
Steve YARA Synapse Miller
@stvemillertime
threat intelligence @google
writing & sharing on adversary tradecraft, malware, threat detection, ics/ot intel and all things #yara
ID: 19564532
https://bsky.app/profile/stvemillertime.bsky.social 26-01-2009 23:03:07
5,5K Tweet
16,16K Followers
1,1K Following



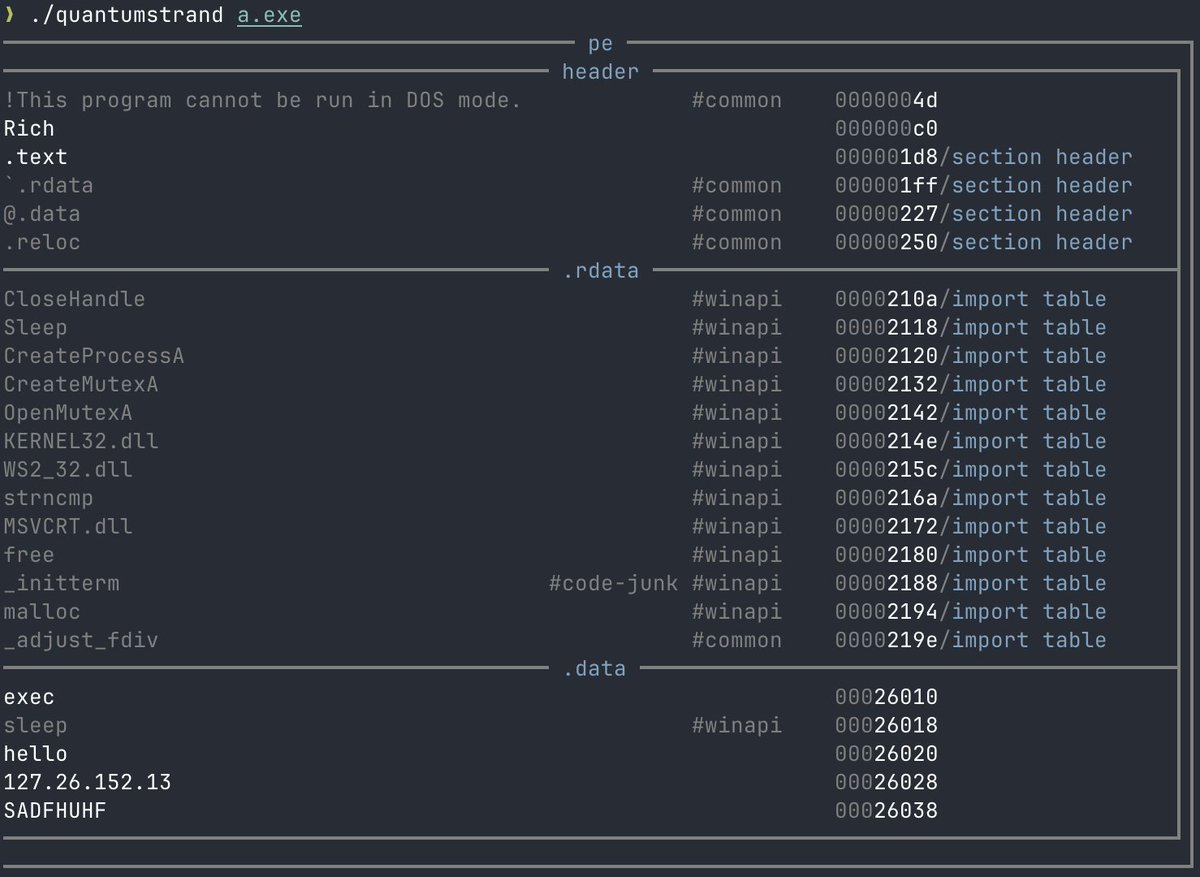
QUANTUMSTRAND beta 1 released: built for analysts to quickly understand *where* strings are, *what* they might be, and *how* important they are, without getting lost in a sea of undifferentiated text. Thanks Moritz and the crew at Mandiant (part of Google Cloud) FLARE github.com/mandiant/flare…










Steve YARA Synapse Miller Debuggers on malware are like the old roguelike RPGs with no formal save game feature and perma-death. You are following a linear path through the dungeon avoiding antianalysis traps and collecting loot in the form of IOCs. The graphics are much worse than those old RPGs.


