
Scott Ruoti
@scottruoti
Assistant professor @EECS_UTK. Researching computer security and human factors. Follower of Jesus Christ and a member of His restored church (@Ch_JesusChrist).
ID: 1032807643067441154
http://userlab.utk.edu/scott-ruoti 24-08-2018 01:51:45
91 Tweet
105 Followers
85 Following



Next up in our #ACSAC2021 #paper #previews is Oesch et al.'s investigation of whether autofill is secure on mobile devices. Their paper explores this question, identifying both strengths and critical vulnerabilities for mobile autofill frameworks! Scott Ruoti Sean Oesch Anuj Gautam

If you are interested in researching password managers, this #ACSAC2021 #paper #preview is just the paper to get you started. In it, Simmons et al. systematize use cases as well as design paradigms and identify open research needs. Scott Ruoti Sean Oesch

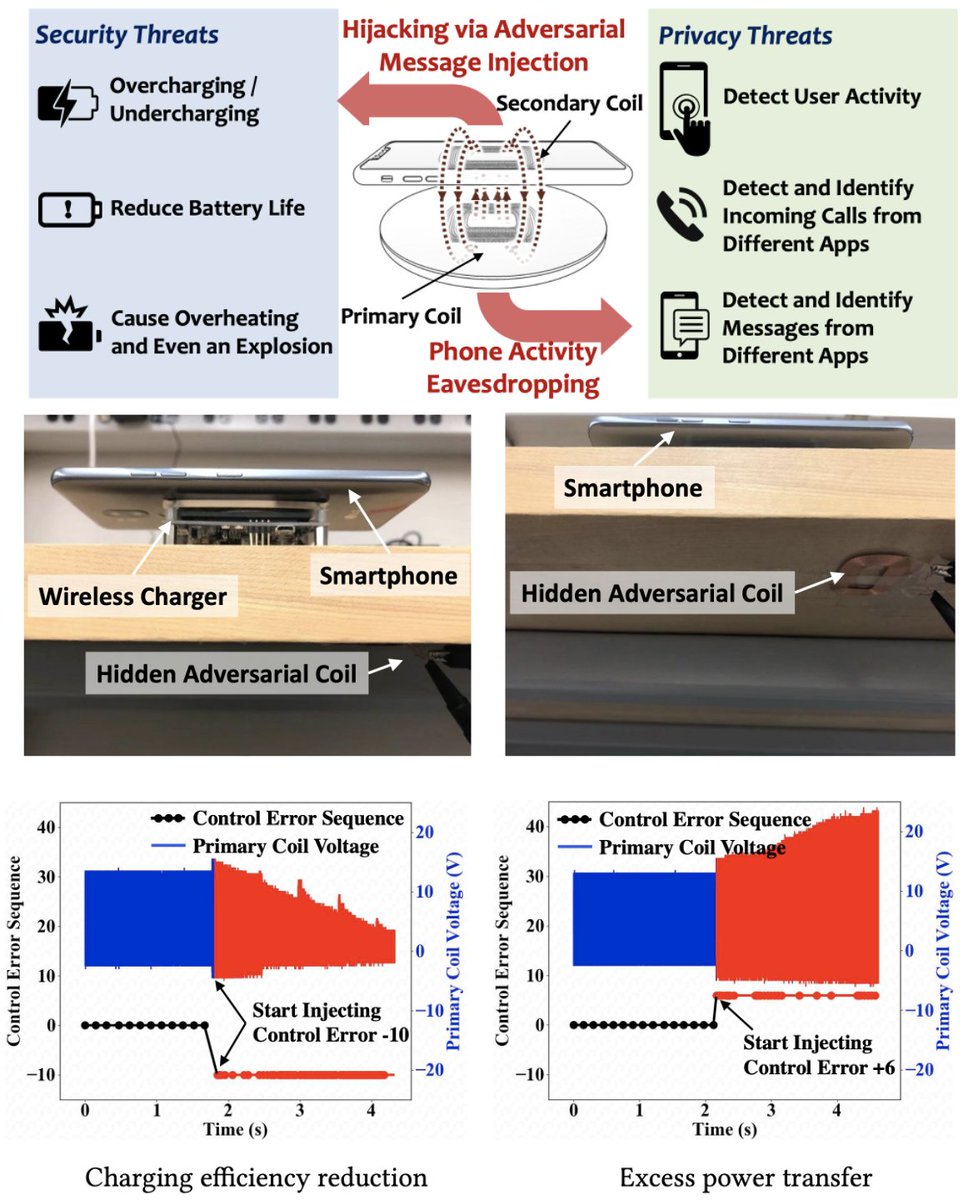
Today's #ACSAC2021 #paper #preview looks at Wu et al.’s "Security and Privacy Vulnerability Analysis of Qi Wireless Charging" reveals critical vulnerabilities of Qi wireless charging through the nearby hidden adversarial coil. Jian (Jack) Liu EECS Tickle College of Engineering UT Knoxville

📢Note the date for the next #CASADistinguishedLecture with Scott Ruoti 👉December 16, 2021, 4:00 pm (UTC +1) 👉Topic: Johnny’s Journey Toward Usable Secure E-mail” 👉Free access –Get link & abstract here: casa.rub.de/en/news/distin…


The Call for Papers for the Eighteenth Symposium on Usable Privacy and Security (SOUPS 2022) is now available! The symposium will take place will take place August 7–9 in Boston, MA. Details: bit.ly/soups2022cfp Symposium on Usable Privacy and Security



I'm excited to announce that our paper (Sean Oesch, Anuj Gautam) examining password manager usage in the wild will appear at CHI '22. Our results shed light on how, and more importantly why people use password managers as they do. Preprint here: userlab.utk.edu/publications/o…


My department wrote a press release about Senjuti Dutta's forthcoming #CHI2022 paper on mobilizing crowdwork through design. (cc: Rhema Linder, PhD, Anastasia Kuzminykh) PS: Paper available soon! #ProudAdvisor eecs.utk.edu/doctoral-stude…




Podcast (Futurati w/ Trent Fowler and Thomas Frey CSP) episode with me introducing L2s, cryptographic voting, and other topics: youtu.be/Rk-hOQI0C5c Also check out the episode before with Scott Ruoti: youtu.be/2z3g-ZCaWF0





