
Hans-Martin Münch
@h0ng10
CEO of MOGWAI LABS GmbH. I play CTF with powerpuffpwn.
ID: 145454720
http://mogwailabs.de 19-05-2010 01:08:44
1,1K Tweet
1,1K Followers
891 Following











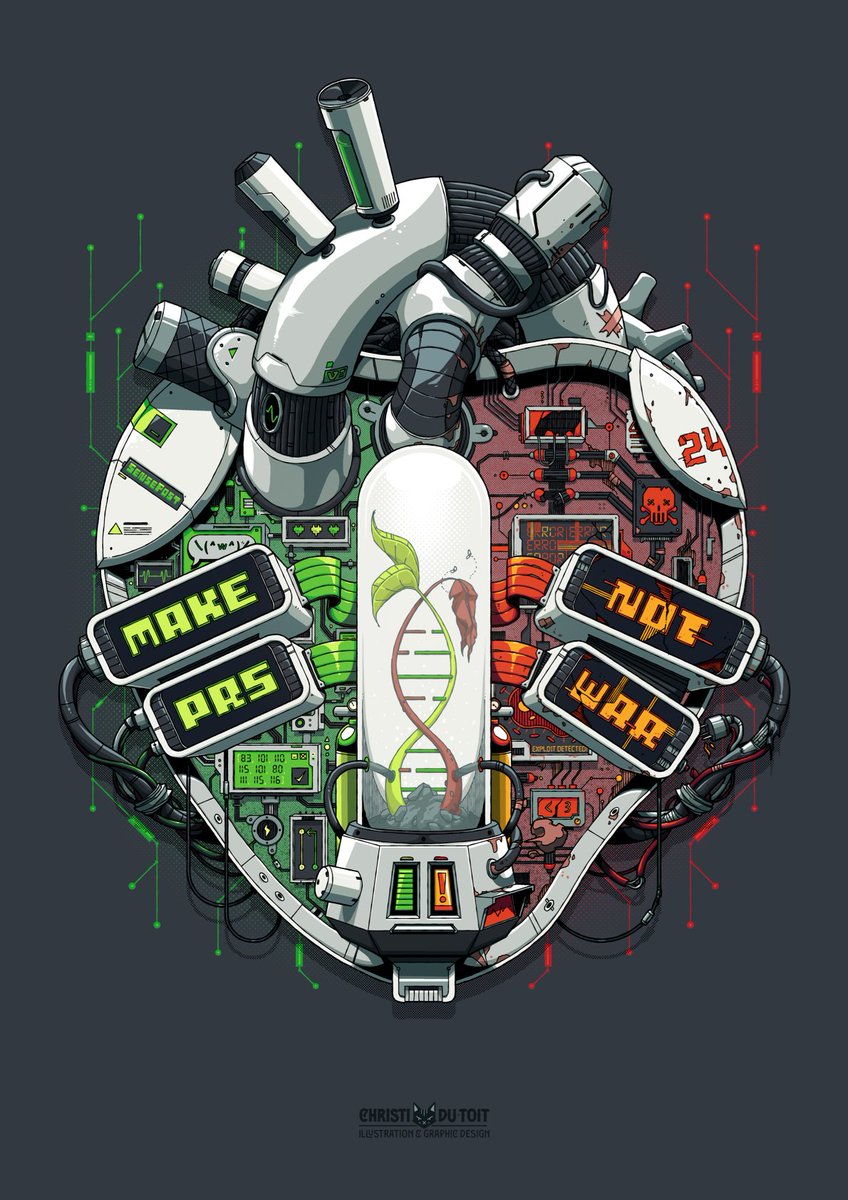
We have a long history of yearly artworks Orange Cyberdefense's SensePost Team, and this year I got to carry the baton forward. I'm excited to reveal our 2024 artwork: "make pr's, not war". An art piece almost literally from my heart. 🧵



Another product, another deserialization vulnerability, another RCE from Markus Wulftange: Patch your Telerik Report Server (CVE-2024-6327 & CVE-2024-6096) code-white.com/public-vulnera…




Happy Monday! watchTowr Labs member SinSinology deep dives into Veeam Backup & Response CVE-2024-40711 in our latest post 🚀 labs.watchtowr.com/veeam-backup-r… We hope you enjoy it! (as always, where there's smoke - there is fire 😉 for next time..)


