EXPMON
@expmon_
Advanced sandbox-based system specifically designed and built for detecting file-based zero-day and hard-to-detect exploits. By @HaifeiLi.
ID: 1431684298705408001
https://pub.expmon.com 28-08-2021 18:28:44
53 Tweet
1,1K Followers
67 Following








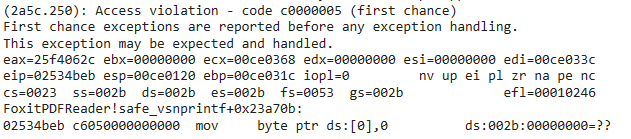
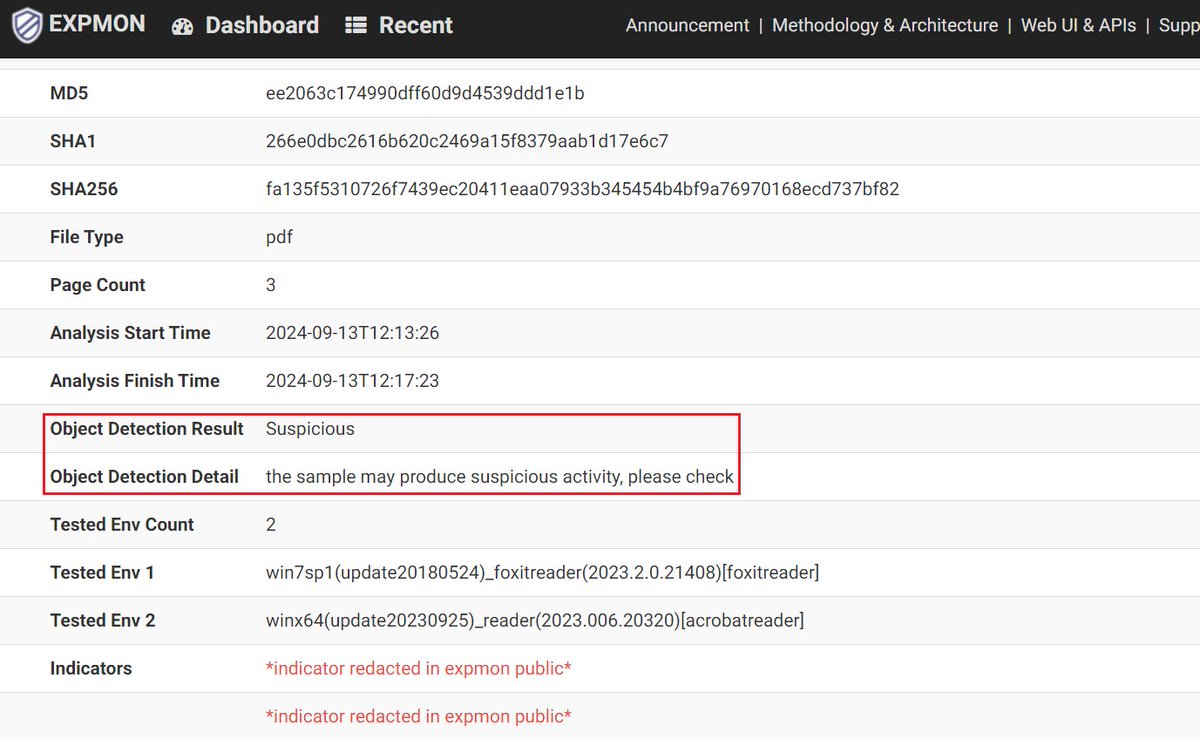
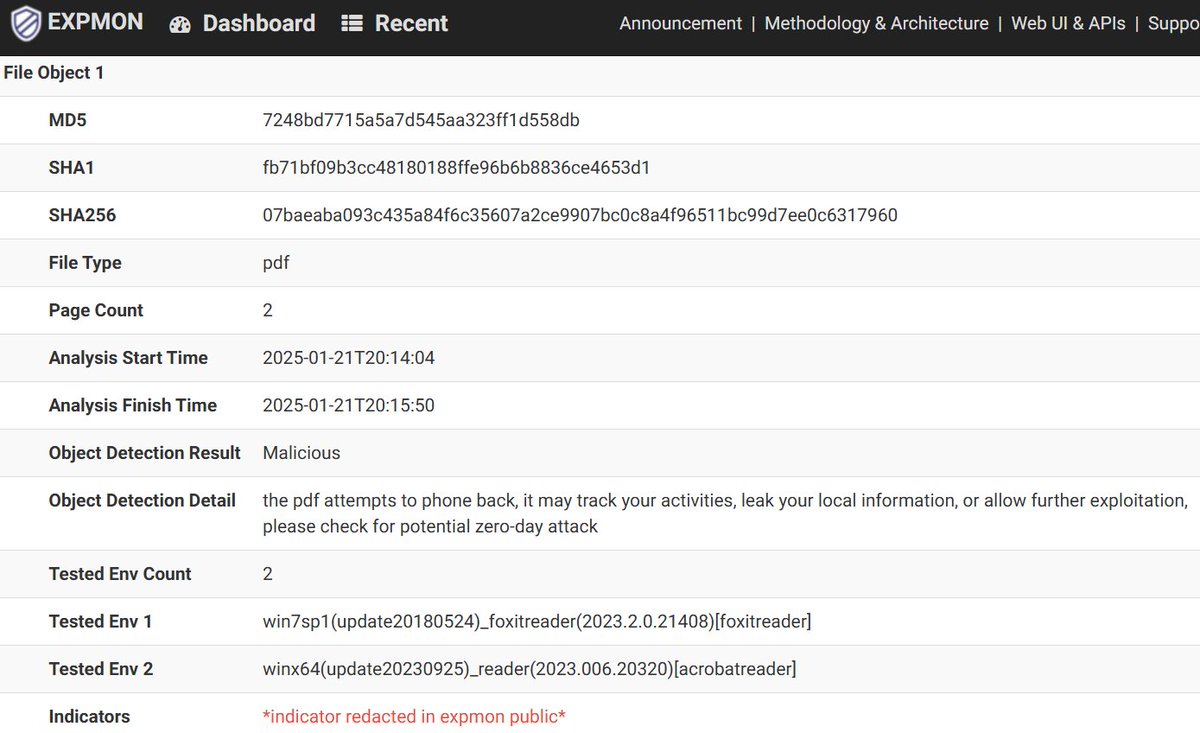
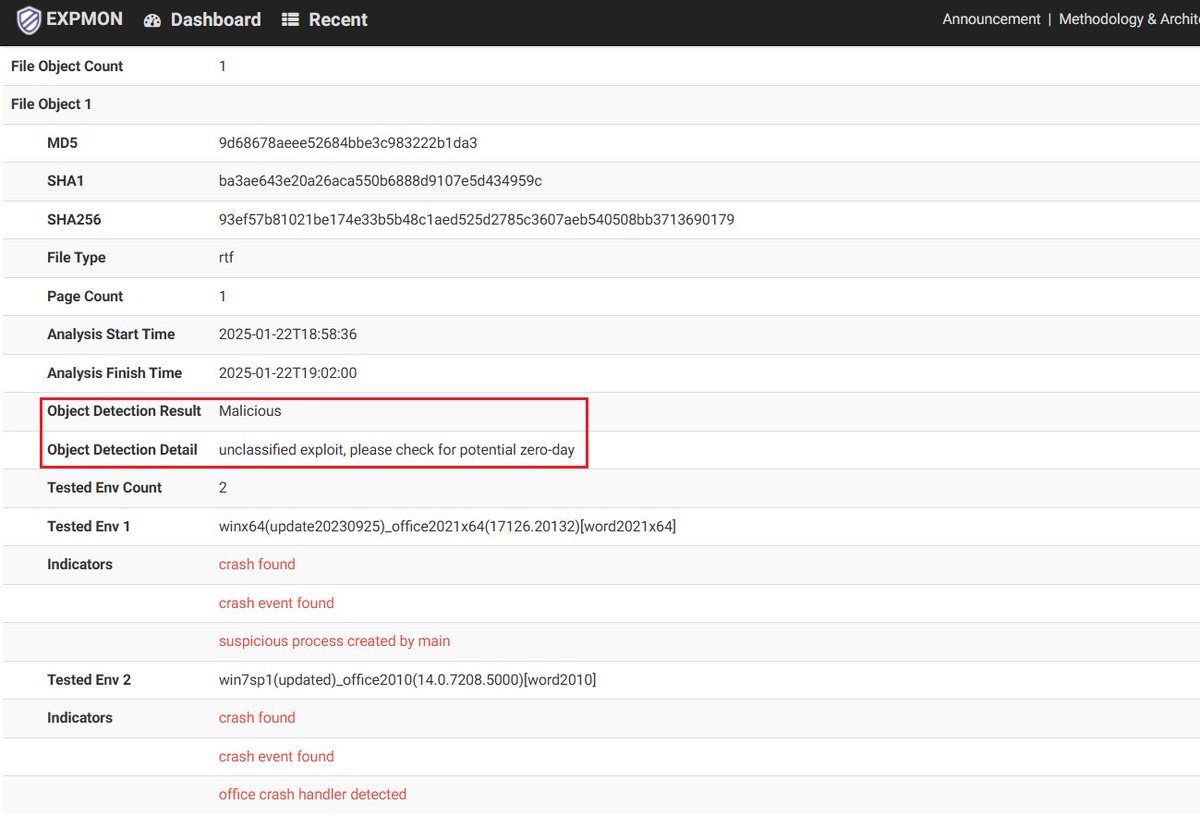
In December, there was a sample uploaded to EXPMON Public (pub.expmon.com/analysis/18899…). I just took some night time analyzing it manually and found that it's likely to be a WPS Office (previous) zero-day sample discussed at welivesecurity.com/en/eset-resear…. Please note that the public