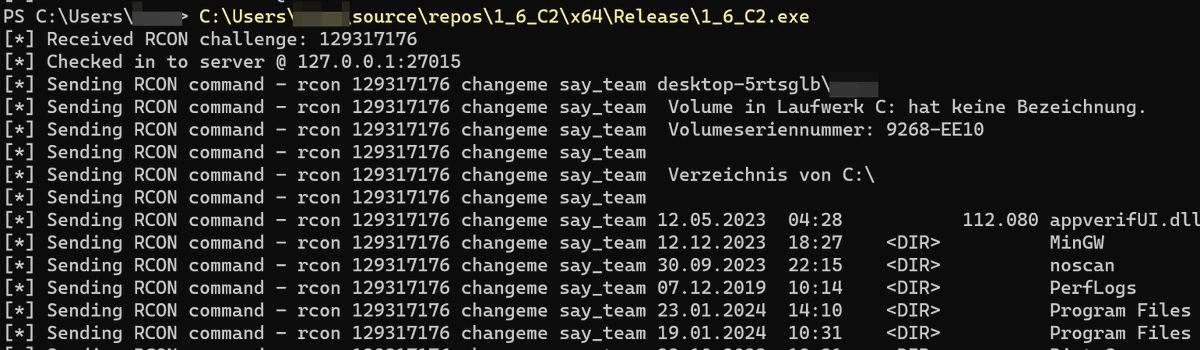
Small experiment today, inspired by Kağan IŞILDAK, using RCON protocol, as used by e.g. CS 1.6 as a C2 channel for the lulz





Having convertible detection content is great, no doubt. What I think is underrated is blueteam-focused tradecraft intel. Red teams share it all the time, we should too. A threat group recently showed creativity with a known technique. Here's how it worked cloud.google.com/blog/topics/th…




![David das Neves (@david_das_neves) on Twitter photo Great overview table of accounts that belong to tier 0. #mustView for every Sec and AD specialist.
[Repo] TierZeroTable
specterops.github.io/TierZeroTable/
#CyberSecurity #Identity #SpecterOps #shiftavenue Great overview table of accounts that belong to tier 0. #mustView for every Sec and AD specialist.
[Repo] TierZeroTable
specterops.github.io/TierZeroTable/
#CyberSecurity #Identity #SpecterOps #shiftavenue](https://pbs.twimg.com/media/F8dpe0sWIAAbzJ5.jpg)