BlockSec Phalcon
@phalcon_xyz
A Platform to Monitor and Block Hacks | The only one boasting dozens of successful white-hat rescues. | Built by @BlockSecTeam
👉TG: t.me/BlockSecTeam
ID: 1278266969532203008
https://blocksec.com/phalcon 01-07-2020 09:59:43
855 Tweet
5,5K Followers
39 Following




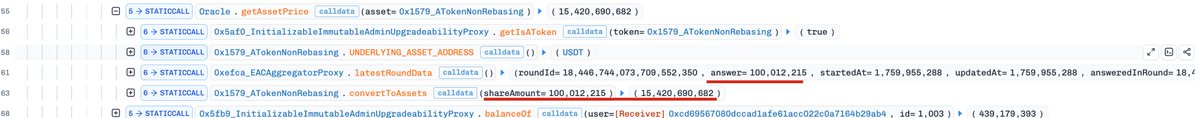
.Sharwa.Finance was reported to be exploited and subsequently paused (as claimed by the project). However, several additional suspicious transactions occurred hours later, likely exploiting the same underlying issue through slightly varied attack paths. In general, the



yo just saw that BlockSec Phalcon has integrated swiss-knife.xyz for Calldata Decoder 🙌






We’ve added two neat updates to Phalcon Explorer! 1️⃣ Direct link to swiss-knife.xyz to decode call data 2️⃣ Show Unix time for tx timestamps 🐛 Found a bug or have a feature idea? DM us or join t.me/BlockSecTeam!