
Tiesun 👨💻💾
@tie__sun
A guy who lives with the moments🍁.
Threat Intel Analyst | Adversary Hunter | Security Researcher
ID: 2397629168
https://hokage-guard.netlify.app/ 19-03-2014 10:25:49
4,4K Tweet
442 Followers
2,2K Following




Outstanding! Nguyen Hoang Thach (Thach Nguyen Hoang 🇻🇳) of STARLabs SG used a single integer overflow to exploit #VMware ESXi - a first in #Pwn2Own history. He earns $150,000 and 15 Master of Pwn points. #P2OBerlin






#FOFA #ThreatHunting | #APT #bitter Query: t.ly/hrgTo IoCs: pastebin.com/WE7bjsat Mikhail Kasimov Cyber Team Ginkgo Michael Koczwara MalwareHunterTeam ref: x.com/malwrhuntertea…
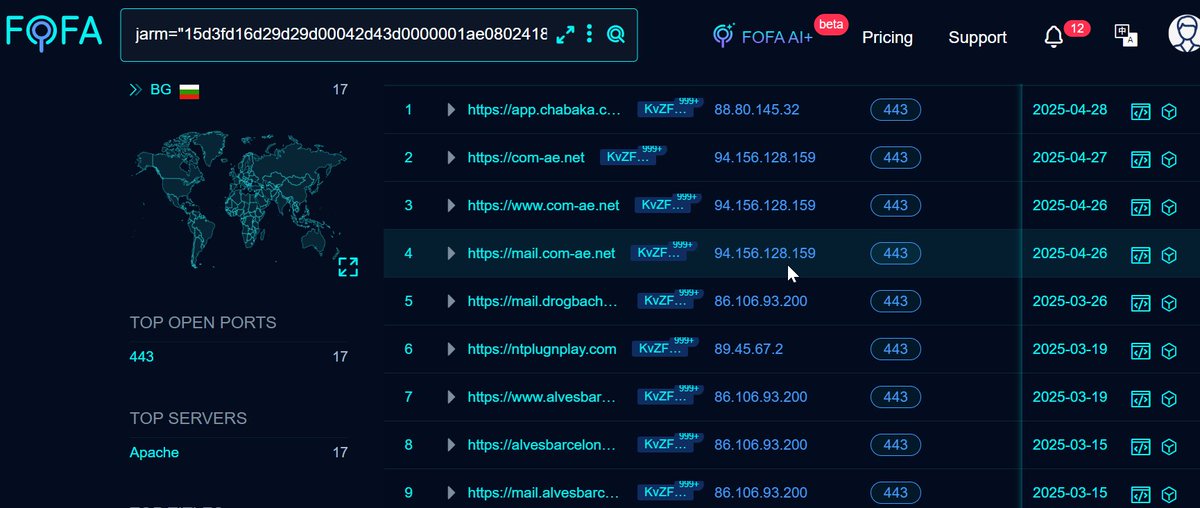






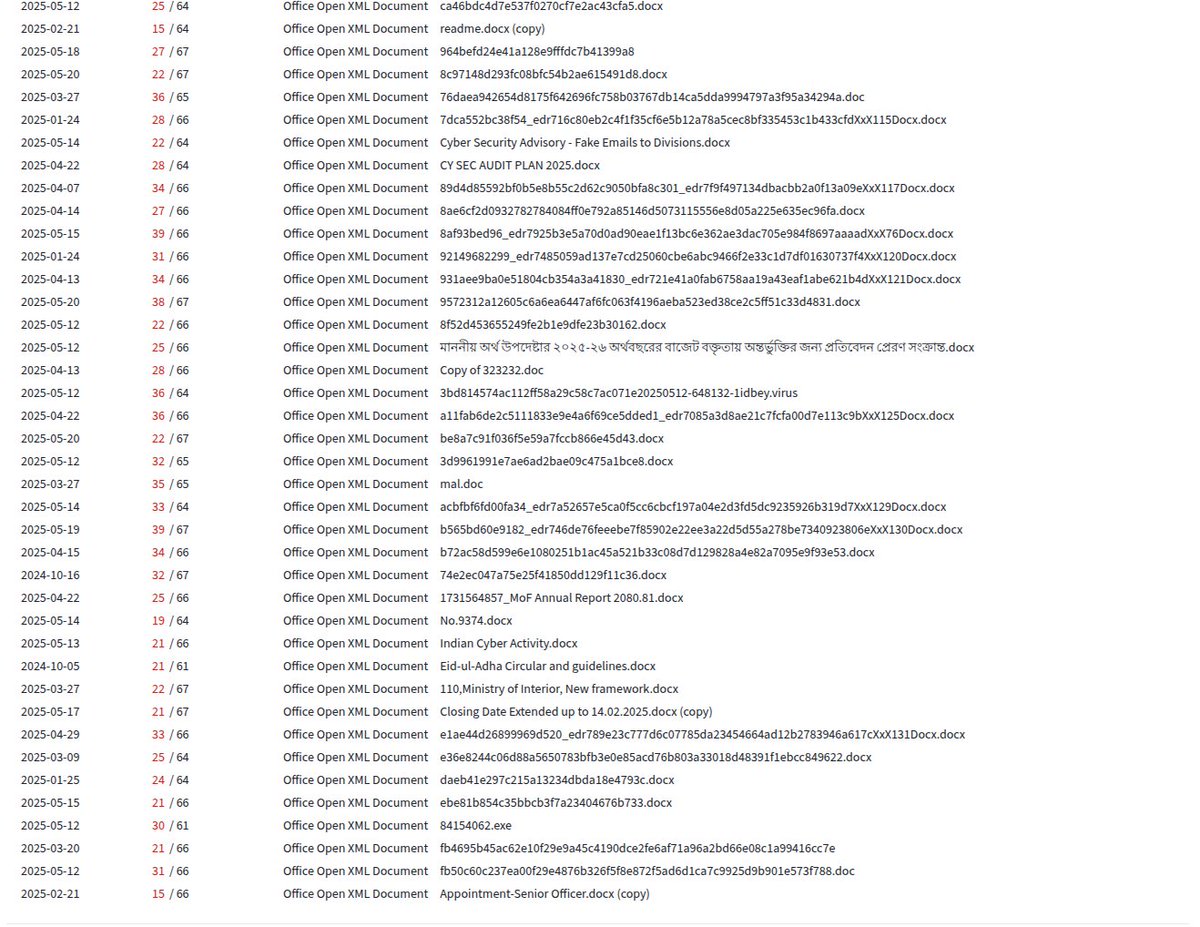
#Sidewinder #APT is dropping its favorite RTF file while launching multiple phishing campaigns. Target countries: 🇱🇰 🇧🇩 🇵🇰 🇳🇵 🇲🇲 🇲🇻 🇮🇩 We have consolidated all infra and are available at: pastebin.com/VFbNag7T Mikhail Kasimov (for update if any new infra) #Malware #ioc



![ThreatBook (@threatbooklabs) on Twitter photo #SideWinder #APT group disguises as the Ministry of Foreign Affairs domain.
#C2:
mofa-gov-np[.]org-liv[.]net
nic-svc[.]net
org-liv[.]net
threatbook.io/domain/mofa-go…
threatbook.io/domain/nic-svc…
threatbook.io/domain/org-liv…
Hash: 9b76d98c2641512c66e8f2f99b2d0bda86ec1a4809420b74feadfb8f4f7dbf48 #SideWinder #APT group disguises as the Ministry of Foreign Affairs domain.
#C2:
mofa-gov-np[.]org-liv[.]net
nic-svc[.]net
org-liv[.]net
threatbook.io/domain/mofa-go…
threatbook.io/domain/nic-svc…
threatbook.io/domain/org-liv…
Hash: 9b76d98c2641512c66e8f2f99b2d0bda86ec1a4809420b74feadfb8f4f7dbf48](https://pbs.twimg.com/media/GmfjY_naUAAAiT-.jpg)
![ThreatBook (@threatbooklabs) on Twitter photo #APT36
#Phishing websites:
indiandefence[.]directory
kashmiraxxack[.]exposed
#Sha256:
8b0ea6a9e427ac3288663e2f33bc3df5ea01bfdaead81d4b6595b00a6b7c4301 (Advisory Notice Movement of Troops.ppam)
It is related to military movements.
#C2: 93.127.133.58:17241|19821|21817|23221|27425 #APT36
#Phishing websites:
indiandefence[.]directory
kashmiraxxack[.]exposed
#Sha256:
8b0ea6a9e427ac3288663e2f33bc3df5ea01bfdaead81d4b6595b00a6b7c4301 (Advisory Notice Movement of Troops.ppam)
It is related to military movements.
#C2: 93.127.133.58:17241|19821|21817|23221|27425](https://pbs.twimg.com/media/Gqa8CJJXQAAH8cK.jpg)

![MalwareHunterTeam (@malwrhunterteam) on Twitter photo "Circular.rar" seen from Pakistan: 7fe0e88514fe4f1a74360b905be923c61dff84b576a96c3550a02a46b9ae95e3
->
"Circular.chm": 243e4d1e53a805f61d2c4e8cabdd02e99a51fba37101b3e0535f219383871091
www.ntplugnplay[.]com "Circular.rar" seen from Pakistan: 7fe0e88514fe4f1a74360b905be923c61dff84b576a96c3550a02a46b9ae95e3
->
"Circular.chm": 243e4d1e53a805f61d2c4e8cabdd02e99a51fba37101b3e0535f219383871091
www.ntplugnplay[.]com](https://pbs.twimg.com/media/GrI3B2OWkAAuA1L.jpg)




![Chris Duggan (@tlp_r3d) on Twitter photo 🇮🇳🐍Potential Sidewinder Cobalt Strike Redirectors in Action
🐍185.159.128.117 0/94 in VT
🔥Suspect Domain: islamabadpolice[.]net 0/94 in VT - hosted on Cloudflare
Spoofing legit domain: fir.islamabadpolice[.]gov[.]pk
🐍31.15.17.230 0/94 in VT
🔥Suspect Domain: 🇮🇳🐍Potential Sidewinder Cobalt Strike Redirectors in Action
🐍185.159.128.117 0/94 in VT
🔥Suspect Domain: islamabadpolice[.]net 0/94 in VT - hosted on Cloudflare
Spoofing legit domain: fir.islamabadpolice[.]gov[.]pk
🐍31.15.17.230 0/94 in VT
🔥Suspect Domain:](https://pbs.twimg.com/media/GrsHtHuXIAAEHIG.jpg)