Darren McDonald
@r3n5k1
Currently into Rust, phishing, redteaming, and hardware.
ID: 380798609
http://cryptic.red 27-09-2011 07:44:37
99 Tweet
105 Followers
95 Following


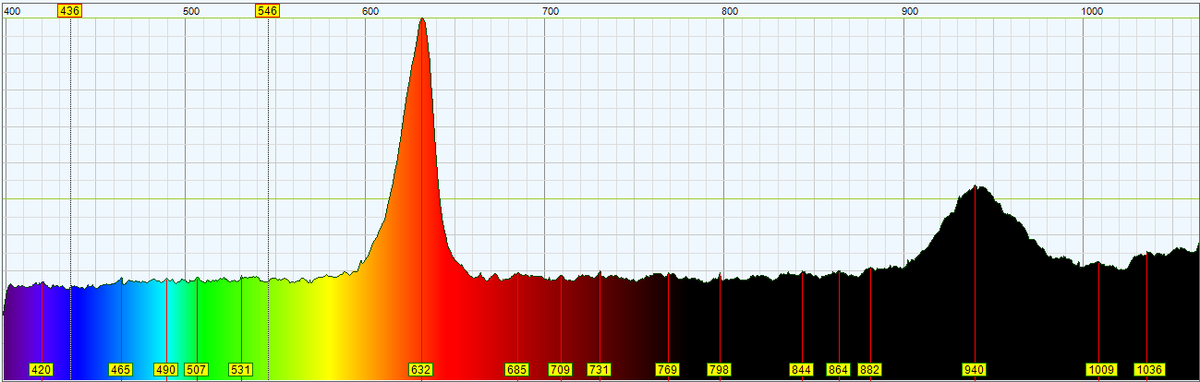
If you aren't using a pre-boot PIN with bitlocker, I'm getting in. With Darren McDonald
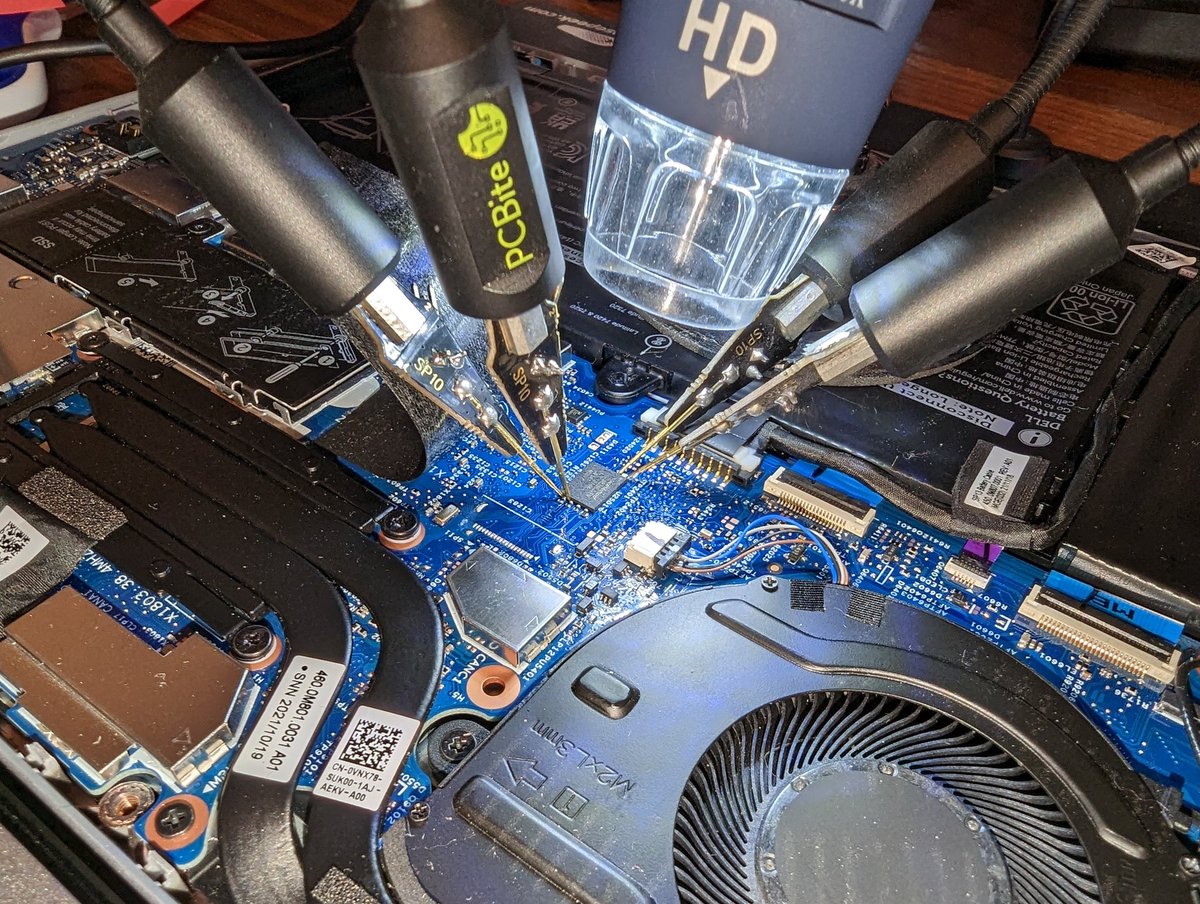








BSides Basingstoke thanks for a great day Darren McDonald , Luke Rogerson and I had an awesome time!




We're excited to announce our first speaker for the October mini meet! Darren McDonald will be delivering his talk, "Breaking the Shield: Bypassing FortWeb WAFs and Zscaler ZIA"


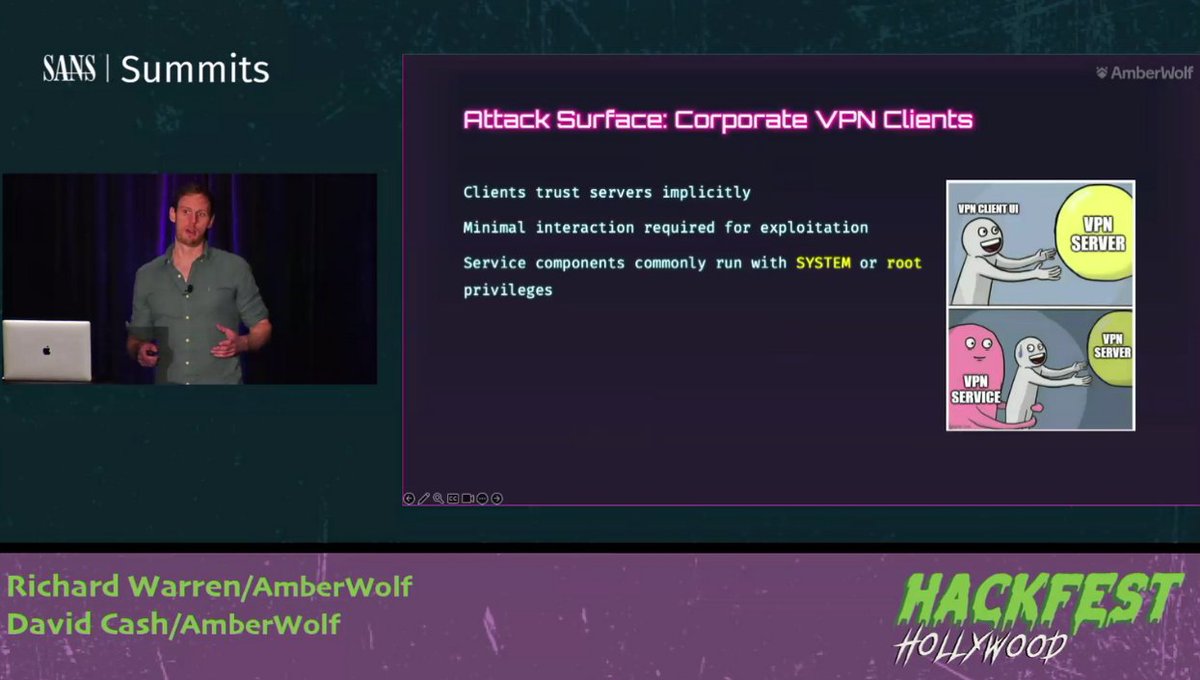
.Rich Warren & Johnny Fishcake are discussing how to exploit corporate VPN clients for remote root & SYSTEM shells. Join to see live demos on Windows & macOS vulnerabilities & how attackers gain control w/ just one click. Register Free: sans.org/u/1vBt #SANSHackFest


Just released a few new courses - the start of my "Code Review & Architecture Fundamentals" series. 33% off on two of the courses until EOD 2nd Dec. Big thanks to CourseStack for their support in making this possible! 👉 ogsec.co.uk/2024/11/13/cod…