
radare
@radareorg
Reverse Engineering Framework for the commandline cowboys. Follow us in our primary fediverse for more updates infosec.exchange/@radareorg
ID: 111926756
http://rada.re 06-02-2010 16:36:51
8,8K Tweet
20,20K Followers
8 Following





HackerFrogs is live! We're learning more XOR Cryptography /w picoCTF and CryptoHack , then /w picoCTF we're learning the Radare2 debugger, finally we're hacking Windows Active Directory /w Thehackerslabs Doraemon! Watc h here: twitch.tv/theshyhat youtube.com/watch?v=Q2xp-f…

LaurieWired i've got one for radare2 you should try github.com/dnakov/radare2…





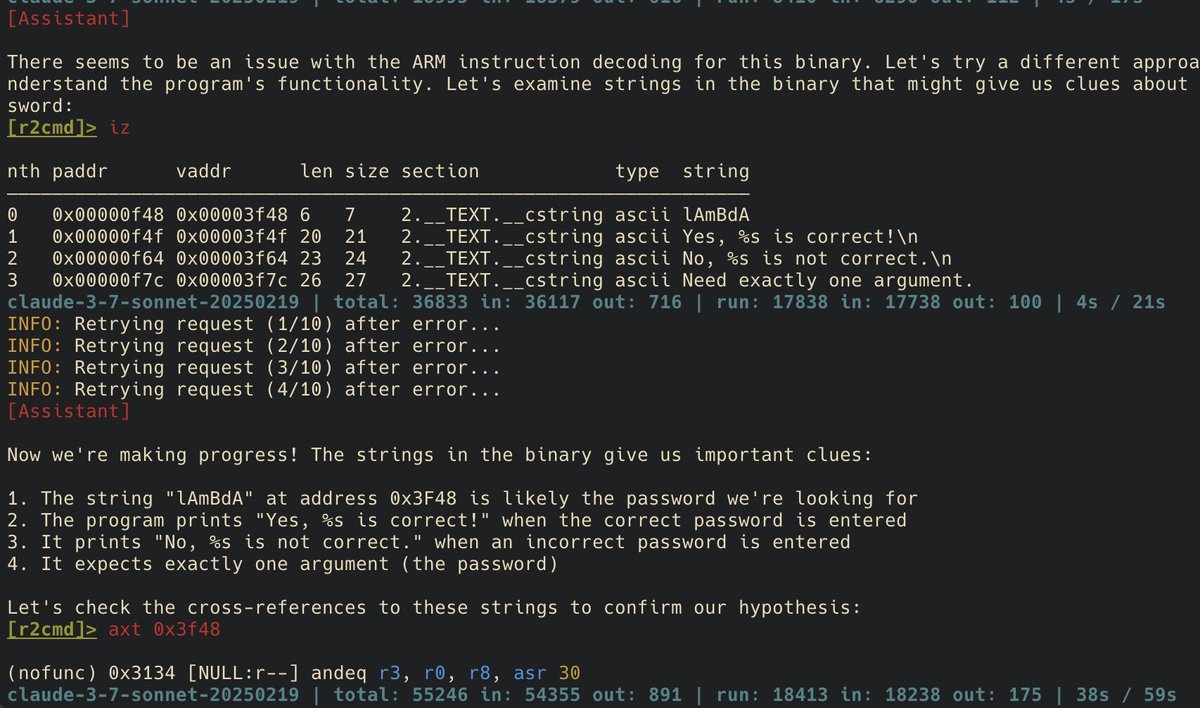
r2ai comes with ask_to_execute (aka baby_mode) by default, where it asks you to confirms everything it executes. Axelle Ap. @cryptax @mastodon.social already thought of that months ago. You don't get that choice with Claude Desktop, you can barely even see the code after you click Allow.








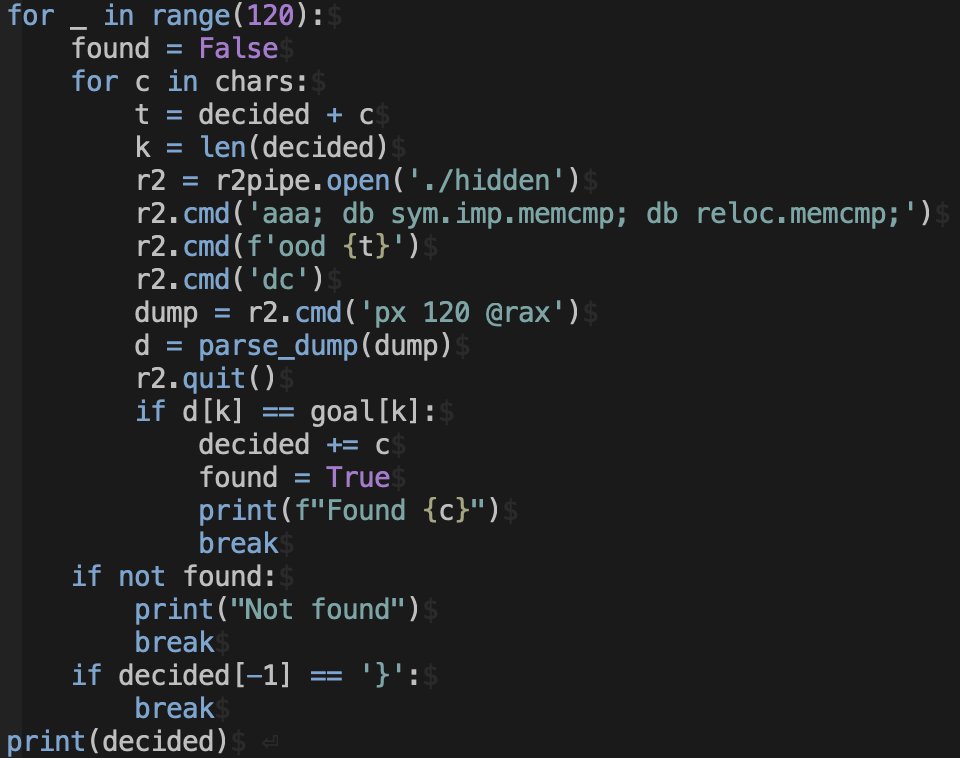





![Daniel Nakov (@dnak0v) on Twitter photo I made a browser extension to enable MCP for claude[.]ai. It works via SSE, so you can just directly point it to your SSE MCP servers. It's kinda cool because it actually just uses the existing code Anthropic already has, just not enabled. So all of the MCP UI works :D I made a browser extension to enable MCP for claude[.]ai. It works via SSE, so you can just directly point it to your SSE MCP servers. It's kinda cool because it actually just uses the existing code Anthropic already has, just not enabled. So all of the MCP UI works :D](https://pbs.twimg.com/media/GoXD_jZXcAADOoW.jpg)

