Lei Wu
@realvisual
Co-founder of BlockSec (@BlockSecTeam) | Views are my own
ID: 32685186
https://leiwu.org 18-04-2009 00:32:25
568 Tweet
264 Followers
157 Following

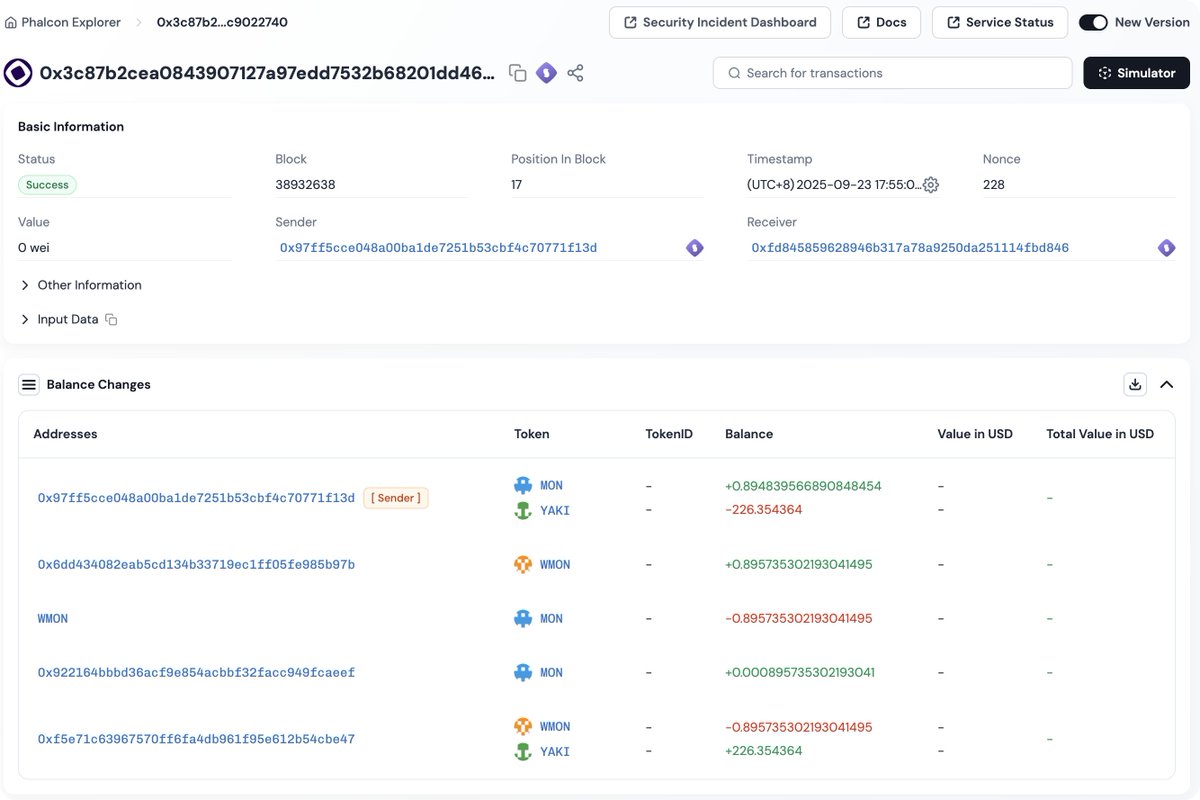
ALERT! Our system detected multiple attacks on #BSC targeting unidentified contracts (suspected MEV bots), resulting in ~$2M in stolen assets (e.g., vTokens) value. While rumors suggest the victim is Venus Protocol, our investigation confirms no association with the protocol






Just curious why users are still interacting with Bankroll Network? Every transaction here is basically lining the attackers’ pockets. Do yourself a favor: Stay far away.



The submission deadline to the ACM CCS workshop on Decentralized Finance and Security has been extended to July 28, 2025 (AoE). Thanks to our incredible program committee & chairs. Aviv Yaish @christoftorres Alex Biryukov Chen-Da Jeremy Clark Jan Gorzny Zhe Ye Manvir Schneider Paweł Szałachowski

Blockchain Security Award Ceremony Pioneering blockchain security talent development to strengthen Hong Kong's Web3 industry. 🚀 BlockSec will award the BlockSec Blockchain Security Award at The Hong Kong Polytechnic University (PolyU), recognizing outstanding talent and celebrating the future of