Sreeram KL
@kl_sree
Infosec enthusiast! | @googlevrp fan boy 😍 | CTF @thehackerscrew1 | CS student | Web Security
ID: 952234523965575168
https://blog.geekycat.in/ 13-01-2018 17:42:56
2,2K Tweet
2,2K Followers
863 Following




New: Repeater Strike Written by Gareth Heyes \u2028, powered by Burp AI! Scale IDOR & fuzzing like never before: 🤖 Auto-build regex rules with AI 📊 Scan proxy history for similar bugs 🛠️ Save, edit, and re-run rules easily #BurpAI






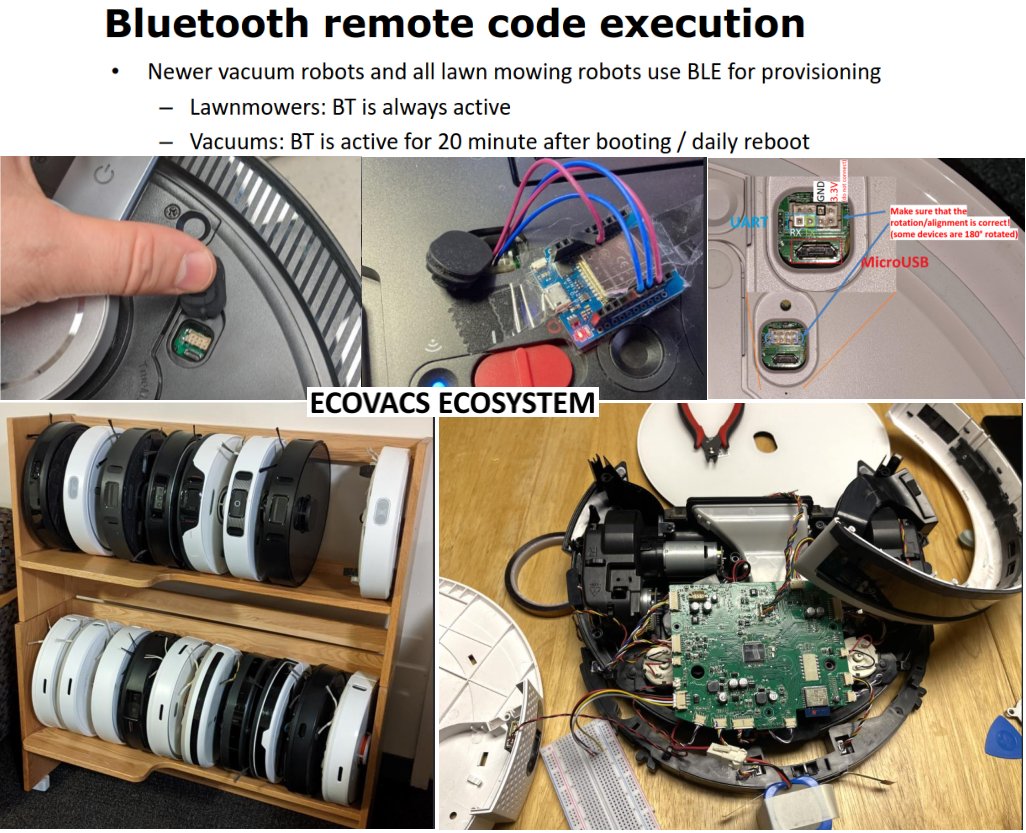
The Schedule is Live! Check out the lineup of talks, workshops, panel discussions, and hands-on activities happening at Adversary Village at DEF CON 33! Schedule: adversaryvillage.org/adversary-even… Mark your calendars - we can't wait to see you all at DEF CON! #AdversaryVillage #DEFCON33






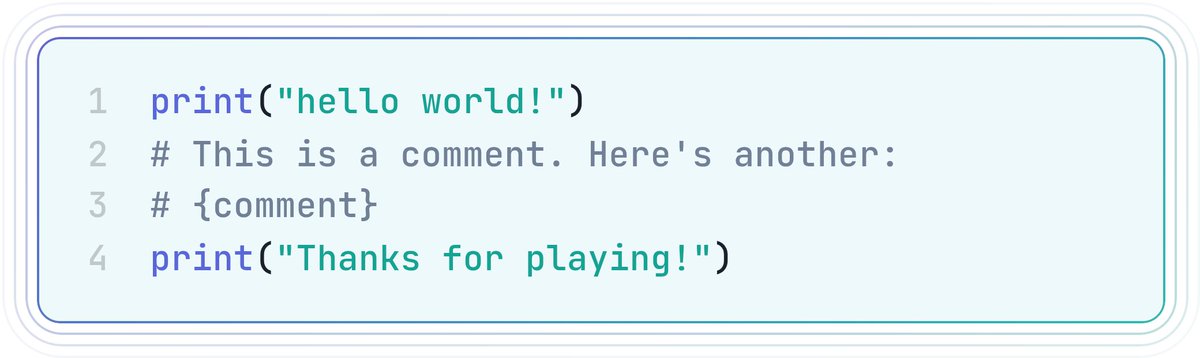
Can you execute arbitrary Python code from only a comment? This was the premise of a recent CTF challenge, which I solved after diving into the CPython source code with the help of Hacktron AI (after a long night chasing a dead end, customising a few Hacktron agents helped me to




Thanks PortSwigger and Bug Bounty Village for this awesome event — and also to my DEVCORE buddies for standing on stage to collect the trophy for me! A little follow-up article on this research is coming soon... stay tuned! 🤘