🏴☠️🏴☠️T̵i̵g̵e̵r̵m̵a̵m̵R̵o̵o̵t̵ ̵🏴☠️🏴☠️
@tigermanroot
#𝑶𝒔𝒊𝒏𝒕 #𝑷𝒆𝒏𝒕𝒆𝒔𝒕𝒆𝒓. 𝑰 𝒍𝒐𝒗𝒆 #𝑳𝒊𝒏𝒖𝒙 𝑺𝒚𝒔𝒕𝒆𝒎 #H𝒂𝒄𝒌𝒆𝒓 - Python and C #programmer 🇮🇹 #Windows Admin Active Directory
ID: 1073503986605572096
https://youtube.com/channel/UC-S2cf2krYdMP8cJmOAdLZA 14-12-2018 09:04:29
31,31K Tweet
5,5K Followers
3,3K Following

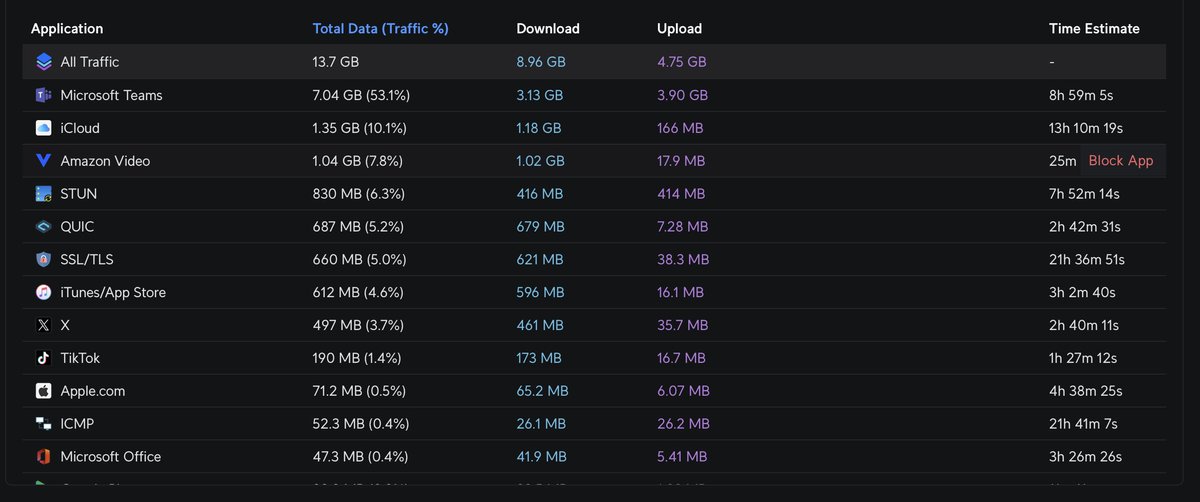
Are VPNs even safe now? YouTube video: youtu.be/Qqd9KzPVBb8 #privacy #vpn #cybersecurity #hack #hacker #hacking #infosec #firewall #security #CVE OccupytheWeb


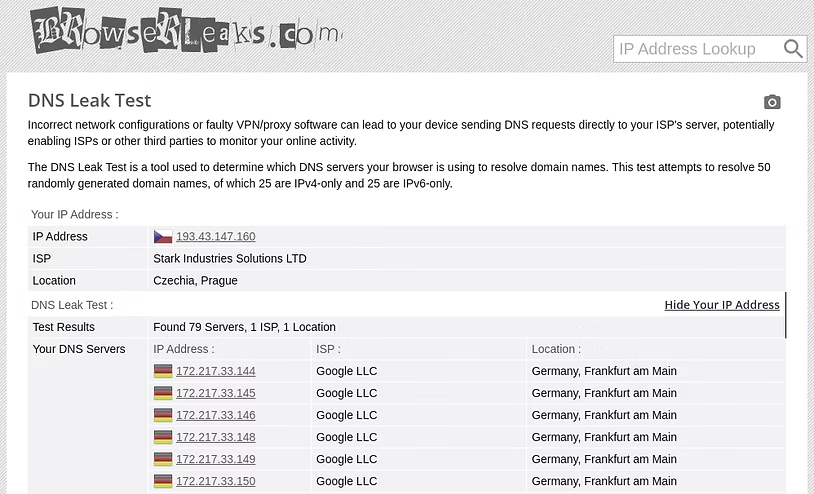
NymVPN: The World's Safest VPN? Discover the revolutionary mixnet VPN that's challenging traditional privacy tools. Step-by-step setup guide + real testing results. Anonymous mode beats Tor & standard VPNs! Read the full review! hackers-arise.com/nymvpn-setup-t… OccupytheWeb

Master network edge security with VPN & Router Hacking course! Learn how attackers target FortiOS, Ivanti Connect Secure, and enterprise routers through authentication bypass, command injection, and RCE exploitation. hackersarise.thinkific.com/courses/vpn-an… OccupytheWeb




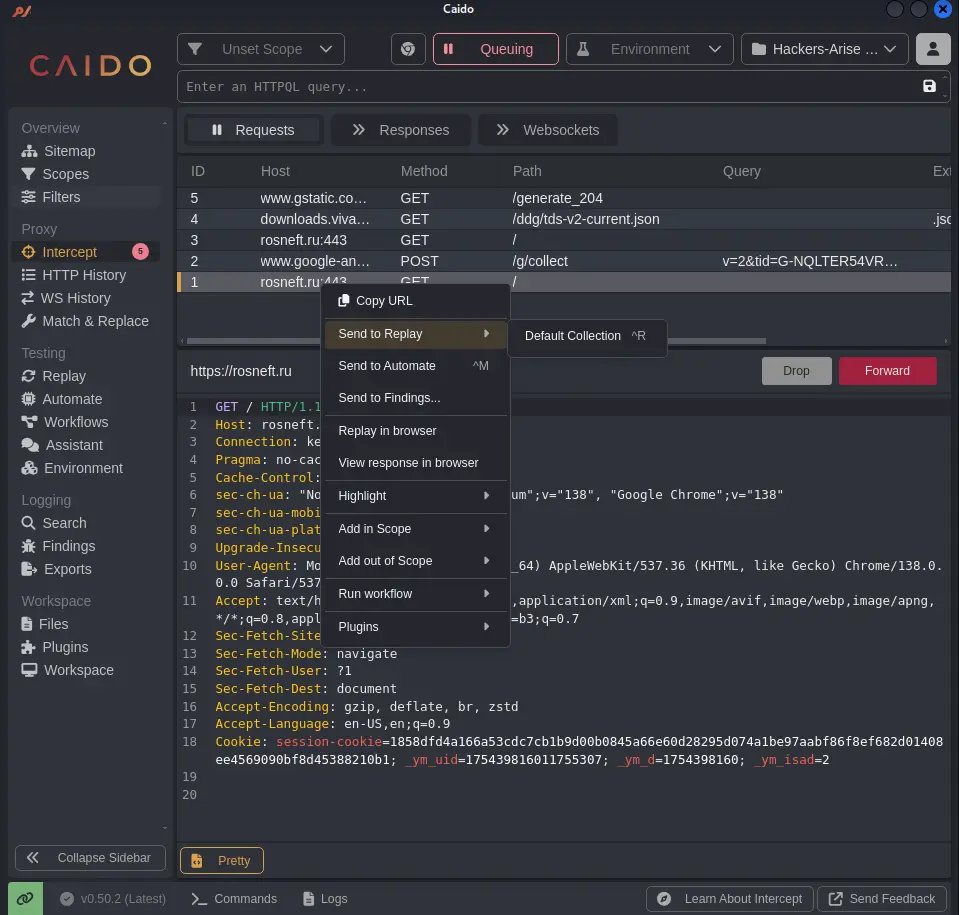
FREE Caido beats expensive Burp Suite! Master HTTP interception, replay attacks & HTTPQL filtering without breaking the bank. hackers-arise.com/web-app-hackin… OccupytheWeb









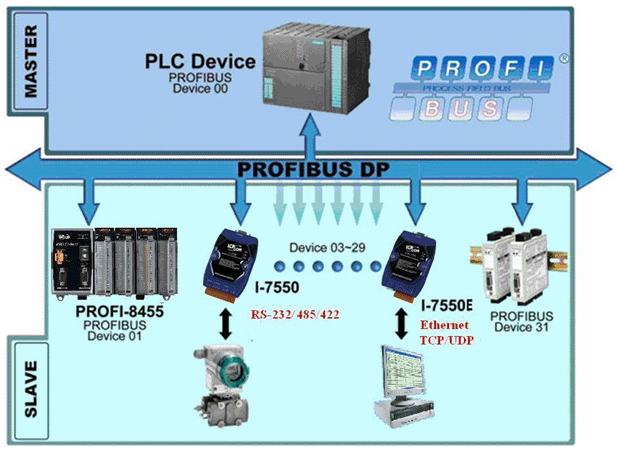
Learn PROFIBUS and PROFINET security fundamentals - from token-ring vulnerabilities to Ethernet-based attacks. Understand the protocols that run critical infrastructure and how to secure them against modern threats. hackers-arise.com/scada-hacking-… OccupytheWeb

pyghidra-mcp: headless Model Context Protocol (MCP) server for Ghidra Blog post: clearbluejar.github.io/posts/pyghidra… Repository: github.com/clearbluejar/p… Credits clearbluejar #infosec