Hardik Shah
@hardik05
Principal Security Researcher - Tweets and opinions are my own and not of my employer. #fuzzing #trainings #security YouTube: youtube.com/@MrHardik05
ID: 8790062
http://fuzzing.in/ 10-09-2007 17:03:59
6,6K Tweet
4,4K Followers
3,3K Following





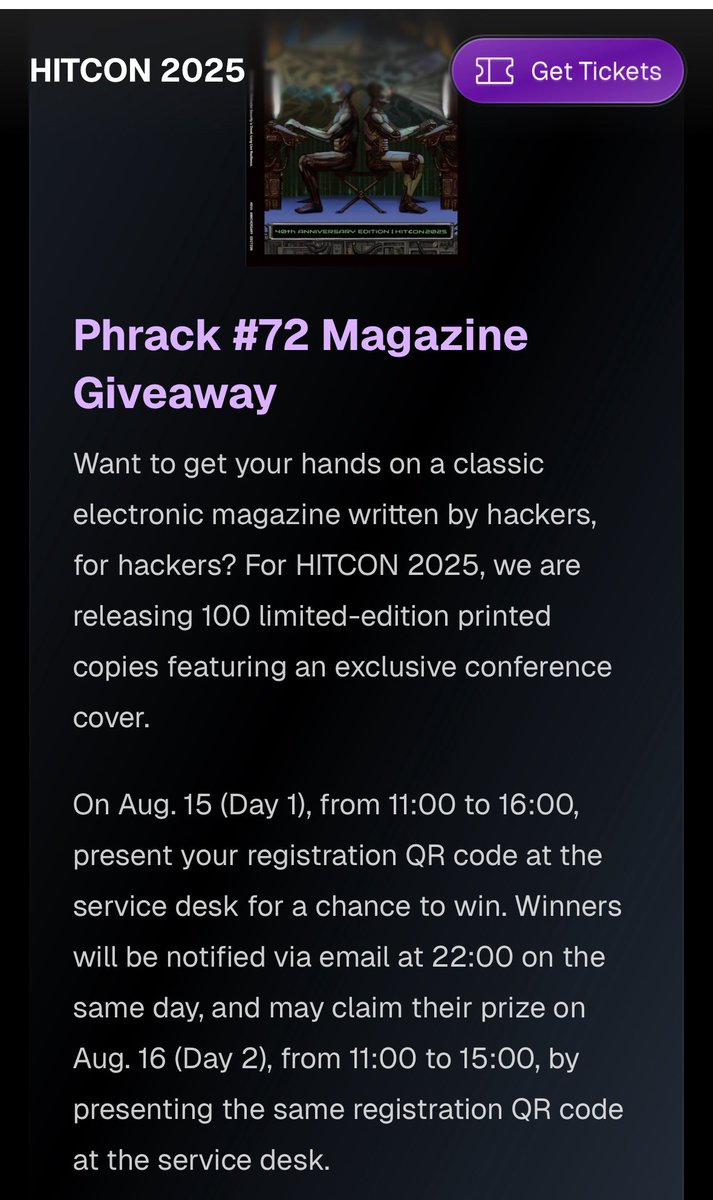
Bypass Kernel Barriers: Fuzzing Linux Kernel in Userspace With LKL Xuan Xing & Eugene Rodionov Eugene Rodionov gave a talk about fuzzing the Linux kernel interfaces completely in user space using LKL (Linux Kernel Library) static.sched.com/hosted_files/l…













As it turns out, Orange Tsai 🍊 and I have more in common than I had thought! If you love old school PHP quirks and CTF tricks I recommend you read our articles: phrack.org/issues/72/5_md… phrack.org/issues/72/6_md…


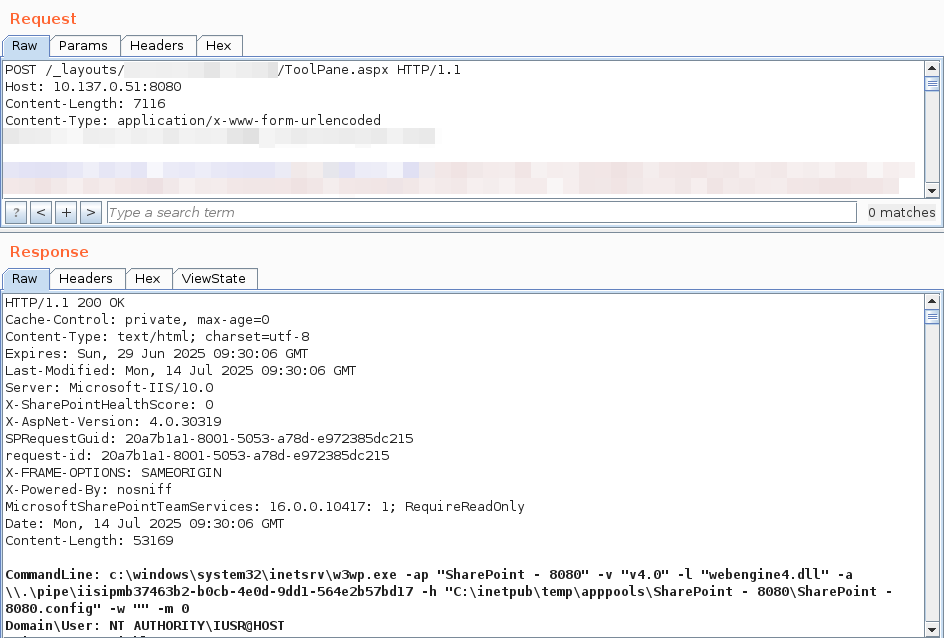



![xvonfers (@xvonfers) on Twitter photo Whoah... $250000
(CVE-2025-4609, similar to CVE-2025-2783/412578726)[412578726][Mojo][IpczDriver]ipcz bug -> renderer duplicate browser process handle -> escape sbx is now open with PoC & exploit(success rate is nearly 70%-80%)
issues.chromium.org/issues/4125787…
issues.chromium.org/issues/4125787… Whoah... $250000
(CVE-2025-4609, similar to CVE-2025-2783/412578726)[412578726][Mojo][IpczDriver]ipcz bug -> renderer duplicate browser process handle -> escape sbx is now open with PoC & exploit(success rate is nearly 70%-80%)
issues.chromium.org/issues/4125787…
issues.chromium.org/issues/4125787…](https://pbs.twimg.com/media/Gx8LeLaWcAA__Xu.jpg)