Itamar Gilad
@trustingtrust
Threat Detection Lead, @wiz_io
ID: 871297109210918912
04-06-2017 09:26:33
146 Tweet
289 Followers
351 Following















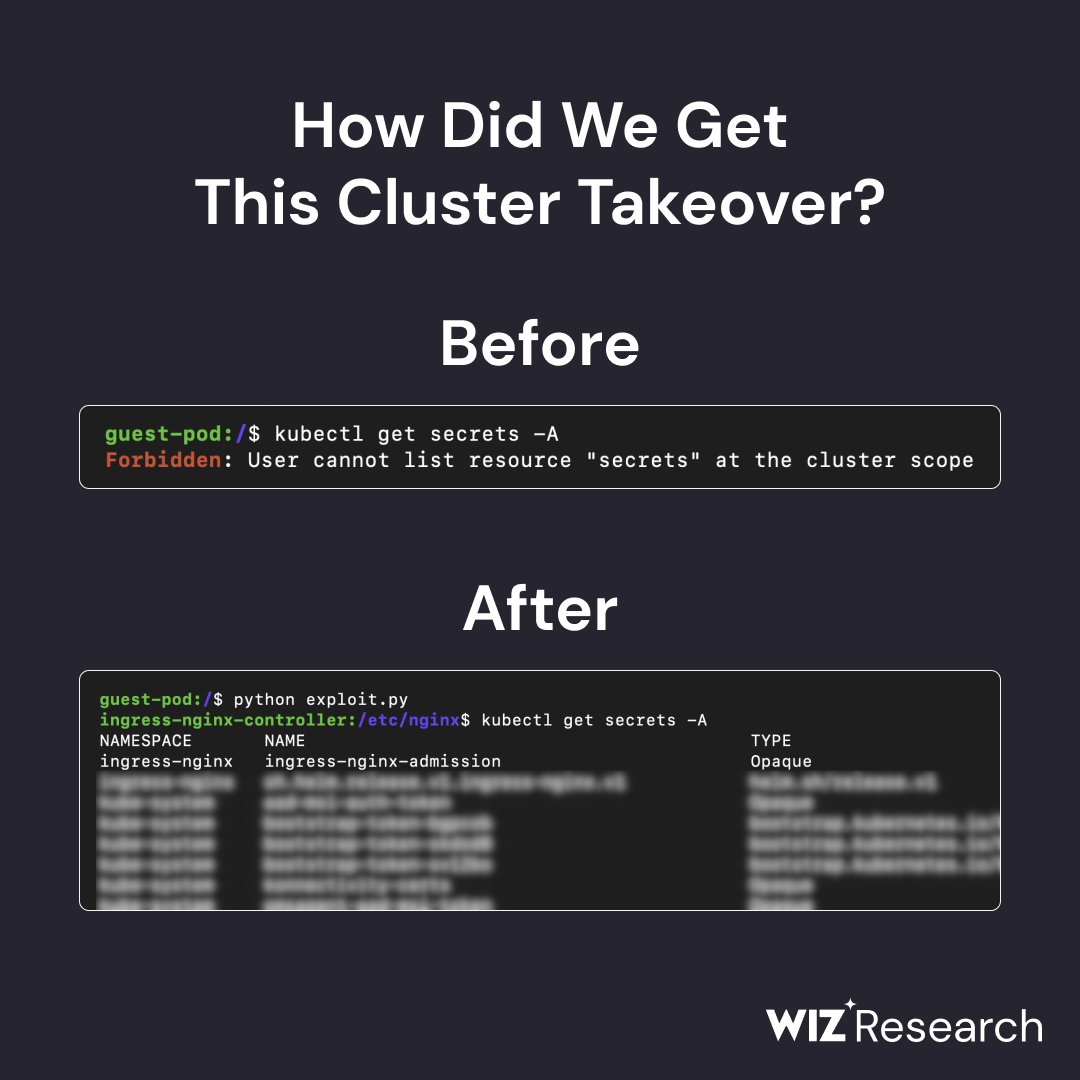
We (+sagitz Ronen Shustin Hillai Ben-Sasson) found a series of unauthenticated RCEs in core @KubernetesIO project "Ingress-NGINX". The impact? From zero permissions ➡️ to complete cluster takeover 🤯 This is the story of #IngressNightmare 🧵⬇️



🏆 Wiz Research took 1st place in #Pwn2Own's first-ever AI category, competing against global teams targeting critical AI infrastructure. Huge thanks to our incredible research team! Nir Ohfeld, Shir, Ronen Shustin, benny isaacs, sagitz & Nir Brakha!