MalasadaTech
@malasadatech808
ALOJAHZ WORLD! HOBBYIST THRUNTELLISEARCHER. VIEWS ARE MY OWN! 808 MALASADA.TECH
ID: 1956187113256607744
15-08-2025 02:53:02
21 Tweet
1 Followers
76 Following









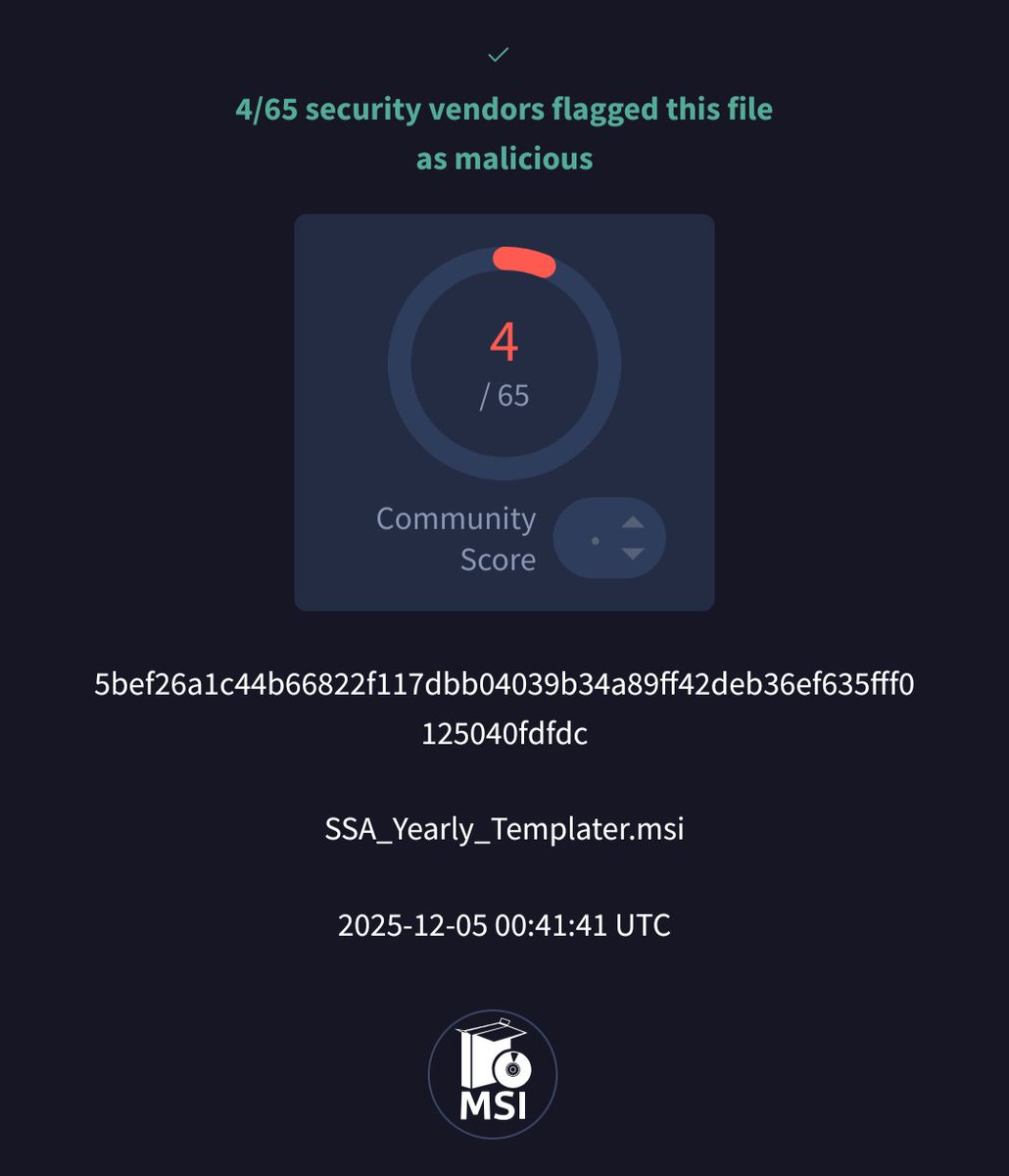
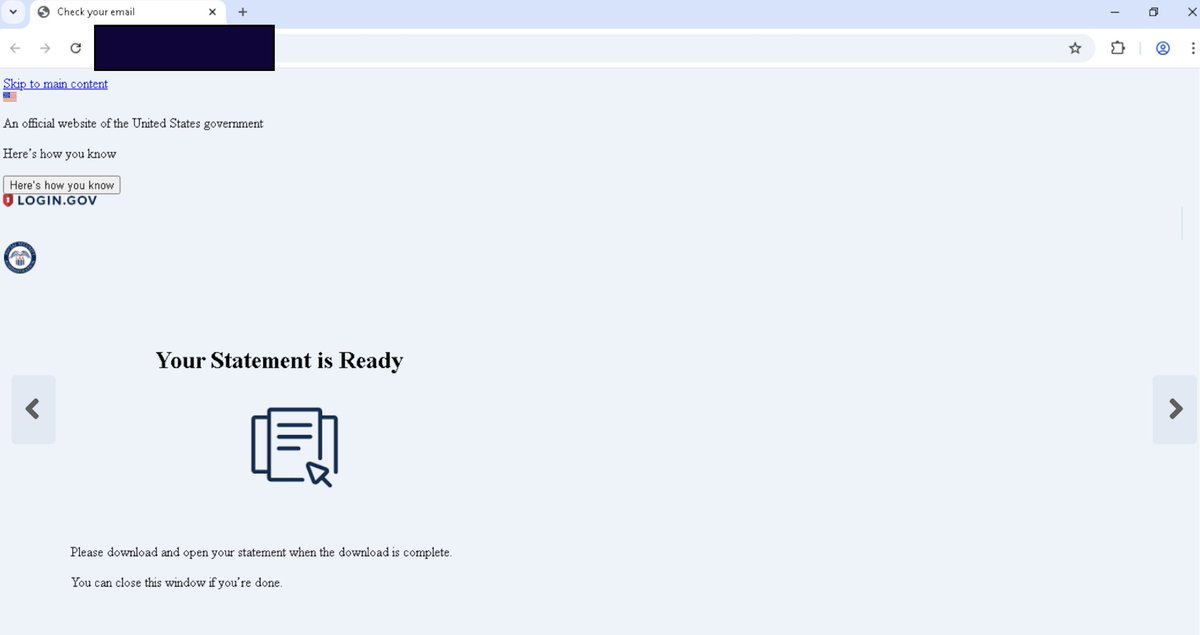
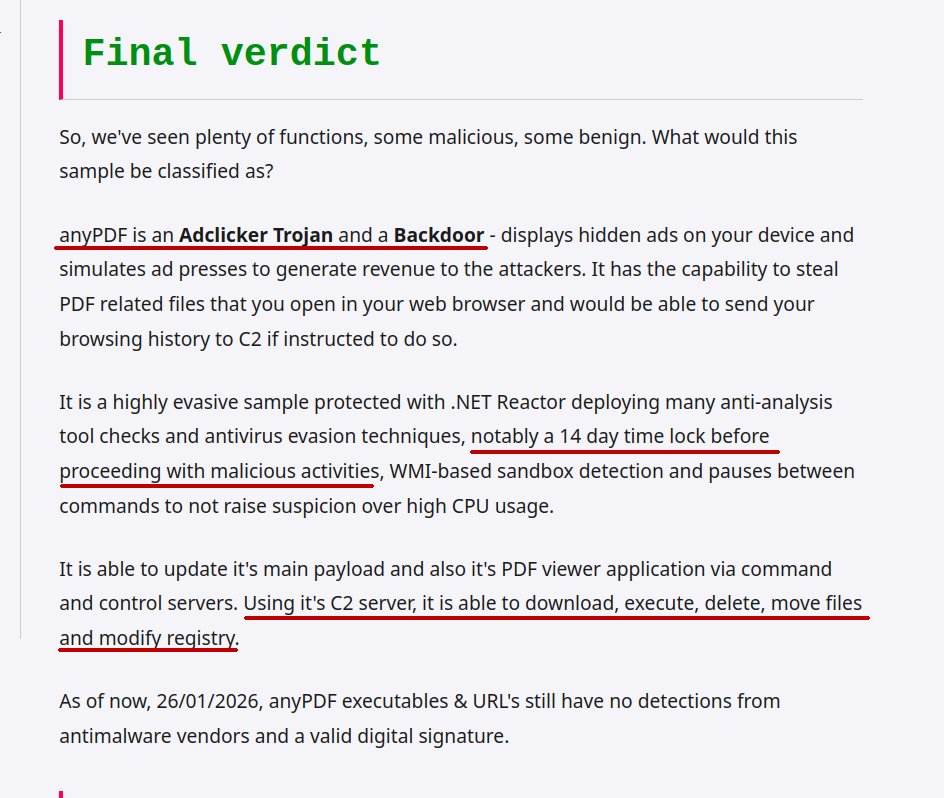
Popular Text Editor Notepad++ was compromised by a nation state attacker presumably from June through December 2, 2025. The state actor used the access to reroute software update traffic to attacker controlled servers making this a supply chain attack. notepad-plus-plus.org/news/hijacked-…

MalasadaTech YAPA... Galacticpdf (97e814385de850e7dbc934e2c8cdce46).

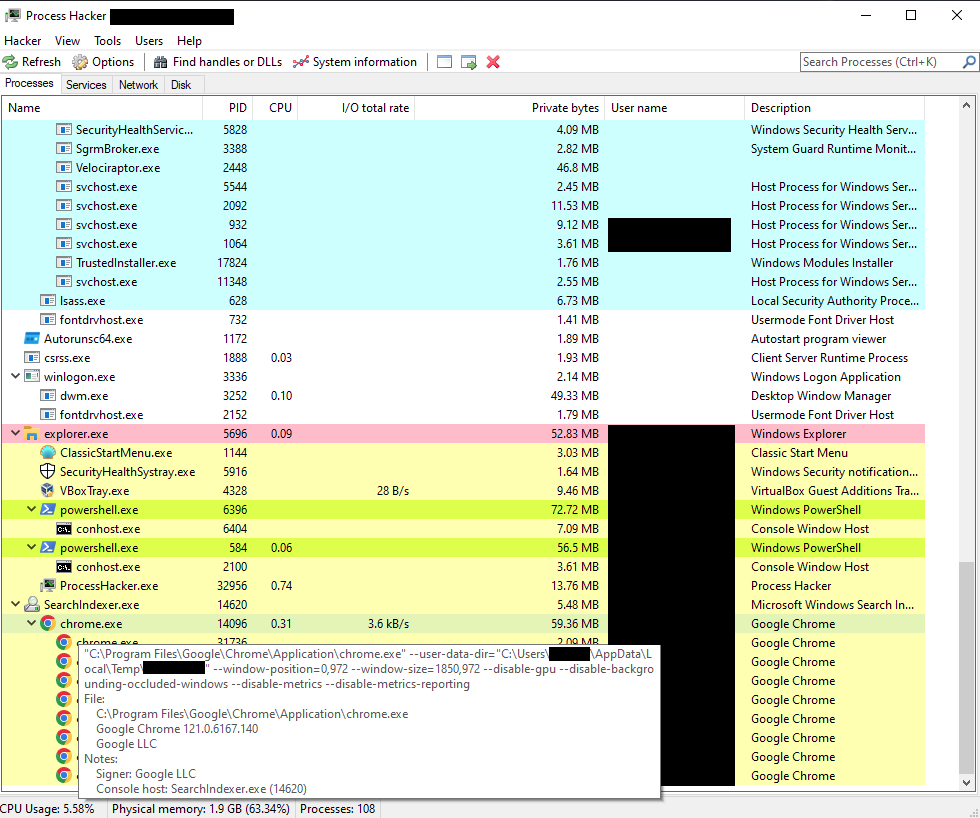
MalasadaTech this relation in virustotal (b7e3b66d28429c07714bb0b8e9487bc9) suggests another browser search hijacker

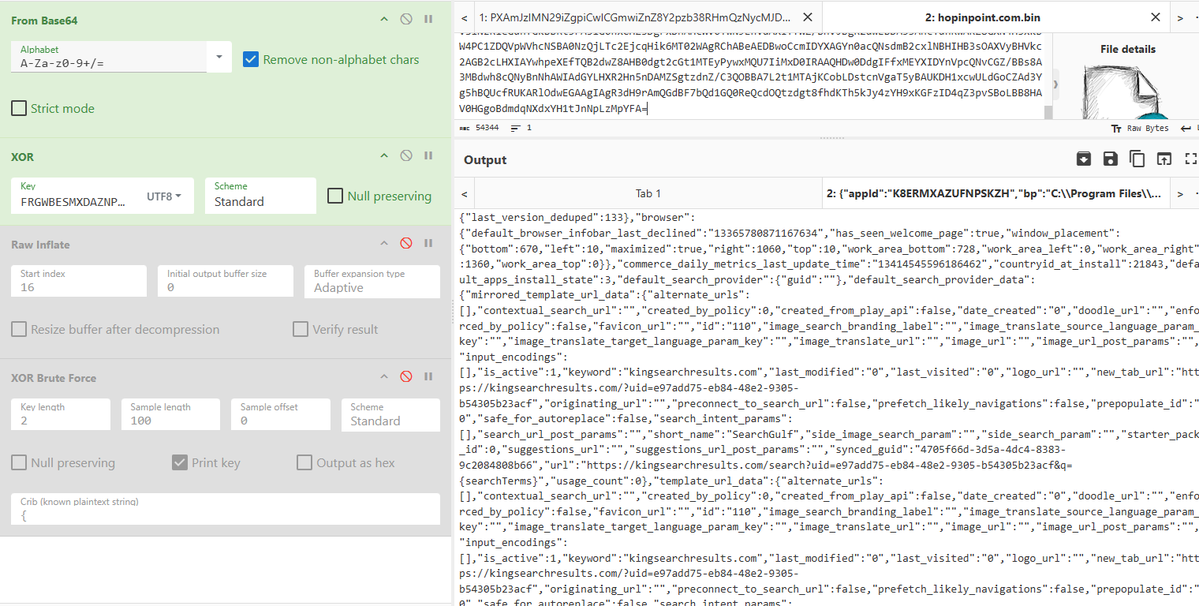
MalasadaTech Rust based, the embedded PE file is pdfium.dll. app.any.run/tasks/b71ca08e… HTTP comms to hopinpoint[.]com. Some custom encoded traffic here that I have not played with yet.
![Luke Acha (@luke92881) on Twitter photo <a href="/MalasadaTech/">MalasadaTech</a> Rust based, the embedded PE file is pdfium.dll. app.any.run/tasks/b71ca08e…
HTTP comms to hopinpoint[.]com. Some custom encoded traffic here that I have not played with yet. <a href="/MalasadaTech/">MalasadaTech</a> Rust based, the embedded PE file is pdfium.dll. app.any.run/tasks/b71ca08e…
HTTP comms to hopinpoint[.]com. Some custom encoded traffic here that I have not played with yet.](https://pbs.twimg.com/media/HAPzyYdWwAAos07.png)


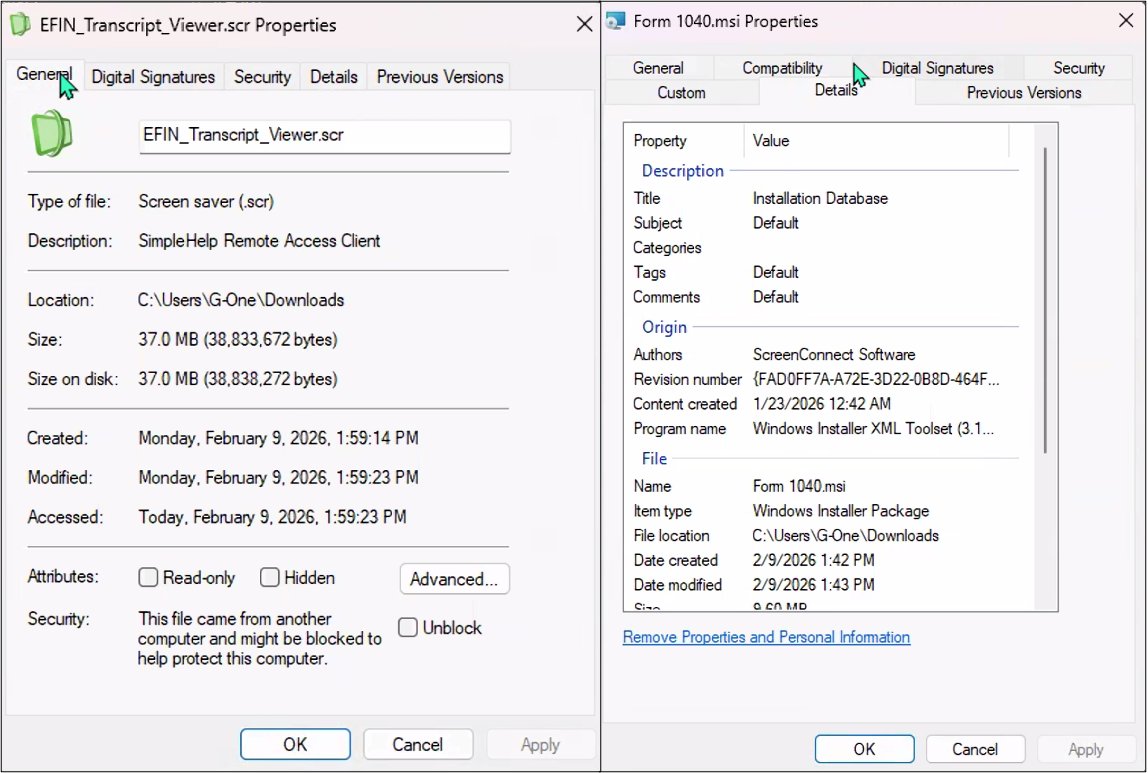
MalasadaTech also has same URI structures and talks to pdfappup[.]com and starrtlightspirit[.]com



![Unit 42 (@unit42_intel) on Twitter photo Belarus-based #APT #WhiteLynx is using a #CAPTCHAmacro technique, enticing users to enable macros on Office docs, generating a CAPTCHA verification window to proceed. We found follow-up malware that communicates with agelessinvesting[.]xyz. Details at bit.ly/4rRgFa9 Belarus-based #APT #WhiteLynx is using a #CAPTCHAmacro technique, enticing users to enable macros on Office docs, generating a CAPTCHA verification window to proceed. We found follow-up malware that communicates with agelessinvesting[.]xyz. Details at bit.ly/4rRgFa9](https://pbs.twimg.com/media/G75t1vVWMAANZkx.jpg)