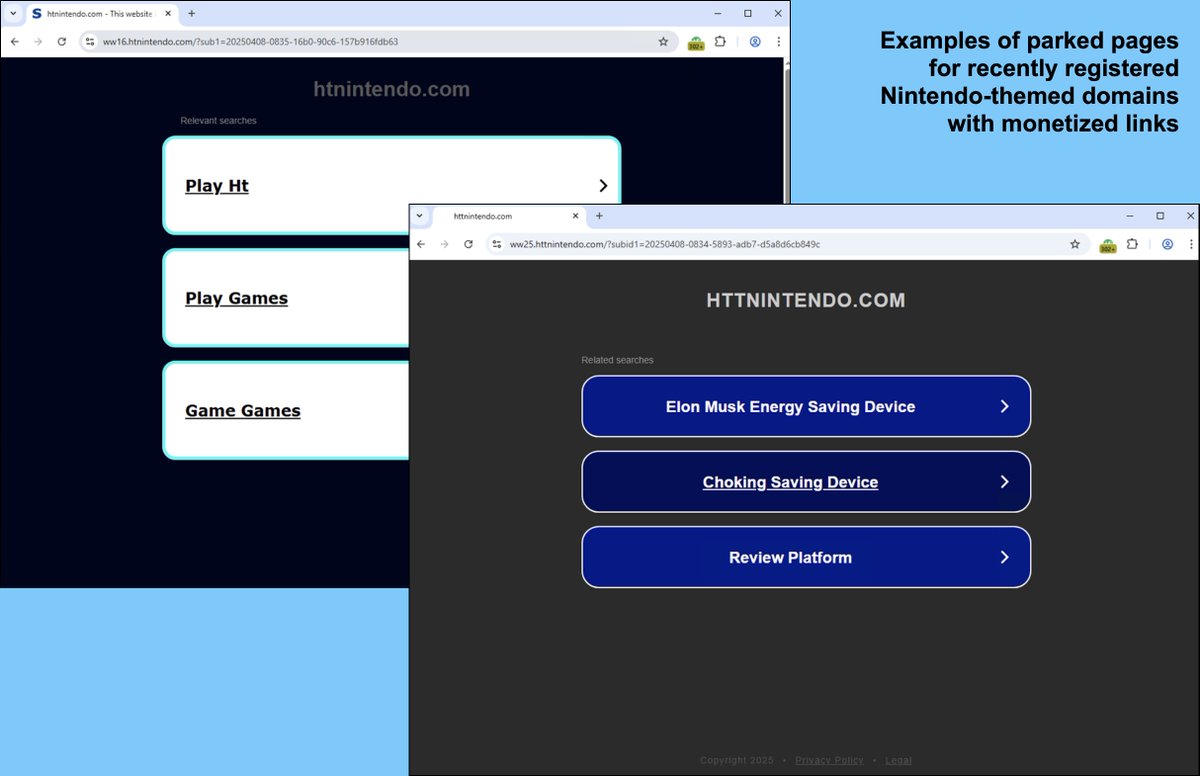
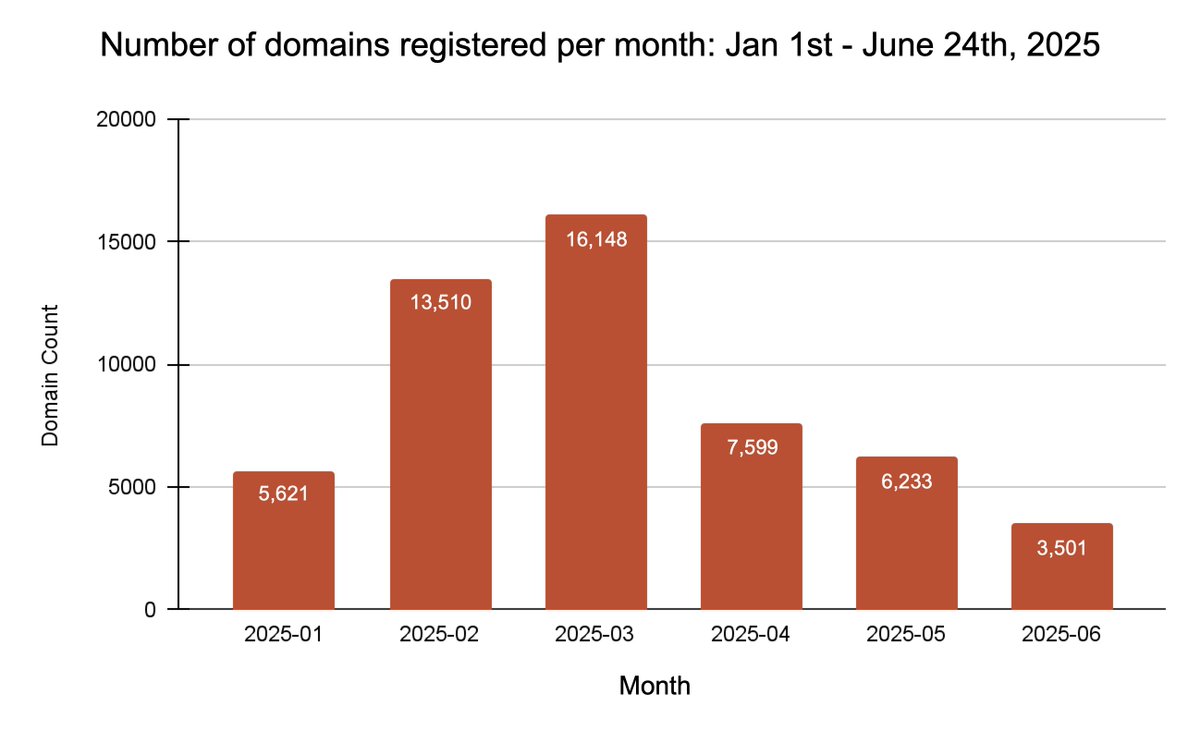
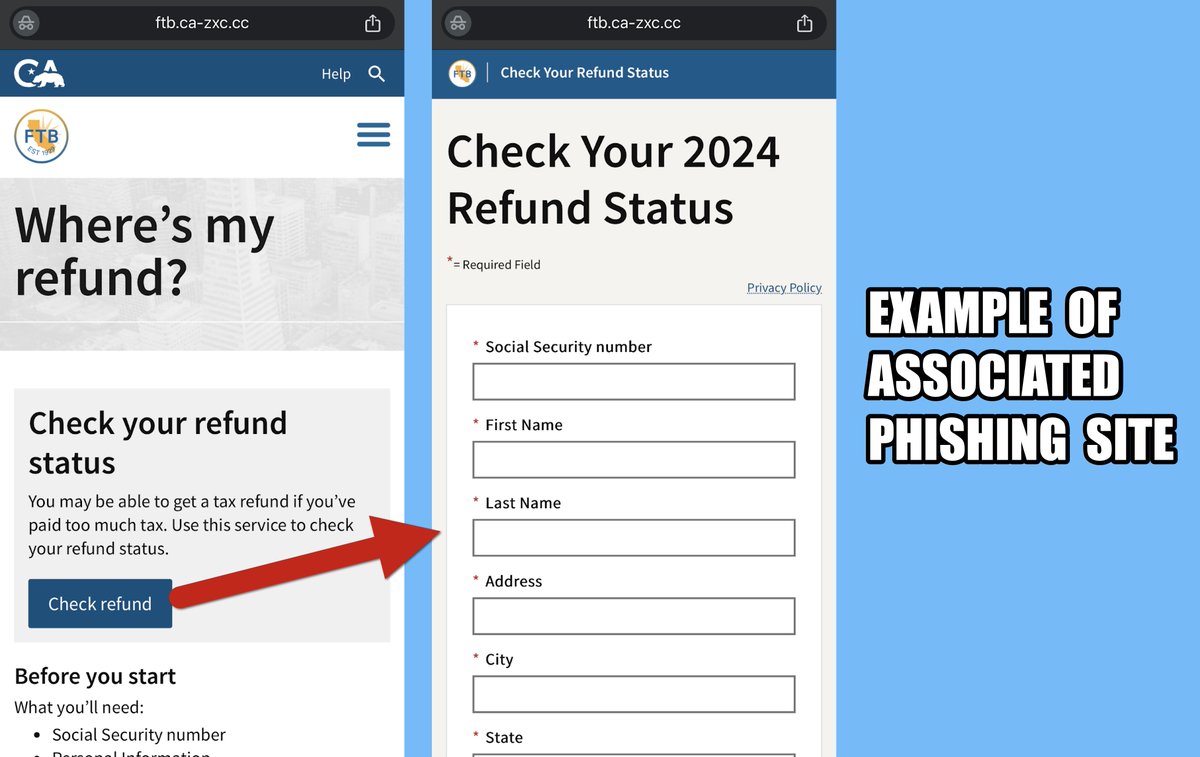
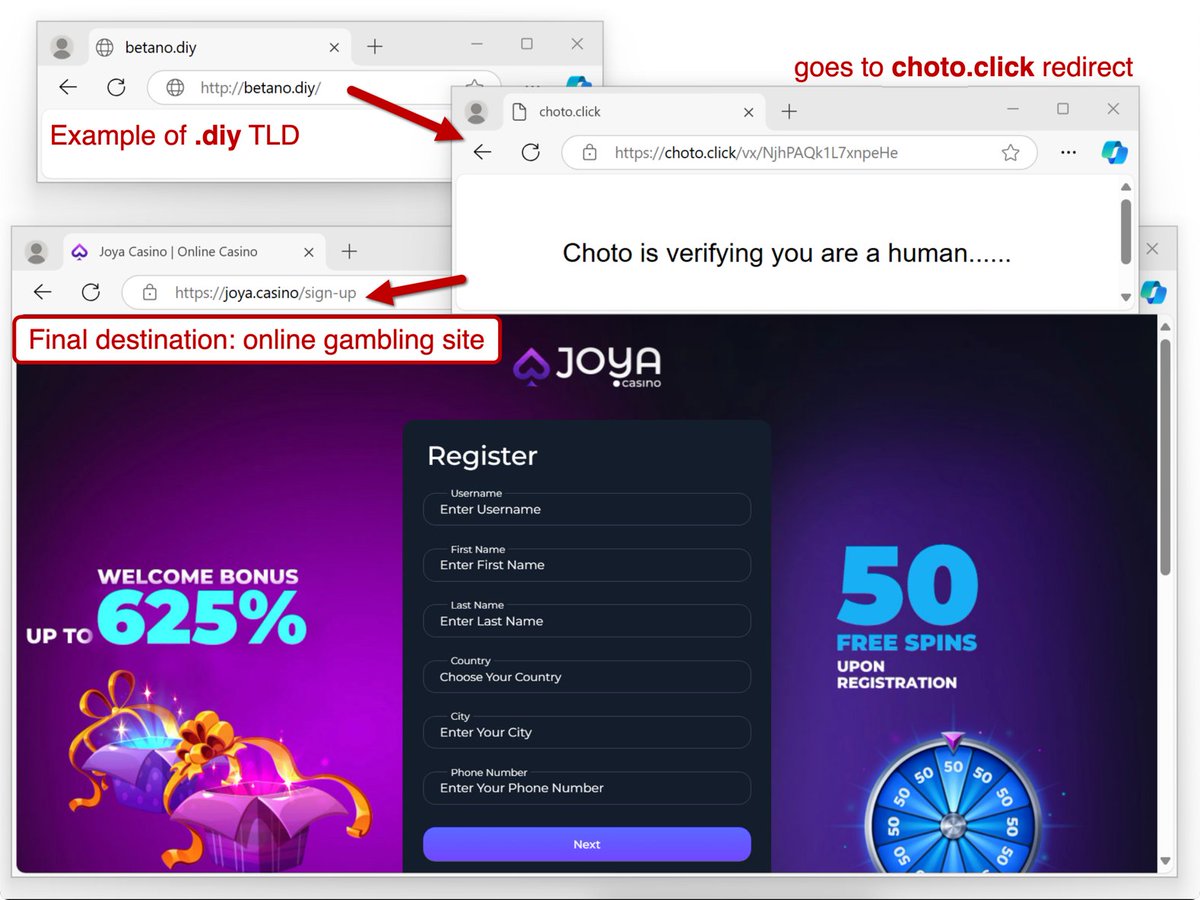
reethika
@reethika_
Senior Staff Researcher at @PaloAltoNtwks | CS PhD from @UMich | Security, Privacy, Internet Measurement | Previously: Research Intern @Brave
ID: 809431717979168768
http://reethika.info 15-12-2016 16:15:34
597 Tweet
512 Followers
692 Following






















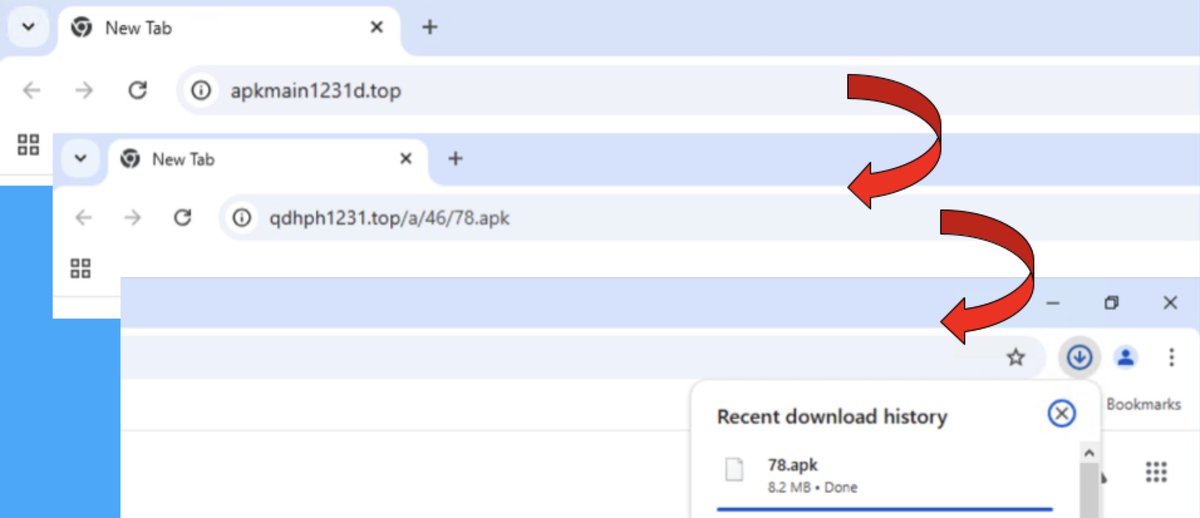




![Unit 42 (@unit42_intel) on Twitter photo We found 80K+ domains used in investment and job #scams. Attackers #StrategicallyAged newly-registered domains for at least 1 month to evade blocking. When active, the domains redirect to URLs on linksapp[.]top and mainly target Japanese users. Details at bit.ly/41EIkPm We found 80K+ domains used in investment and job #scams. Attackers #StrategicallyAged newly-registered domains for at least 1 month to evade blocking. When active, the domains redirect to URLs on linksapp[.]top and mainly target Japanese users. Details at bit.ly/41EIkPm](https://pbs.twimg.com/media/Gmkr75OWcAAE4GX.jpg)