
Dzmitry Lukyanenko
@vulnano
ID: 984040401735770121
http://www.vulnano.com 11-04-2018 12:08:09
107 Tweet
1,1K Followers
102 Following






Hackerone steals from researchers based on nationality, using sanctions as pretense. Proof that their executive team (Mårten Mickos Michiel Prins) publicly lied about sanctions when there are none (confirmed by OFAC)






Last days I've spent on Meta's BountyCon event hosted in Seoul, Korea. Together with my teammates(Philippe Harewood, Youssef Sammouda (sam0) and Josip Franjković ) we took 1-2 places and won 5/7 nominations. Also special thanks from me for event collaboration with Sergey Toshin & Oversecured scanner.


📸Dzmitry Lukyanenka Dzmitry Lukyanenko is a full-time White Hat from Belarus with 8 years of experience. He thinks White Hats are independent, curious, ethical, patient, and inventive. Let's get to learn from him: security.tecno.com/SRC/blogdetail… #hack #infosec #bugbounty #AppSec #websecurity




Thanks Meta Facebook Security for event and my colleagues Philippe Harewood , Josip Franjković , Youssef Sammouda (sam0) with my other Facebook researcher friends for support)
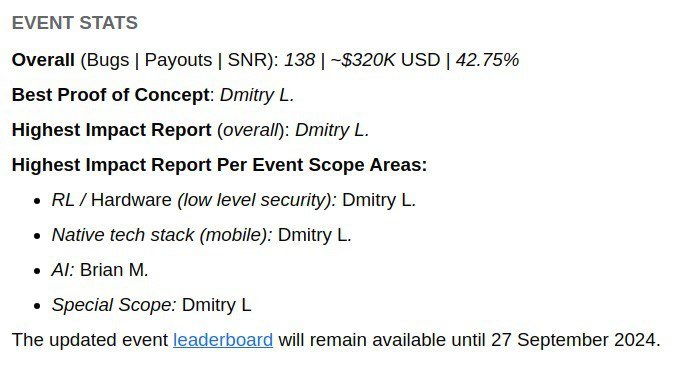

Alhamdulillah, $250,000 in total with bonuses for this bug, another record broken. Many thanks to Meta and the Yes Team Philippe Harewood Josip Franjković Dzmitry Lukyanenko , crazy we're still doing it after all these years.
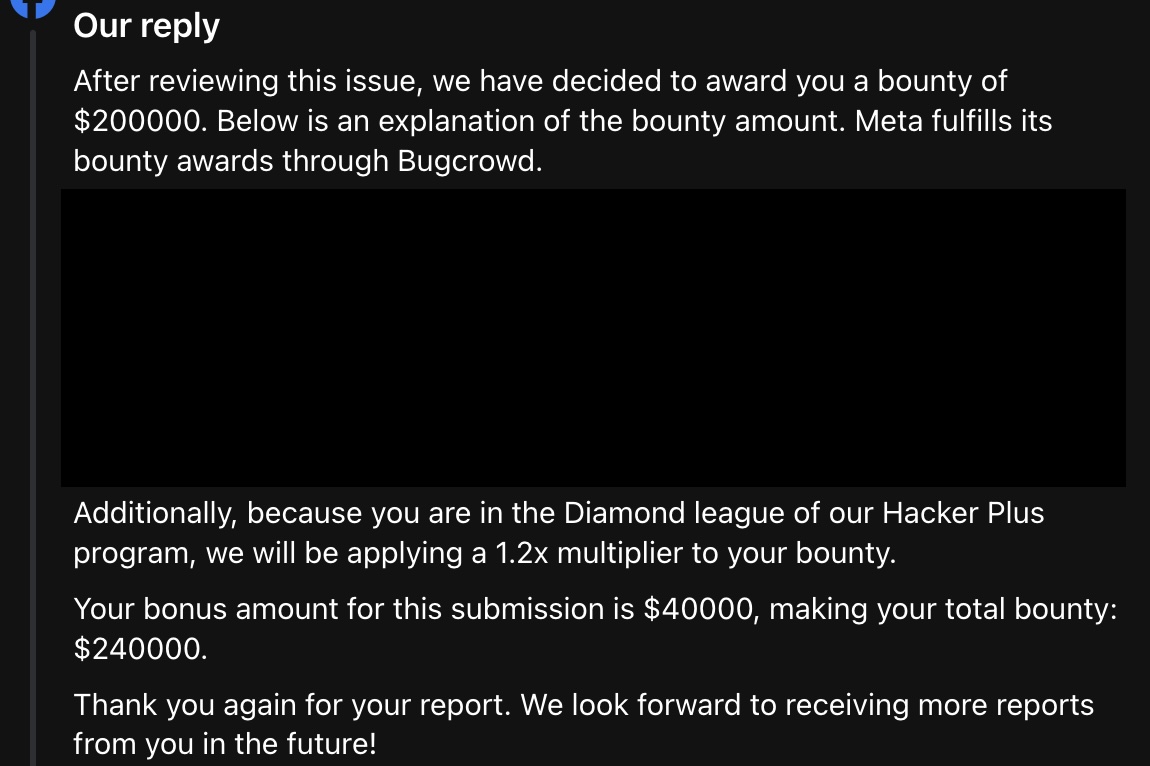

Thank you Meta Bug Bounty and everyone who attended Meta’s Bug Bounty Researcher Conference #MBBRC2025 in Tokyo! It was nice catching up with everyone and meeting new people! I had an amazing time and enjoyed all of the talks and events!






