ComProfessor
@itscomprofessor
JavaScript, React, Python
ID: 1417344923666370567
20-07-2021 04:45:49
14,14K Tweet
189 Followers
144 Following













The CA Board of Directors and Management has today visited the Rukanga sub-location of Taita Taveta County which has been connected to mobile network services through the Universal Service Fund (USF), a Fund managed by the Authority to avail communications services...1/2







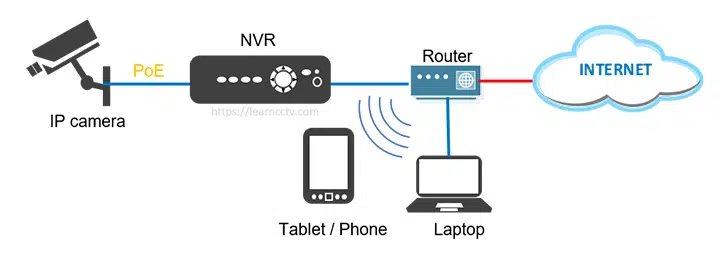
Konstantin Dabchev Yes, use shielded ethernet cables and ground the router like this for complete peace of mind x.com/helios_brah/st…