
zhixiang hao
@haozhixiang
APT threat,Web security,Osint
Shandong Lanxiang School China。My sample analysis is just for learning research
ID: 1463316372541169671
24-11-2021 01:20:08
505 Tweet
1,1K Followers
343 Following


One command to get ssrf mining gau --subs xxx.com | gf ssrf | sort -u | httpx -mc 200 | qsreplace "burpcollaborator" >> ssrfuzzxxx.txt; ffuf -c -w ssrfuzzxxx.txt -u FUZZ happy hunting everyone😄 🇸🇦 Murtada Bin Abdullah (Rood) Justin Gardner zseano H1 Disclosed - Public Disclosures H4x0r.DZ N$






zhixiang hao Kornelij Narek Babajanyan🇦🇲 thank you for pointing us to this, we've done some additional research and will release more details soon cyberhub.am/en/blog/2023/0…





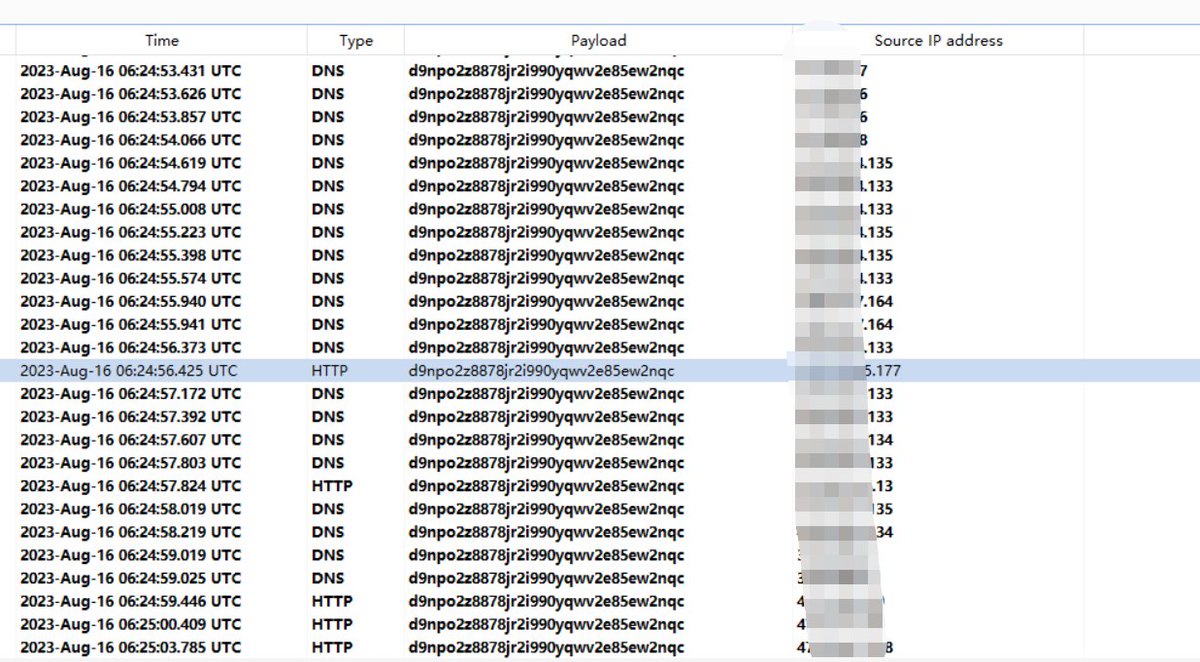
![zhixiang hao (@haozhixiang) on Twitter photo APT Gamaredon
The content of the document is a forged document of "Electronic Trust Service of the Shastinska Regional Electricity Administration of Ukraine"
наказ_в_дпов_дальної особи.doc
http]://principles67.vilitord.ru/BUDGET/stoppage56/rejoice/already[.]mkv
can't access APT Gamaredon
The content of the document is a forged document of "Electronic Trust Service of the Shastinska Regional Electricity Administration of Ukraine"
наказ_в_дпов_дальної особи.doc
http]://principles67.vilitord.ru/BUDGET/stoppage56/rejoice/already[.]mkv
can't access](https://pbs.twimg.com/media/F407bzIbMAAPHqX.png)


