ge0lev
@ge0lev
Threat Hunting | Malware Analysis
ID: 1015190309859446785
06-07-2018 11:06:46
34 Tweet
322 Takipçi
361 Takip Edilen


Mom, look! I'm on AnyRun. I want to thank ANY.RUN for this opportunity, as well as all of my friends: Fox_threatintel NDA0E blinkz kddx00 Raghav Rastogi DaveTheResearcher Who said what? ge0lev Simplicio Sam L.


🚨 New Blog: "Analyzing #Tycoon2FA Infra with Validin" Discover how WatchingRac expanded a phishing analysis into ~2k confirmed Storm-1747 domains using Validin's powerful threat-hunting tools. A must-read for analysts hunting advanced phishing kits! validin.com/blog/tycoon_2f…

#Tycoon2FA +287 new domains related to the infrastrucute pastebin.com/GR9fgB39 CC: Fox_threatintel NDA0E blinkz kddx00 Raghav Rastogi DaveTheResearcher Who said what? Dee Mikhail Kasimov ge0lev Simplicio Sam L. JAMESWT_MHT DonPasci


#Tycoon2FA 31 new domains related to the infrastructure pastebin.com/3KQ6bUig CC: Fox_threatintel NDA0E blinkz kddx00 Raghav Rastogi DaveTheResearcher Who said what? Mikhail Kasimov ge0lev Simplicio Sam L. JAMESWT_MHT DonPasci


#Tycoon #Phishing Got more domains with the help of Who said what? 571 domains linked to Tycoon. Here’s a list of domains+subdomains+full path, hosting Outlook/Gmail phishing pages: pastebin.com/jp0uTrK4 A few of them are waiting for API renew (TA's didn't pay the bill 😂)

#Tycoon2FA #Phishing 126 new domains and urls related to Tycoon: pastebin.com/sCzWTCLw CC: Fox_threatintel NDA0E blinkz kddx00 Raghav Rastogi DaveTheResearcher Who said what? Dee Mikhail Kasimov ge0lev Simplicio Sam L. JAMESWT_MHT DonPasci



#Tycoon2FA #Phishing 24 new domains and urls related to Tycoon with low hits on VT: pastebin.com/8CyYQHLT CC: Fox_threatintel NDA0E blinkz kddx00 Raghav Rastogi DaveTheResearcher Who said what? Dee Mikhail Kasimov ge0lev Simplicio Sam L. JAMESWT_MHT DonPasci


#FakeCaptcha 87 Domains hosting FakeCaptcha: pastebin.pl/view/17961bda AnyRun: app.any.run/tasks/a08761bd… app.any.run/tasks/7bbd518a… CC: Fox_threatintel NDA0E blinkz kddx00 Raghav Rastogi DaveTheResearcher Who said what? Dee Mikhail Kasimov ge0lev Simplicio Sam L. JAMESWT_MHT DonPasci


#Tycoon Updates: -> New Captcha (IconCaptcha) -> Currently Using .es, .ru, .com, .info, .org TLD's New Domains: pastebin.com/mW4tZnf7 CC: Fox_threatintel NDA0E blinkz kddx00 Raghav Rastogi DaveTheResearcher Who said what? Dee Mikhail Kasimov ge0lev Simplicio Sam L. JAMESWT_MHT


#Phishing My first bot will focus on phishing domains! CC: Fox_threatintel NDA0E blinkz kddx00 Raghav Rastogi DaveTheResearcher Who said what? Dee Mikhail Kasimov ge0lev Simplicio Sam L. JAMESWT_MHT DonPasci

🚨After a long time, I finally created a GitHub repo containing the domains discovered by the bot: github.com/NoMorePhish/Ty… CC: Fox_threatintel NDA0E blinkz kddx00 Raghav Rastogi DaveTheResearcher Who said what? Dee Mikhail Kasimov ge0lev Simplicio Sam L. JAMESWT_MHT DonPasci


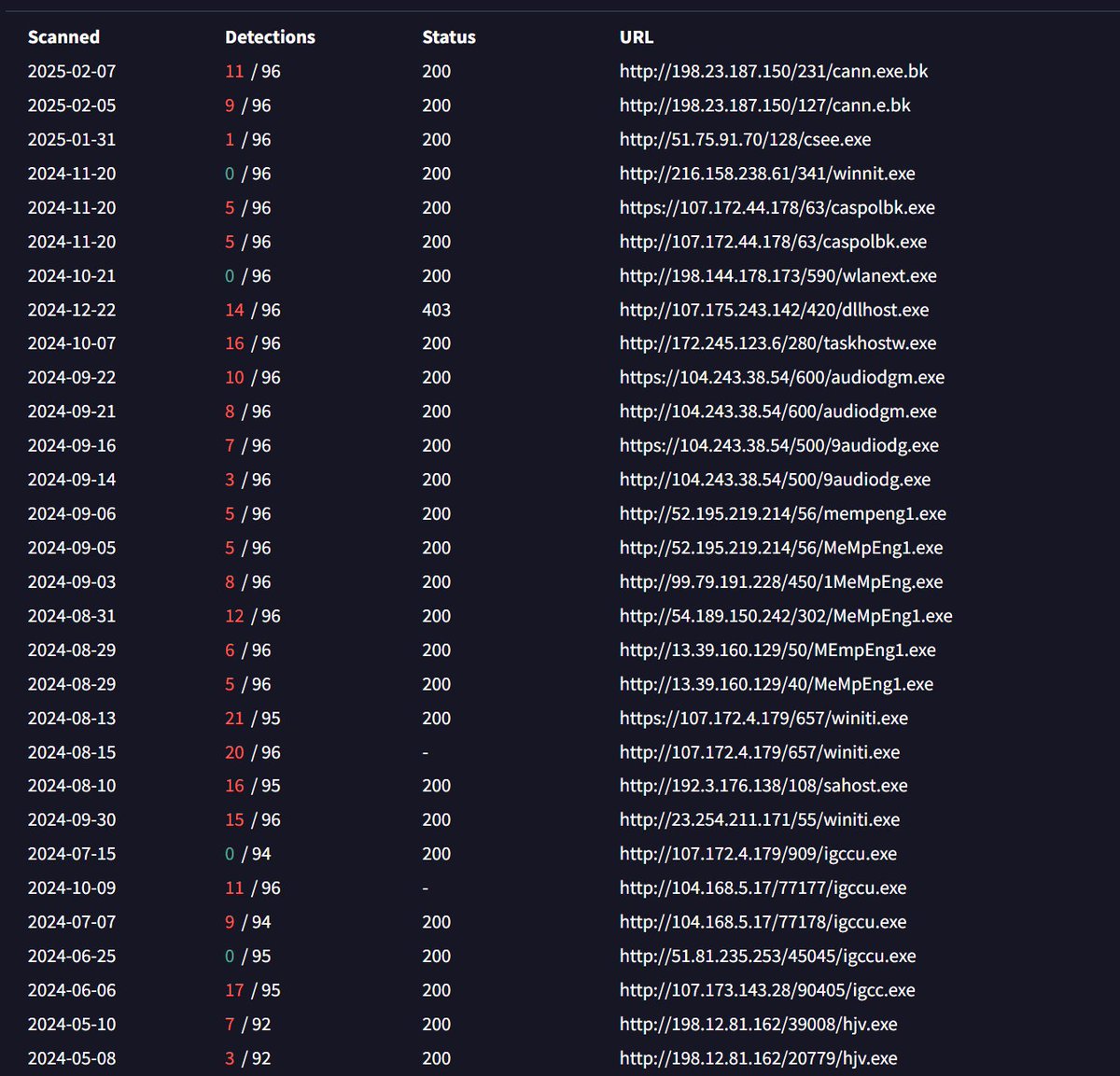
#Lumma #Malware 👾 32 domains related to Lumma: pastebin.com/0RhLL7Uf CC: Fox_threatintel NDA0E blinkz kddx00 Raghav Rastogi DaveTheResearcher Who said what? Dee Mikhail Kasimov ge0lev Simplicio Sam L. JAMESWT_MHT DonPasci
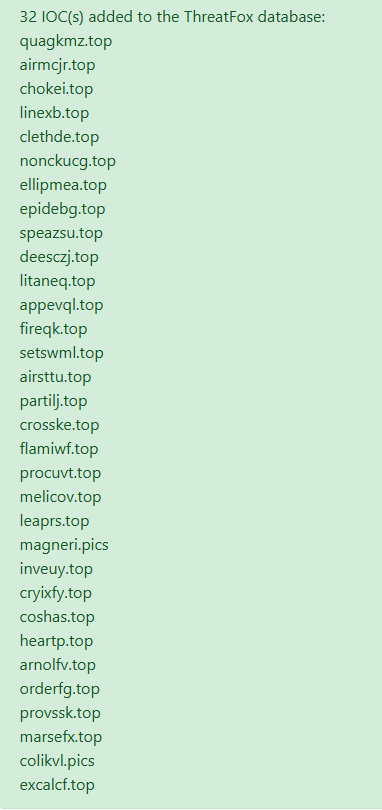

#Lumma #Malware 👾 37 domains related to Lumma: pastebin.com/39PPLg4L CC: Fox_threatintel NDA0E blinkz kddx00 Raghav Rastogi DaveTheResearcher Who said what? Dee Mikhail Kasimov ge0lev Simplicio Sam L. JAMESWT_MHT DonPasci


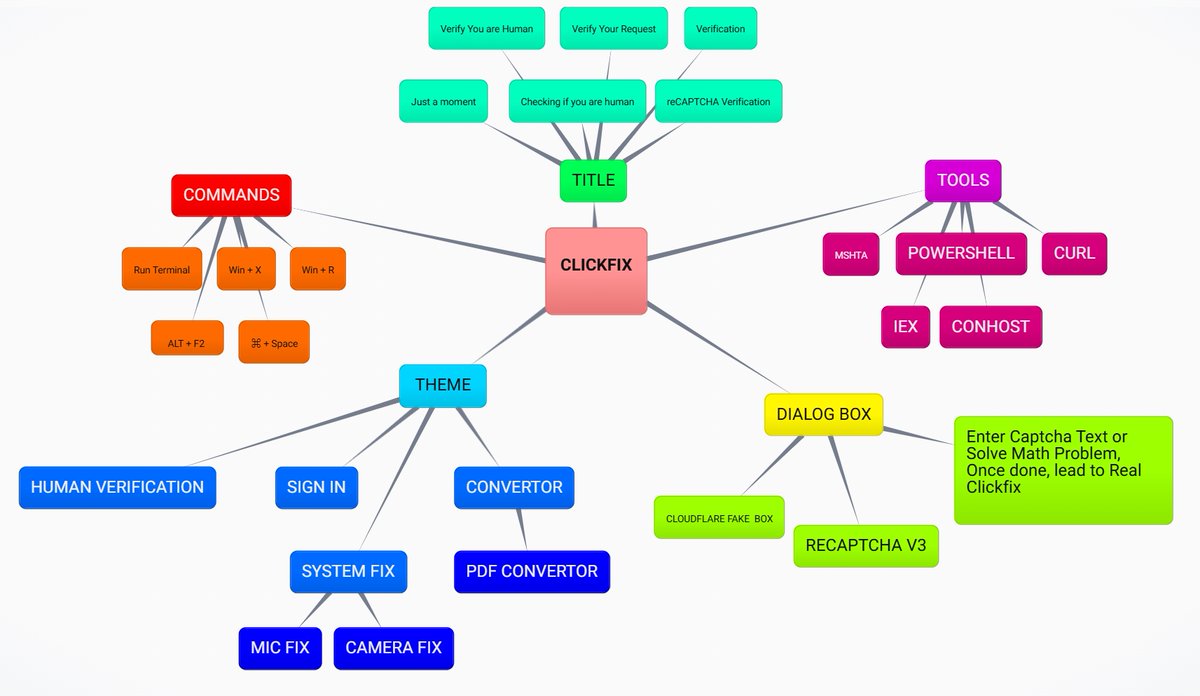
#Tycoon2FA #Phishing - Using new TLD ([.]co[.]za) - New Anti-Bot System (never saw something like that) CC: Fox_threatintel NDA0E blinkz kddx00 Raghav Rastogi DaveTheResearcher Who said what? Dee Mikhail Kasimov ge0lev Simplicio Sam L. JAMESWT_MHT DonPasci
![WatchingRac (@racwatchin8872) on Twitter photo #Tycoon2FA #Phishing
- Using new TLD ([.]co[.]za)
- New Anti-Bot System (never saw something like that)
CC:
<a href="/banthisguy9349/">Fox_threatintel</a>
<a href="/NDA0E/">NDA0E</a>
<a href="/BlinkzSec/">blinkz</a>
<a href="/kddx0178318/">kddx00</a>
<a href="/raghav127001/">Raghav Rastogi</a>
<a href="/DaveLikesMalwre/">DaveTheResearcher</a>
<a href="/g0njxa/">Who said what?</a>
<a href="/ViriBack/">Dee</a>
<a href="/500mk500/">Mikhail Kasimov</a>
<a href="/ge0lev/">ge0lev</a>
<a href="/marsomx_/">Simplicio Sam L.</a>
<a href="/JAMESWT_MHT/">JAMESWT_MHT</a>
<a href="/DonPasci/">DonPasci</a> #Tycoon2FA #Phishing
- Using new TLD ([.]co[.]za)
- New Anti-Bot System (never saw something like that)
CC:
<a href="/banthisguy9349/">Fox_threatintel</a>
<a href="/NDA0E/">NDA0E</a>
<a href="/BlinkzSec/">blinkz</a>
<a href="/kddx0178318/">kddx00</a>
<a href="/raghav127001/">Raghav Rastogi</a>
<a href="/DaveLikesMalwre/">DaveTheResearcher</a>
<a href="/g0njxa/">Who said what?</a>
<a href="/ViriBack/">Dee</a>
<a href="/500mk500/">Mikhail Kasimov</a>
<a href="/ge0lev/">ge0lev</a>
<a href="/marsomx_/">Simplicio Sam L.</a>
<a href="/JAMESWT_MHT/">JAMESWT_MHT</a>
<a href="/DonPasci/">DonPasci</a>](https://pbs.twimg.com/media/G1SqMdVWYAAwKKq.png)

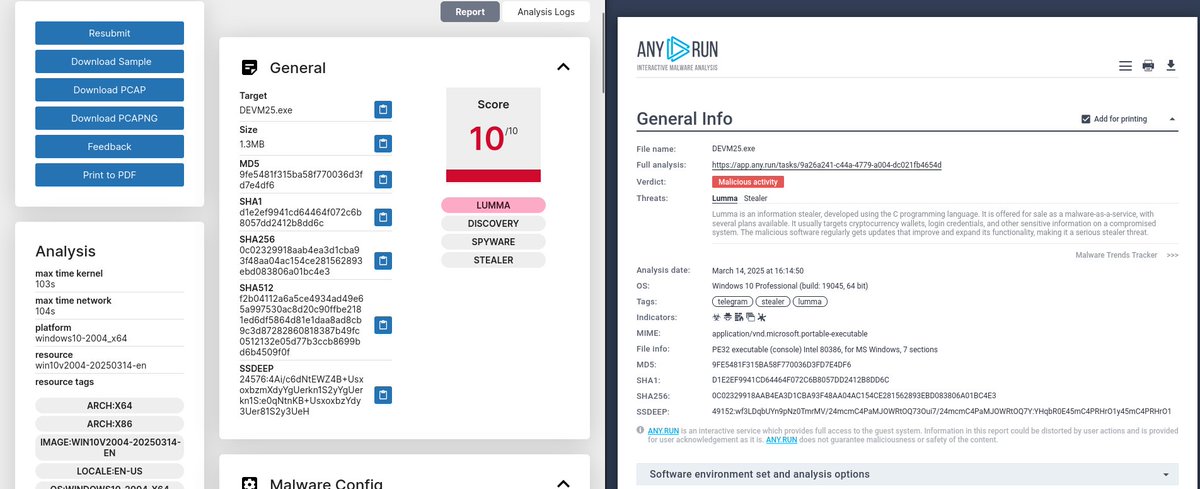
#Stealc #Malware 🚨40 IP's with Low Hits on VT related to Stealc🚨 pastebin.com/u7SVaBGv CC: Fox_threatintel NDA0E blinkz kddx00 Raghav Rastogi DaveTheResearcher Who said what? Dee Mikhail Kasimov ge0lev Simplicio Sam L. JAMESWT_MHT DonPasci

![WatchingRac (@racwatchin8872) on Twitter photo #AsyncRat #Malware
💣holder-apartments-face-matthew[.]trycloudflare[.]com/uline/Nr-2005-028763-2024-PDF[.]lnk💣
lnk->vbs->bat (checks if Avast exists) -> zip -> python scripts (injects shellcode) -> AsyncRat
app.any.run/tasks/0a336523…
app.any.run/tasks/13911dd7… #AsyncRat #Malware
💣holder-apartments-face-matthew[.]trycloudflare[.]com/uline/Nr-2005-028763-2024-PDF[.]lnk💣
lnk->vbs->bat (checks if Avast exists) -> zip -> python scripts (injects shellcode) -> AsyncRat
app.any.run/tasks/0a336523…
app.any.run/tasks/13911dd7…](https://pbs.twimg.com/media/GdFO8TuXIAEJffo.png)