Hannah Schneider
@hschneidertech
Verbindung der digitalen Punkte 🌐
ID: 1723309658583035905
11-11-2023 12:00:15
160 Tweet
7 Takipçi
144 Takip Edilen


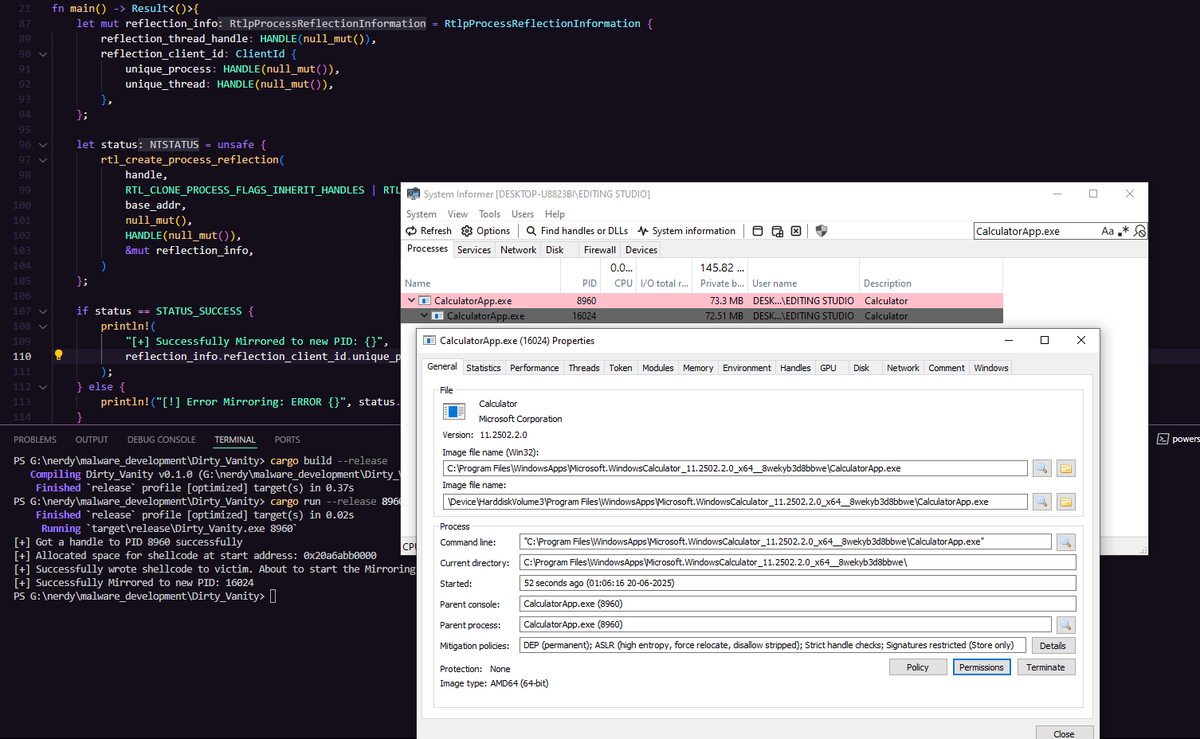
Hunting EDR Freeze... A recent EDR-Freeze technique by Two Seven One Three can suspend a given EDR process. Now it's time to hunt it down with few logs and clever correlation. The post: blog.axelarator.net/hunting-for-ed… #redteam #blueteam #maldev Hunting EDR Freeze... A recent EDR-Freeze



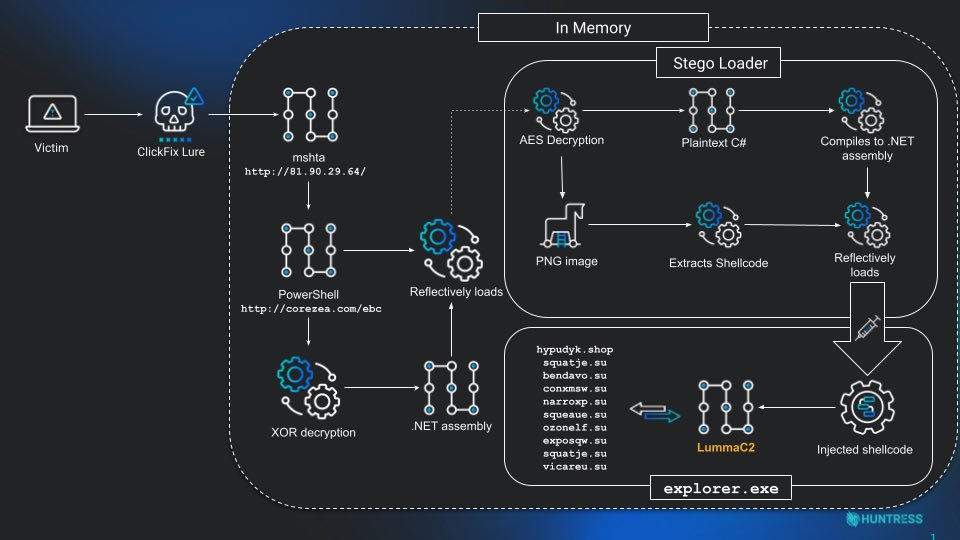
Kaspersky exposed ToddyCat APT's evolution: the group steals M365 OAuth tokens from memory and uses TCSectorCopy to steal locked Outlook OST files, allowing covert access to cloud email outside the perimeter #ToddyCat #M365Hack #Cyberespionage #OAuthToken securityonline.info/toddycat-apt-s…



ICYMI: In this blog, Oddvar Moe goes over a clever DLL hijack that turns Windows Narrator into a persistence vector. Got questions? Our next Discord Livestream is on December 4 where he’ll be answering your questions on Windows Accessibility. Read now! trustedsec.com/blog/hack-cess…













Era from Hack The Box has multiple IDOR vulnerabilities followed by a PHP injection invoking the PHP SSH module to run commands on the host. Then there's a signed Linux binary to negotiate for root. 0xdf.gitlab.io/2025/11/29/htb…