HACKDEFI
@hackthedefi
ID: 1755004066001035264
06-02-2024 23:02:41
63 Tweet
45 Followers
34 Following




📢Announcement Time 📢 We're very excited to be working with Chainlink Labs to bring our on-chain security solutions to #ChainlinkBUILD members to help Web3 #builders safeguard dApps and innovate with a peace of mind. Read more in our blog here: medium.com/fuzzland-blog/…



🌟 Excited to support DeFiHackLabs!

My [DAY 2] in EthCC - Ethereum Community Conference 2024 I had a wonderful discussion with other researchers and engineers about DeFi security/security methods ~ Especially thanks: - siyu.uni.eth from (Uniswap Labs 🦄), - Jeff from (HACKDEFI) - Victor Zhou🍊🛡️Namefi.io from (Namefi.io 🍊) - Rob from (Remix Project)
![Daniel.T 🏍️ (@mr_dddt) on Twitter photo My [DAY 2] in <a href="/EthCC/">EthCC - Ethereum Community Conference</a> 2024
I had a wonderful discussion with other researchers and engineers about DeFi security/security methods ~
Especially thanks:
- <a href="/JohnJsy0216/">siyu.uni.eth</a> from (<a href="/Uniswap/">Uniswap Labs 🦄</a>),
- Jeff from (<a href="/hackthedefi/">HACKDEFI</a>)
- <a href="/ZainanZhou/">Victor Zhou🍊🛡️Namefi.io</a> from (<a href="/namefi_io/">Namefi.io 🍊</a>)
- Rob from (<a href="/EthereumRemix/">Remix Project</a>) My [DAY 2] in <a href="/EthCC/">EthCC - Ethereum Community Conference</a> 2024
I had a wonderful discussion with other researchers and engineers about DeFi security/security methods ~
Especially thanks:
- <a href="/JohnJsy0216/">siyu.uni.eth</a> from (<a href="/Uniswap/">Uniswap Labs 🦄</a>),
- Jeff from (<a href="/hackthedefi/">HACKDEFI</a>)
- <a href="/ZainanZhou/">Victor Zhou🍊🛡️Namefi.io</a> from (<a href="/namefi_io/">Namefi.io 🍊</a>)
- Rob from (<a href="/EthereumRemix/">Remix Project</a>)](https://pbs.twimg.com/media/GSHnrNmWUAAkCFH.jpg)





All About DeFi and Future of Finance - Full Course in 4 playlists (80 YT Videos): LINKS 👇 1. Course I: DeFi Infrastructure: 📎youtube.com/playlist?list=… 2. Course II: DeFi Primitives: 📎youtube.com/playlist?list=… 3. Course III: DeFi Deep Dive: 📎youtube.com/playlist?list=… 4. Course IV:



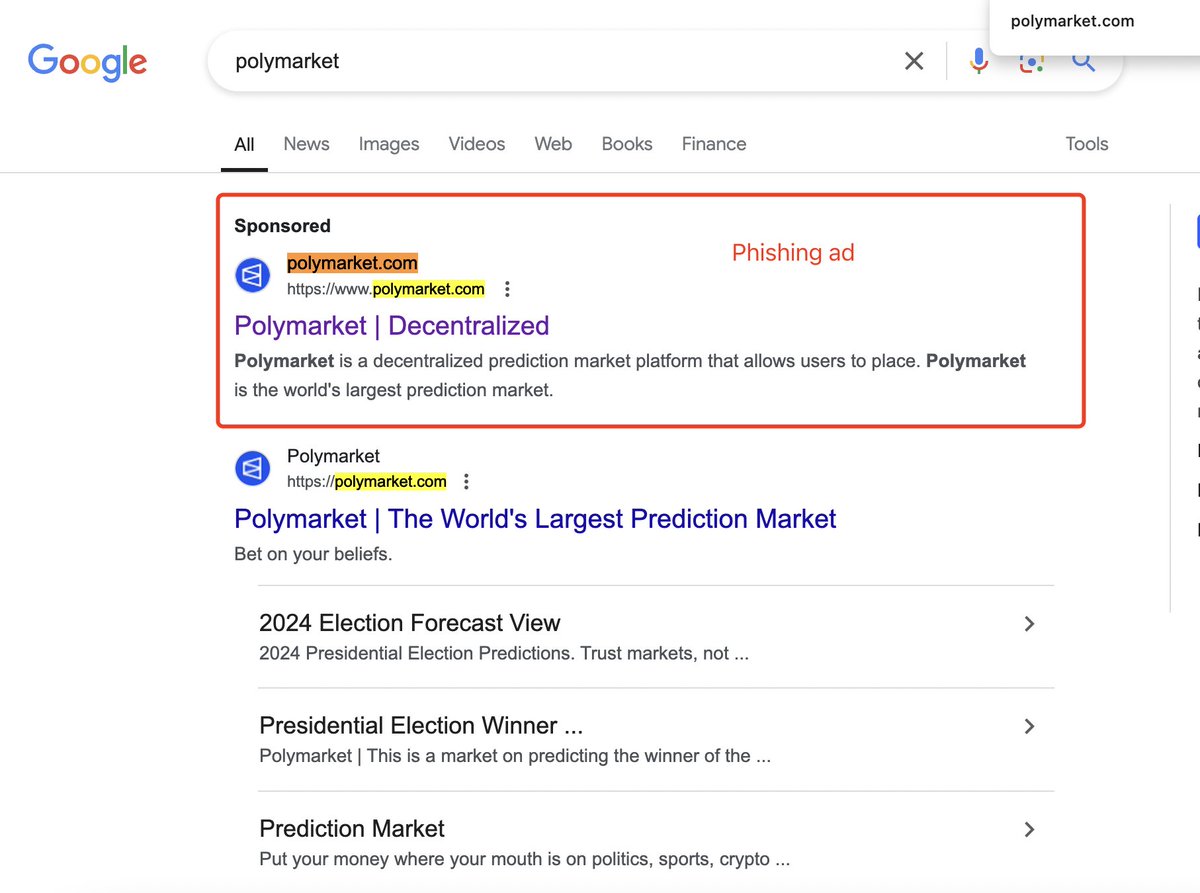
🚨 Phishing Alert: Polymarket users targeted on Google search! 🔍 Protect your assets—avoid simple mistakes. Get our security extension now! 🛡️✨ Stay safe and alert! ⚠️

🚨SlowMist Security Alert🚨 We detected potential suspicious activity related to Bedrock | ✈️ #KBW2025 🇰🇷 due to mistakenly supporting the minting of uniBTC at a 1:1 exchange rate with the native token. As always, stay vigilant!