Sean O'Connor (He/Him)
@vhumint
Head of @Equinix Threat Analysis Center (ETAC) | @sansforensics Author | @curatedintel contributor | Husband, Father, Veteran. Thoughts are my own
ID: 1254066248184446978
https://www.linkedin.com/in/vHUMINT/ 25-04-2020 15:14:46
837 Tweet
811 Followers
1,1K Following














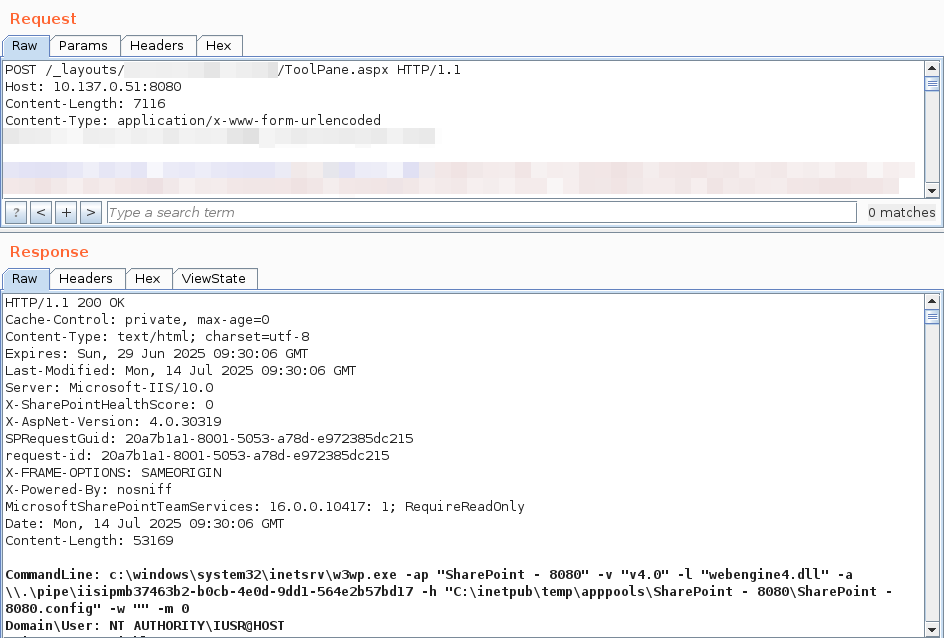
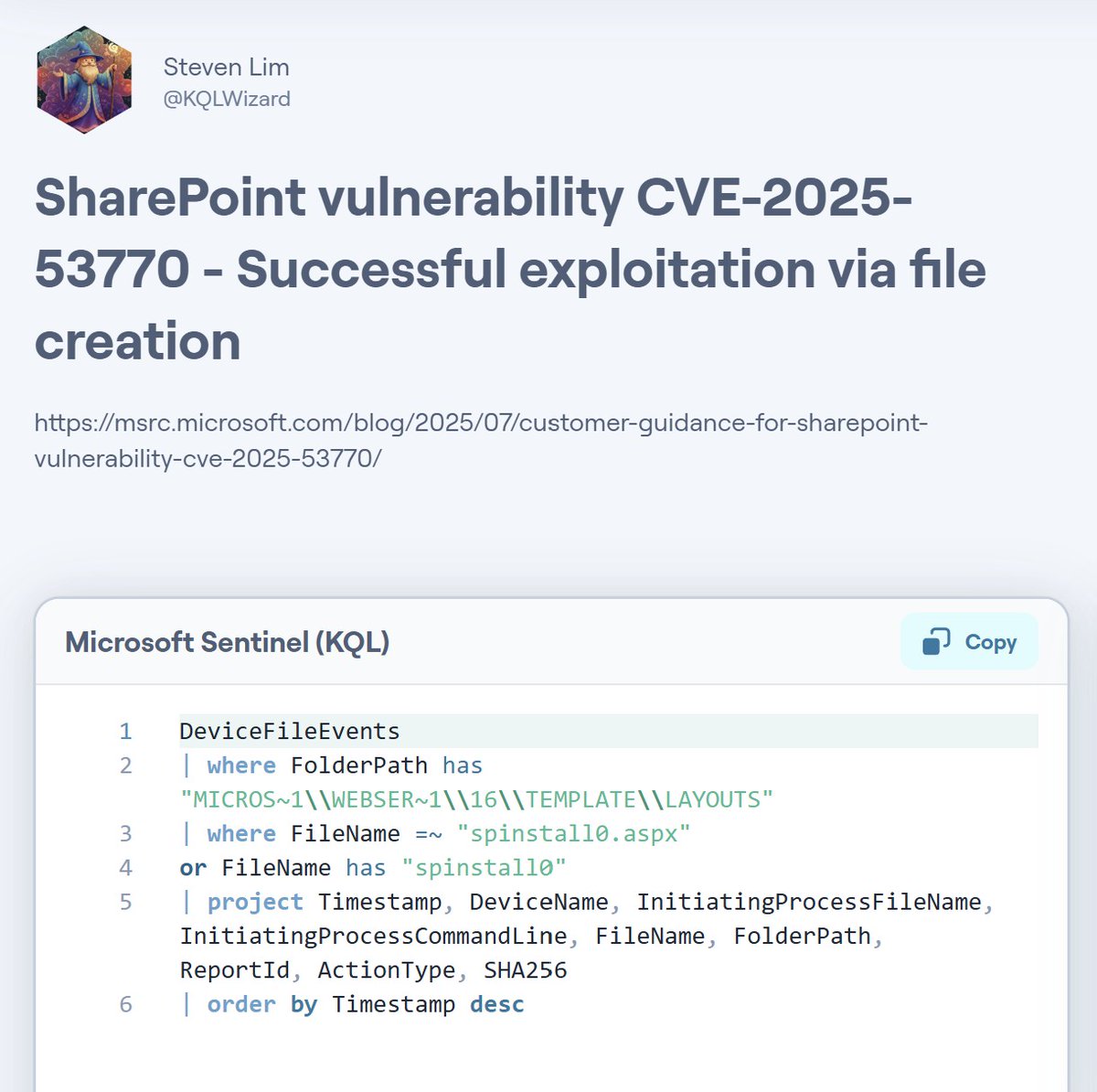
Sorry to disturb your weekend. There is a SharePoint 0day actively abused. Do not only focus on the rule of MSRC for hunting, other blogs also share different files and folders in use! Additional info: MSRC: msrc.microsoft.com/blog/2025/07/c… Blog by Eye Security: research.eye.security/sharepoint-und…

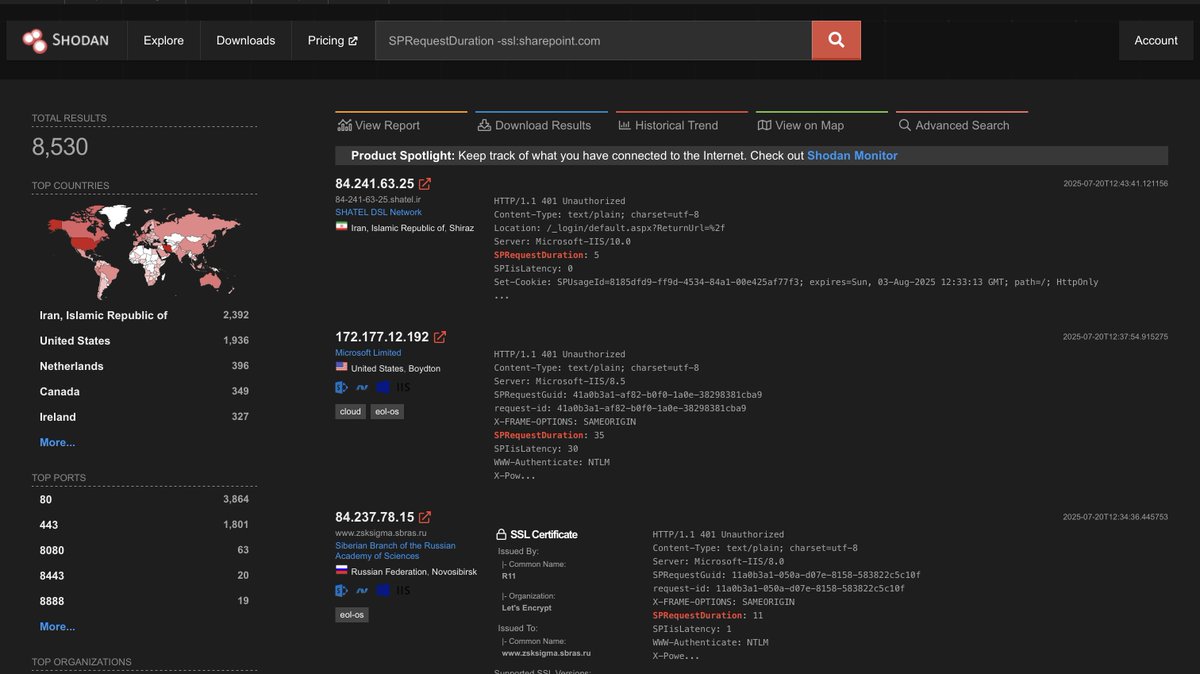
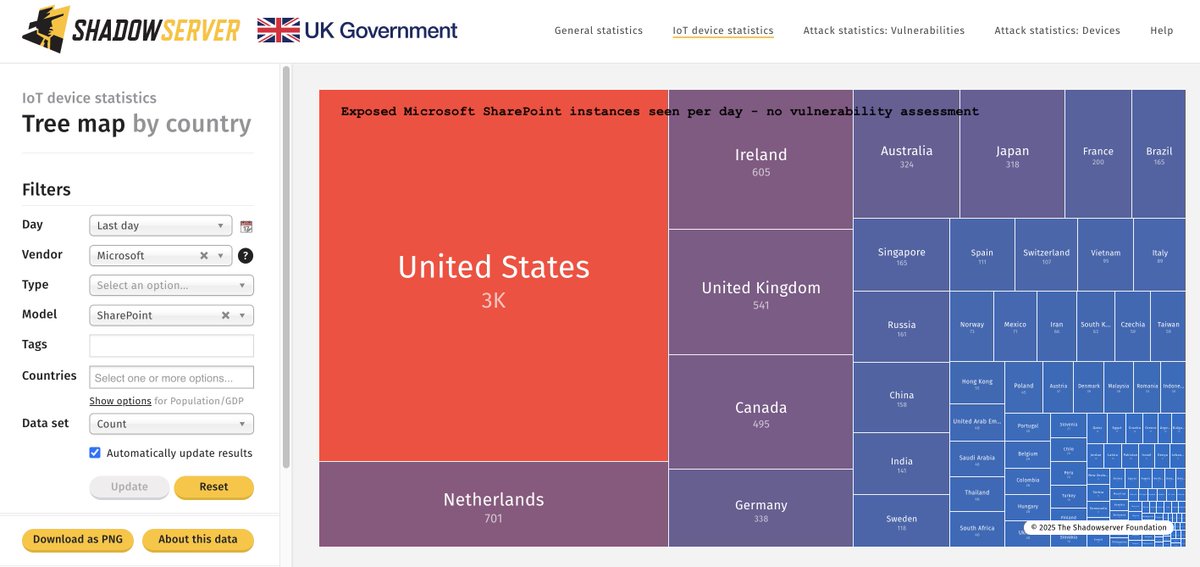
Alert: SharePoint CVE-2025-53770 incidents! In collaboration with Eye Security & watchTowr we are notifying compromised parties. Read: research.eye.security/sharepoint-und… ~9300 Sharepoint IPs seen exposed daily (just population, no vulnerability assessment): dashboard.shadowserver.org/statistics/iot…



Whats this... real DPRK ITW names and related emails/profiles?! 🇰🇵🍪🇰🇵🍪🇰🇵🍪 Enjoyyy and enrich with your data in the thread below ~> ❤️❤️🔥🔥 (will post raw for easier searching in 🧵🧵) Narcass3 aptwhatnow Kawaii-Jong-UwUn Matt 🍌rchism #NorthKorea #DPRK