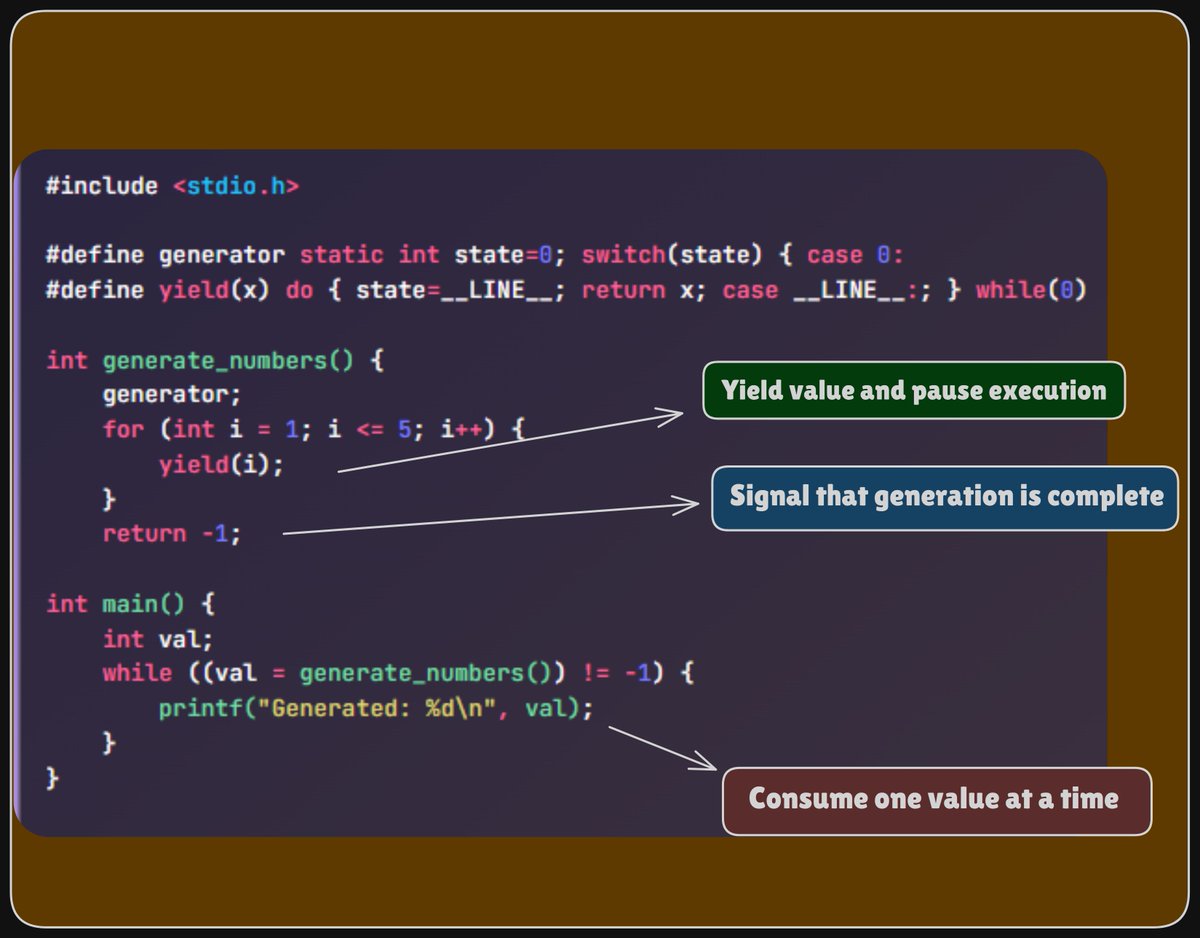
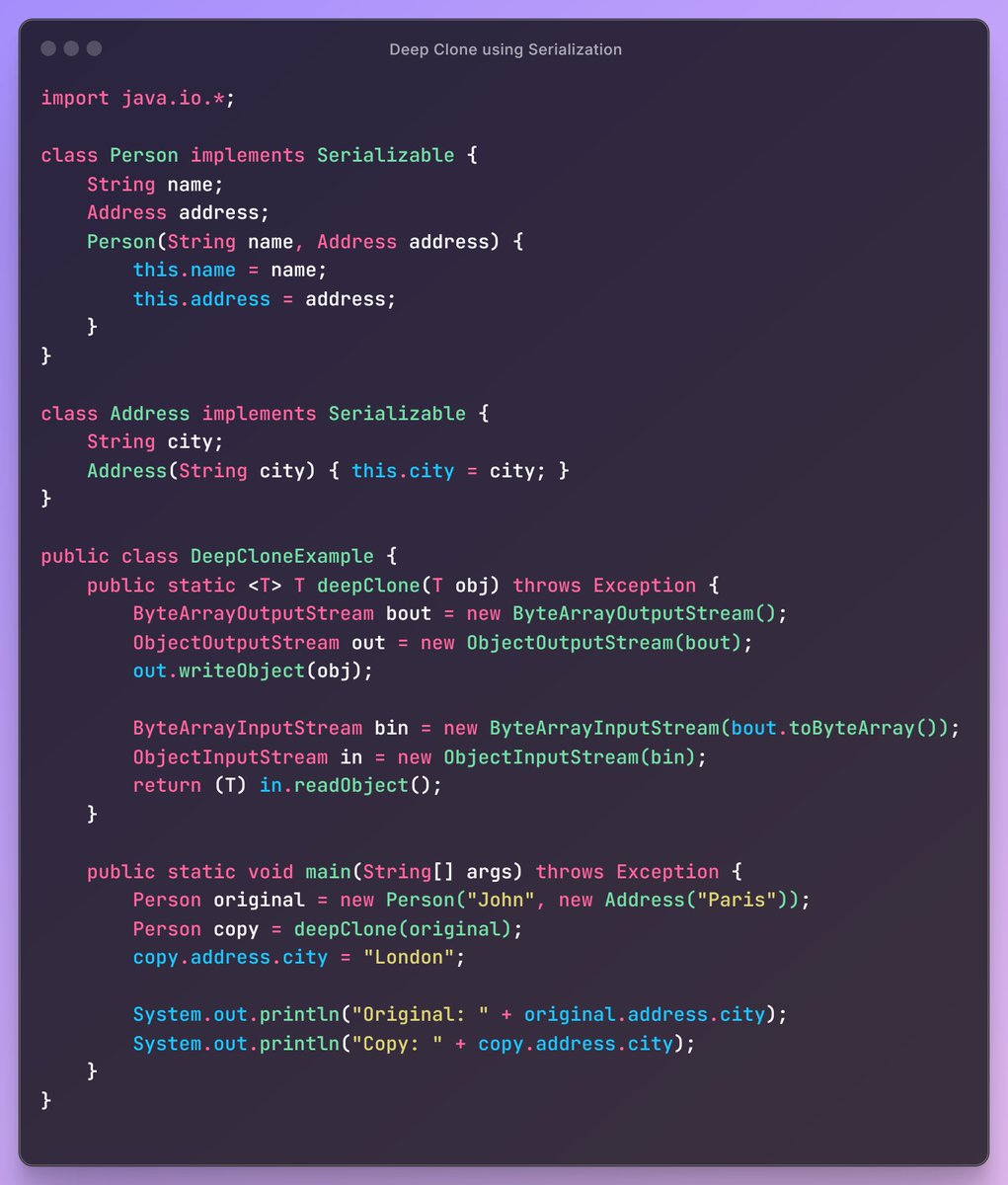
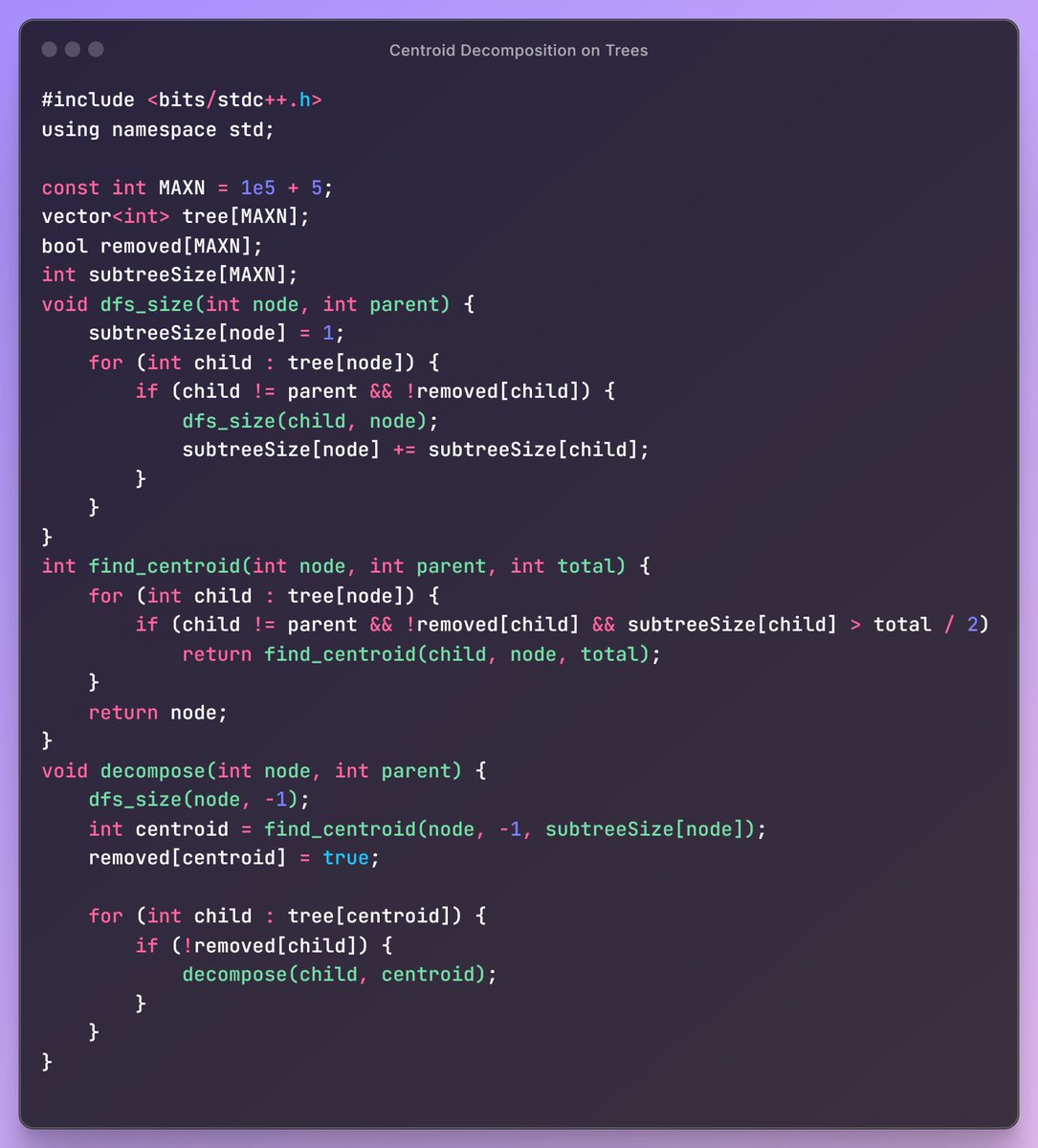
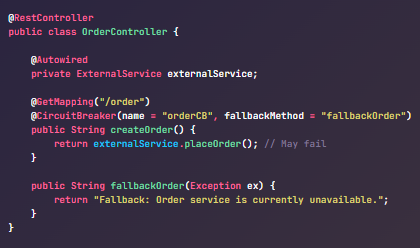
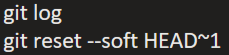
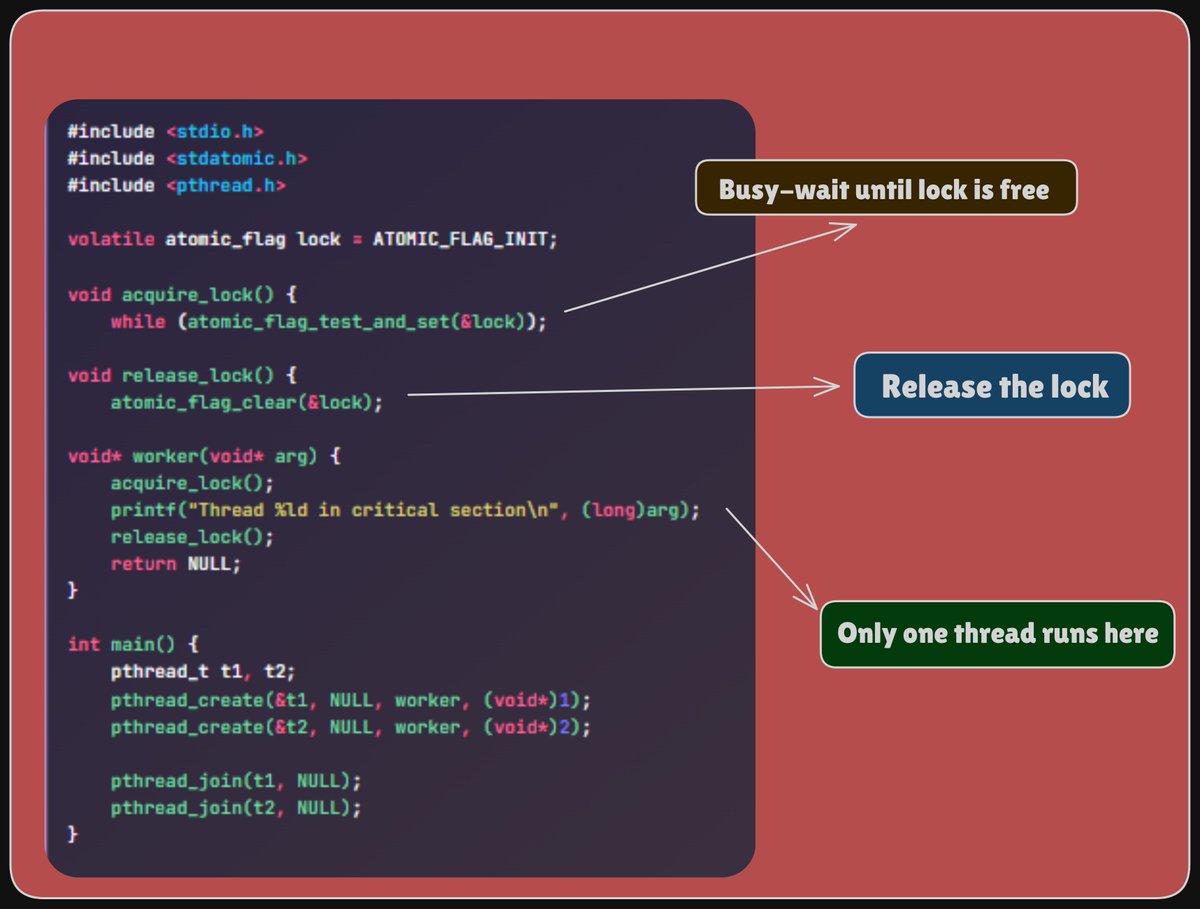
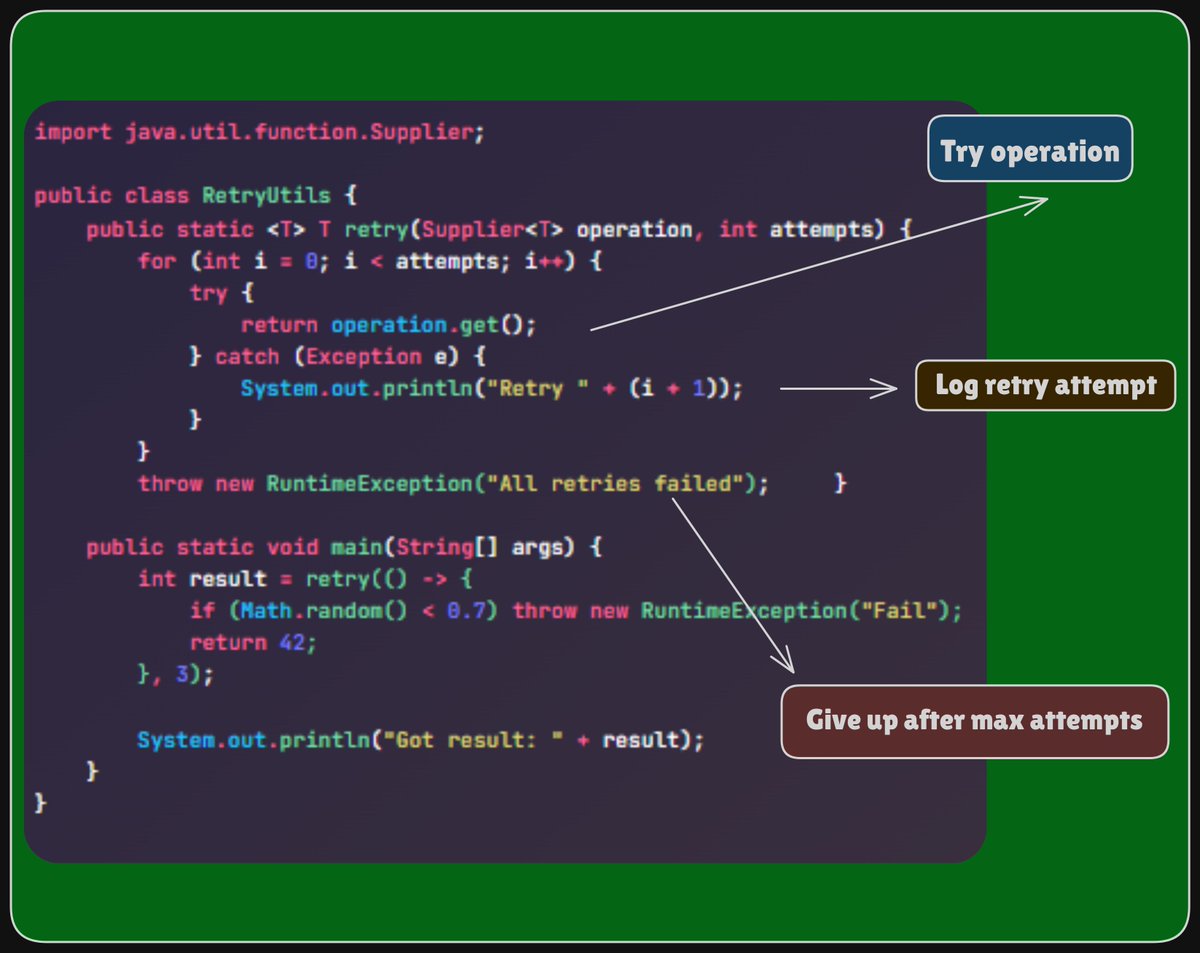
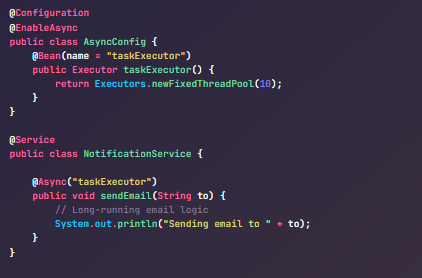
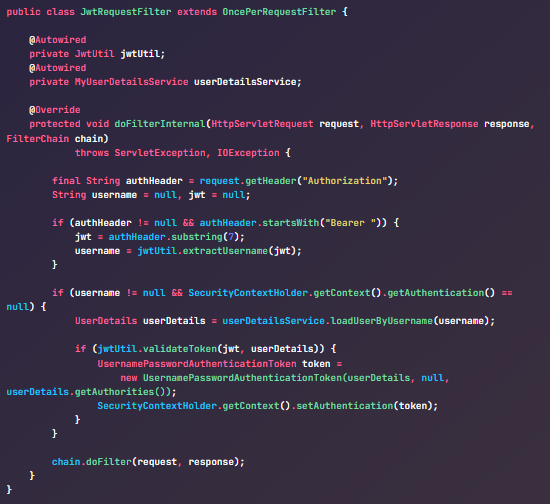
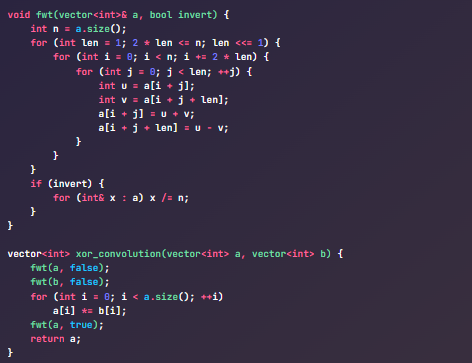
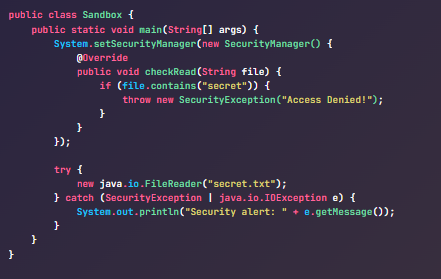
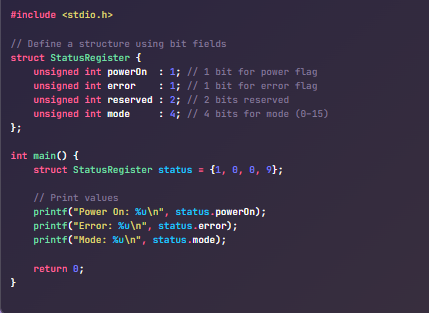
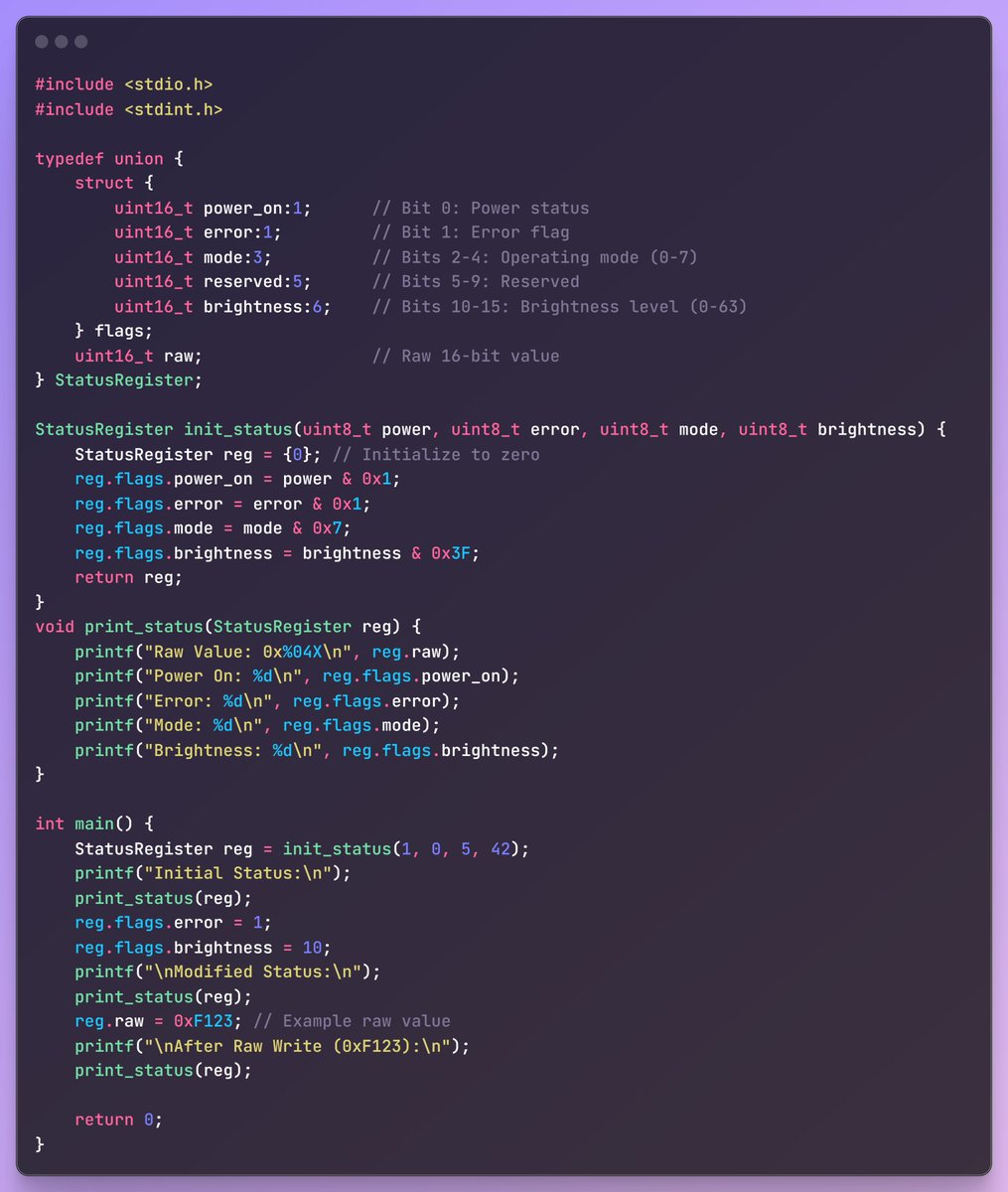
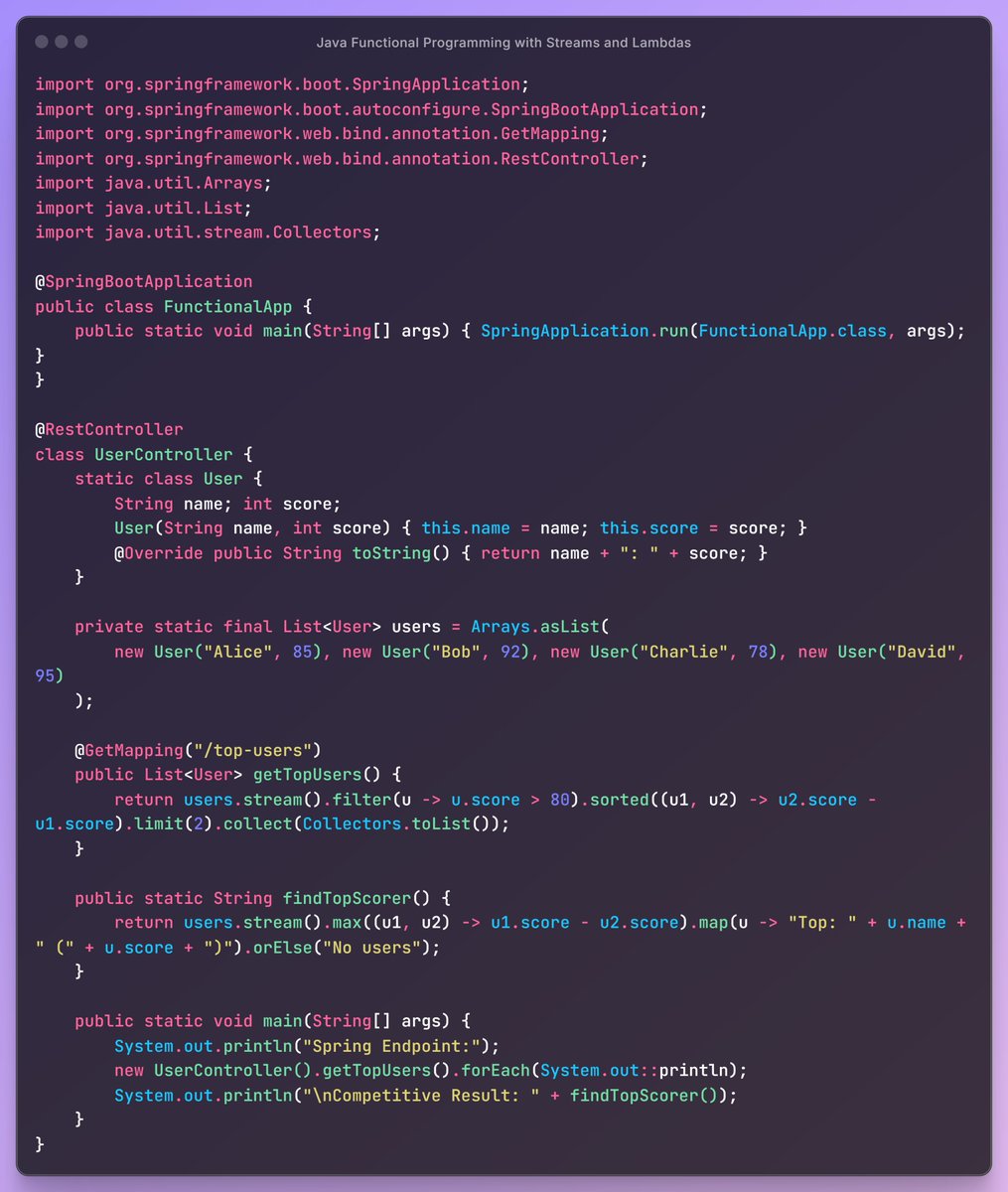
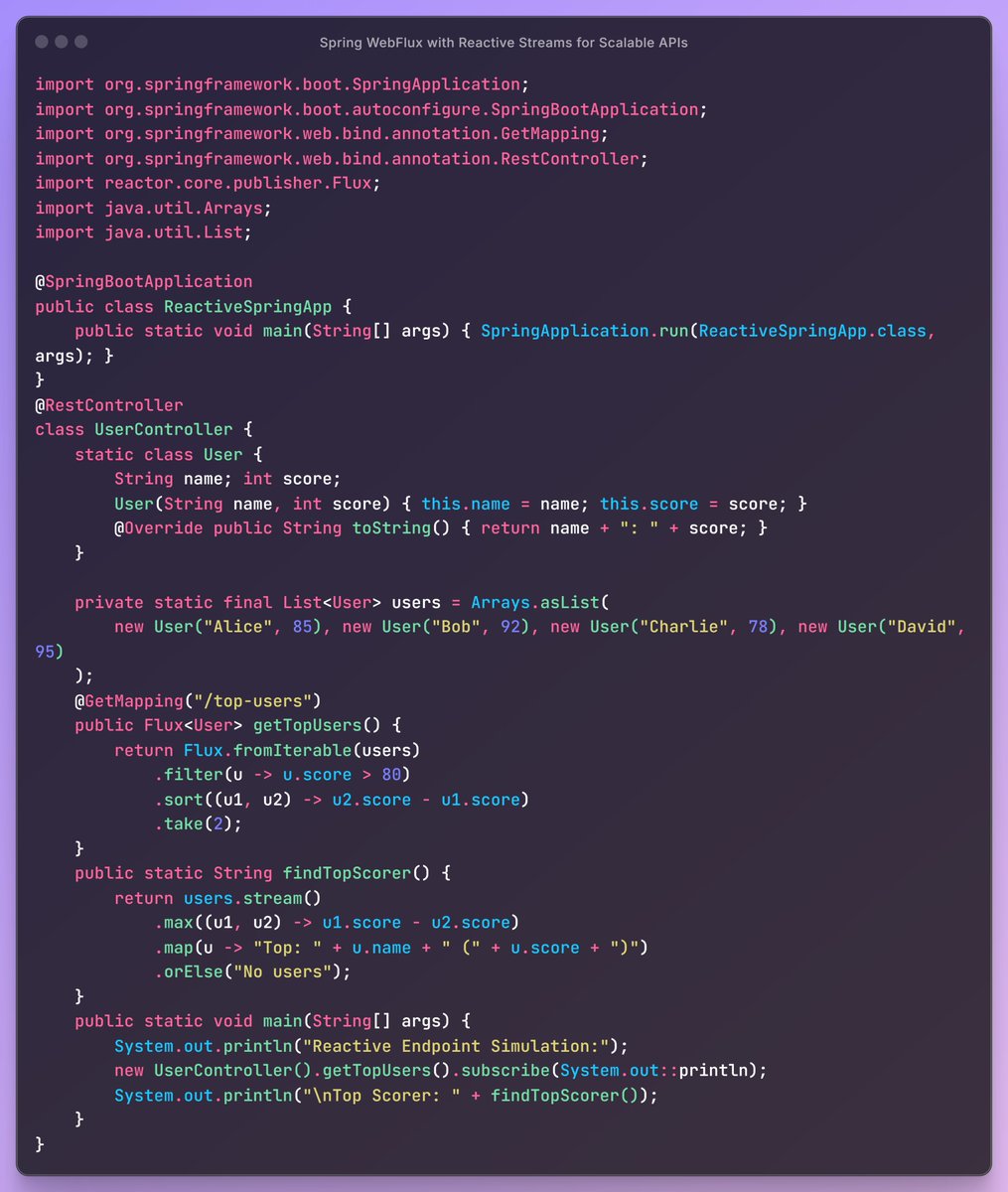
Mahesh
@gutsofdarkness8
Engineering @AmadeusITGroup |
Tech tips and tutorials to help you learn faster, grow stronger, and build great things. Now, let's talk through the content below
ID: 1864316160508088326
https://www.youtube.com/channel/UCfFyrv4xf8541Gi3G2Ip6hw 04-12-2024 14:30:04
320 Tweet
440 Followers
4 Following