Security Engineer at @zellic_io, a.k.a vakzz when doing bug bounties and CTFs with @pb_ctf - devcraft.io
ID: 1586550266
https://wbowling.info/ 11-07-2013 18:51:33
213 Tweet
6,6K Followers
412 Following






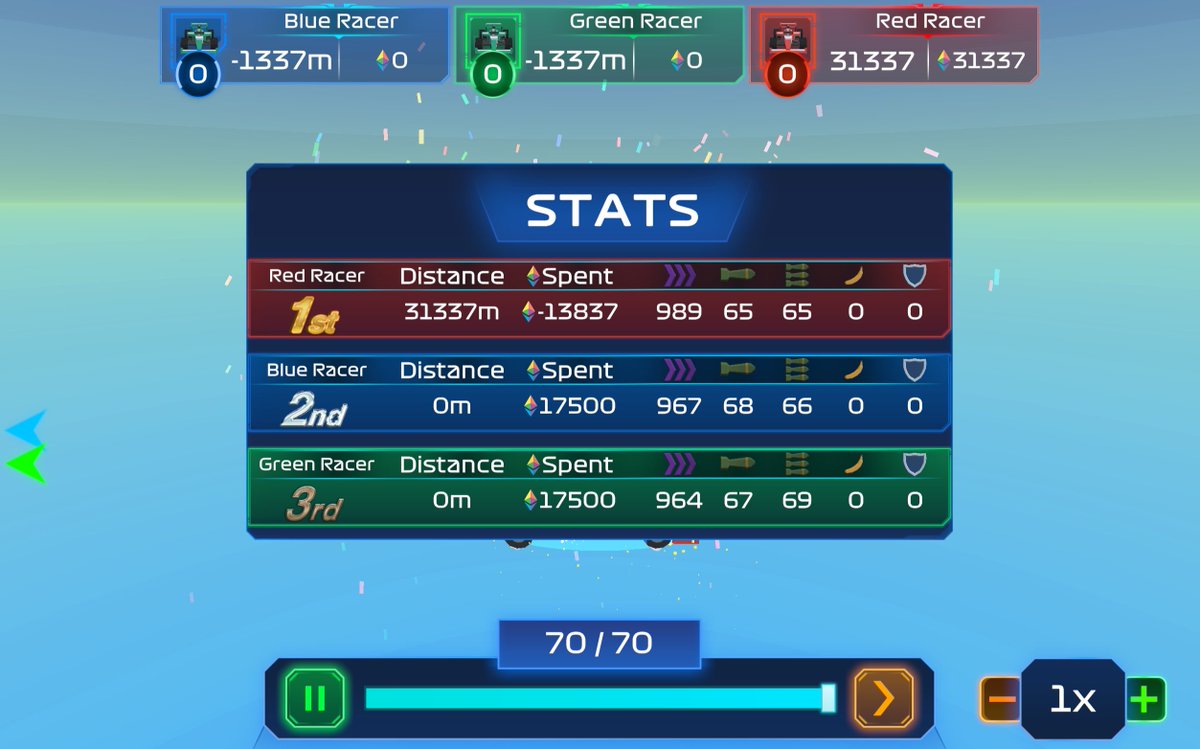
This weekend, we played 0xmonaco MatchboxDAO, a web3 gaming competition. We developed a highly profitable racing strategy by leveraging clever math and bugs. We got DQ-ed😅 In this thread, we'll break down: 🎯 our car's unique strategy 🎯 the vulnerabilities our car exploited





The dangers of integer truncation: How the Zellic team found a critical vulnerability in the Astar Network. This bug allowed an attacker to drain certain LP contracts on the Astar-EVM, with no bugs required in the contracts. Read more: 🧵👇


2023 was another great year for the team! 🎉 Blue Water, a collab between perfect blue and Water Paddler, placed 1st in CTFtime globally!🏆 🥇1st place in 6 CTFs 💻Hosted a successful pbctf 2023 In the past, we also placed first in 2020 and 2021.✌ Looking forward to 2024!🎆




✨ Our judges also decided to give a special mention to William Bowling @[email protected] for his submission in which the bug allows a `multisig` storage variable to be overwritten, allowing the `emergencyWithdraw` function to be called by an attacker. Read Patrick Collins’s thoughts on this










