
Erye Hernandez
@eryeh
Security Researcher, @inicmu alum, gamer, snowboarder, weekend baker, PPP member
ID: 22731987
04-03-2009 04:15:02
305 Tweet
1,1K Takipçi
451 Takip Edilen







0day privilege escalation for macOS Catalina discovered in the wild by Erye Hernandez support.apple.com/en-us/HT212825 We saw this used in conjunction with a N-day remote code execution targeting webkit. Thanks to Apple for getting patch out so quickly.


Google uncovered a sophisticated attack that leveraged both iOS & macOS exploits (n-/0-days) to infect Apple users! 👀 Interested in a triage of the macOS implant (named OSX.CDDS), including: ▫️ Installation ▫️ Persistence ▫️ Capabilities 📝 Have a read: objective-see.com/blog/blog_0x69…


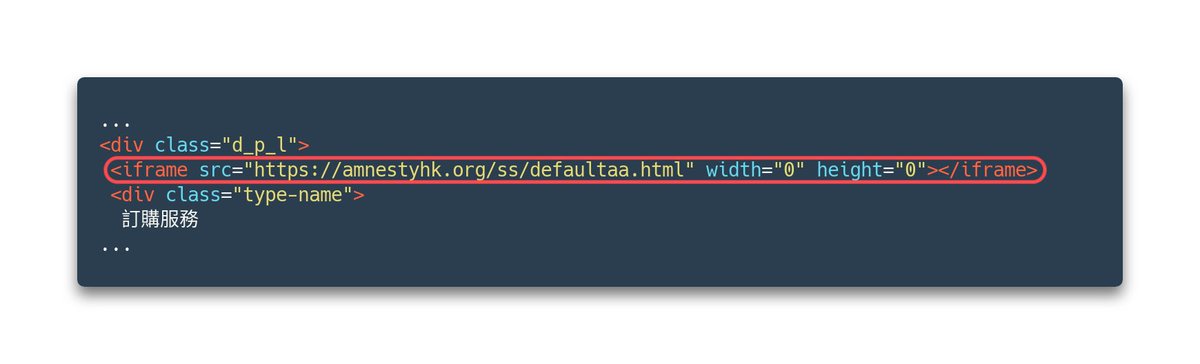
More technical details from Erye Hernandez and the team on last months exploit and the associated campaign. blog.google/threat-analysi… TAG discovered watering hole attacks targeting visitors to Hong Kong websites for a media outlet and a prominent pro-democracy labor and political group.

#ESETresearch uncovers new Mac malware DazzleSpy, delivered using watering hole on a pro-democracy Hong Kong radio station website. Payload was launched as root without user interaction, using exploits for Safari and macOS. Marc-Etienne M.Léveillé Anton Cherepanov welivesecurity.com/2022/01/25/wat… 1/7



#oneisntenough have you registered? Wicked6Games KATZCY @CyberRiskLady Skelly DrReem Faraj AlShammari Mansi Erye Hernandez Women's Cyberjutsu Ann Johnson

Session 1 speakers are set for today's Wicked6games, don't miss your chance to register: hubs.li/Q016B3TH0 DrReem Faraj AlShammari|THE Mari Galloway | Cyberjutsu | International|julie agnes 🌈|Erye Hernandez|Asuka Nakajima | 中島明日香



MMM takes 1st at DEF CON CTF! Had a great time playing with our friends Maple Bacon and Theori as Maple Mallard Magistrates! 🍁🦆🗝 Great job to Katzebin, StarBugs, and all the other teams! And thanks to Nautilus Institute for organizing!



