Lê Hữu Quang Linh 🇻🇳
@linhlhq
Security researcher
ID: 954363747111354369
https://ezqelusia.blogspot.com/ 19-01-2018 14:43:43
538 Tweet
2,2K Followers
852 Following

Finding and chaining 4 vulns to exfiltrate encryption keys from the Android Keystore on Samsung series A* devices. Did you miss the "Attacking the Samsung Galaxy A* Boot Chain" talk by Maxime Rossi Bellom and Raphaël Neveu earlier this year ? Talk && PoC || GTFO: blog.quarkslab.com/attacking-the-…









The fifth article (57 pages) of the Exploiting Reversing Series (ERS) is available on: exploitreversing.com/2025/03/12/exp… I would like to thank Ilfak Guilfanov Ilfak Guilfanov and Hex-Rays SA Hex-Rays SA for their constant and uninterrupted support, which have helped me write these articles over



In our latest MindShaRE blog, renorobert describes how to use Binary Ninja’s MLIL to establish a data flow graph by tracing interactions between a specific memory allocation in order to find UAF bugs. He includes source code so you can, too. zerodayinitiative.com/blog/2025/3/20…

One Bug to Rule Them All: Stably Exploiting a Preauth RCE Vulnerability on Windows Server 2025 by zhiniang peng @ver0759 Zishan Lin i.blackhat.com/Asia-25/Asia-2…






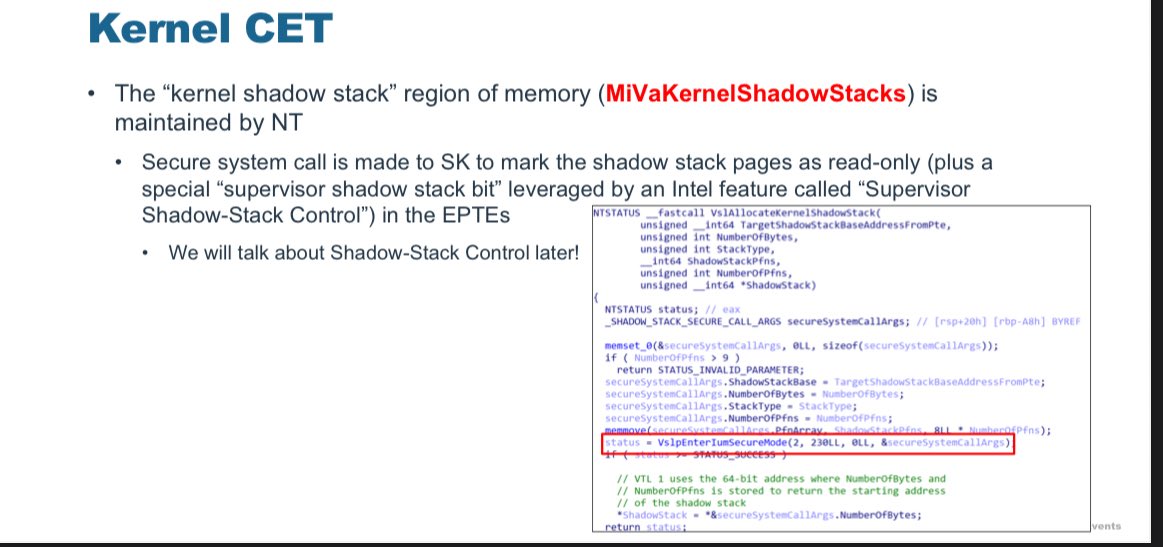
Out Of Control: How KCFG and KCET Redefine Control Flow Integrity in the Windows Kernel by Connor McGarr i.blackhat.com/BH-USA-25/Pres…