
finbat
@finbat3
ID: 1079158155681165312
29-12-2018 23:32:08
60 Tweet
45 Followers
588 Following

Xmas is a time for gift-giving🎁 Join our #ChristmasGiveaway 🎄3 books of Practical Malware Analysis signed by the author Michael Sikorski 🎄1 month of Searcher 🎄1 month of Hunter Rules are simple: follow us and share this post. On 25th December, we’ll announce 5 winners. Good luck!



I’m going to randomly pick 3 people who retweet this to receive a copy of the book. I’ll tweet out the winners tomorrow. I’ll also be giving away two more copies later this week complements of Ray [REDACTED]! …and maybe a couple more next week just for university students
![Stephen Sims (@steph3nsims) on Twitter photo I’m going to randomly pick 3 people who retweet this to receive a copy of the book. I’ll tweet out the winners tomorrow. I’ll also be giving away two more copies later this week complements of <a href="/RayRedacted/">Ray [REDACTED]</a>! …and maybe a couple more next week just for university students I’m going to randomly pick 3 people who retweet this to receive a copy of the book. I’ll tweet out the winners tomorrow. I’ll also be giving away two more copies later this week complements of <a href="/RayRedacted/">Ray [REDACTED]</a>! …and maybe a couple more next week just for university students](https://pbs.twimg.com/media/FNSV6beVcAU4yrZ.jpg)


Giveaway time! We are going to send a t-shirt and few goodies to one person who follows PentesterLab and likes this tweet !! And we are going to give a 1-year voucher to someone who RT this tweet!

It's been a while since our last discount, so time for another! Until June 20th you can grab the Zero2Automated course for 15% off, using code "BAZAR", giving you lifetime access to all 25+ hours of course content, the course discord community, and more! courses.zero2auto.com/?coupon=BAZAR




Follina Exploit Leads to Domain Compromise ➡️Initial Access: Word Doc exploiting Follina ➡️Persistence: Scheduled Tasks ➡️Discovery: ADFind, Netscan, etc. ➡️Lat Movement: SMB, Service Creation, RDP ➡️C2: #CobaltStrike, Qbot, NetSupport, Atera/Splashtop thedfirreport.com/2022/10/31/fol…



⭐️GIVEAWAY!⭐️ I'm giving away 10 digital copies of Digital Forensics and Incident Response, 3rd Edition by GERARD JOHANSEN Packt Publishing Winners will be announced Friday, @ 12pm EST 🥳 Enter by liking, sharing, and commenting 😊



Malicious ISO File Leads to Domain Wide Ransomware ➡️Initial Access: IcedID ISO ➡️Credentials: DCsync ➡️PrivEsc: ZeroLogon ➡️Lateral: RDP, SMB/Remote Service, WMI ➡️C2: IcedID, Cobalt Strike, Anydesk ➡️Exfil: Rclone to Mega ➡️Impact: Quantum Ransomware thedfirreport.com/2023/04/03/mal…





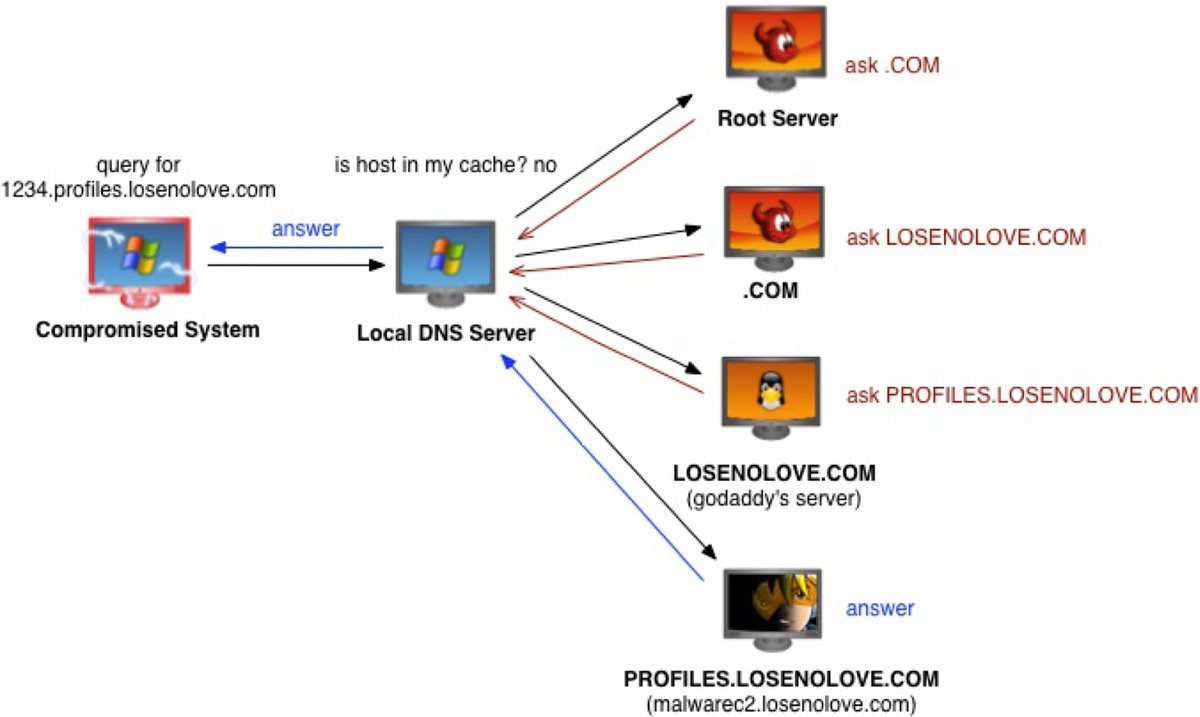

![Matthew (@embee_research) on Twitter photo A quick demo of how to identify "real" exported functions from a #obfuscated #IcedID dll file.
I'll also briefly touch on some #Ghidra tips, and how to extract #shellcode using a debugger.
A moderate sized thread😃
[1/13] A quick demo of how to identify "real" exported functions from a #obfuscated #IcedID dll file.
I'll also briefly touch on some #Ghidra tips, and how to extract #shellcode using a debugger.
A moderate sized thread😃
[1/13]](https://pbs.twimg.com/media/Fdfy4c1VEAAweWl.png)
