malware and kittens, basically. she/her
ID: 76923611
24-09-2009 12:09:05
9,9K Tweet
2,2K Followers
2,2K Following


Stoked to announce the #OBTS v8 trainings! 🔗 objectivebythesea.org/v8/trainings.h… This year we’ve expanded adding 2 brand-new trainings: 1️⃣ "*OS – Security & Insecurity" by Jonathan Levin 2️⃣ "AI for Mac Security" by Dr. Kimo Bumanglag (of OpenAI) Trainings always sell out — sign up today!

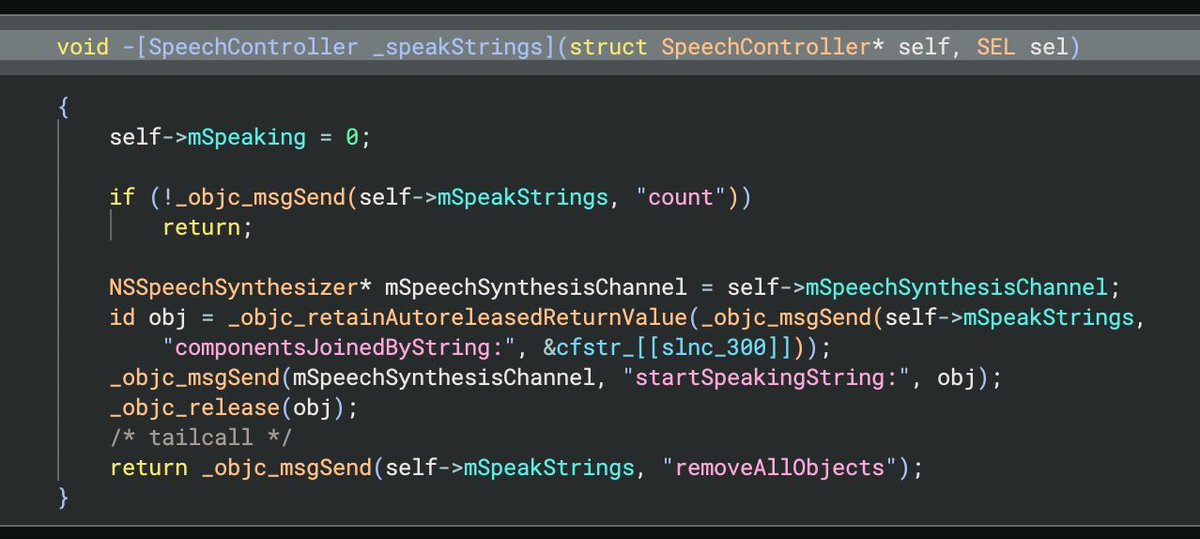
This definitely happened quickly after reading Patrick Wardle's blog post.


🎙️😍 Was stoked to talk nerdy on the Mac Admins Podcast! If you're interested in macOS malware, Apple security & detection, and much more, have a listen: linkedin.com/feed/update/ur…




Stoked for this #OBTS talk (and congrats on the CVE Ferdous Saljooki)! ...but phew, Apple cutting it close on the patch!⌛️😅






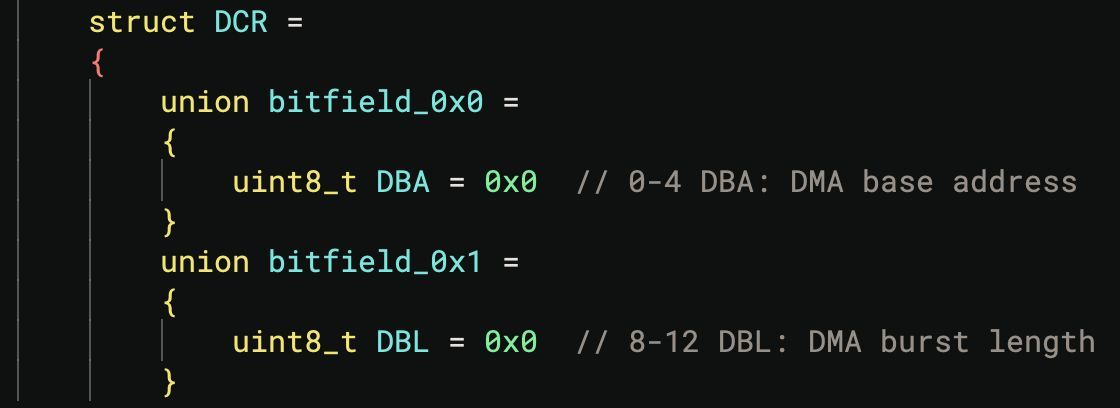
The slidedeck to our talk, Crash One: A Starbucks Story - CVE-2025-24277, with Gergely Kalman from Hexacon and Objective-See Foundation #OBTS is available from the link below. It was a macOS vulnerability impacting the crash reporting process where we could achieve LPE and sandbox

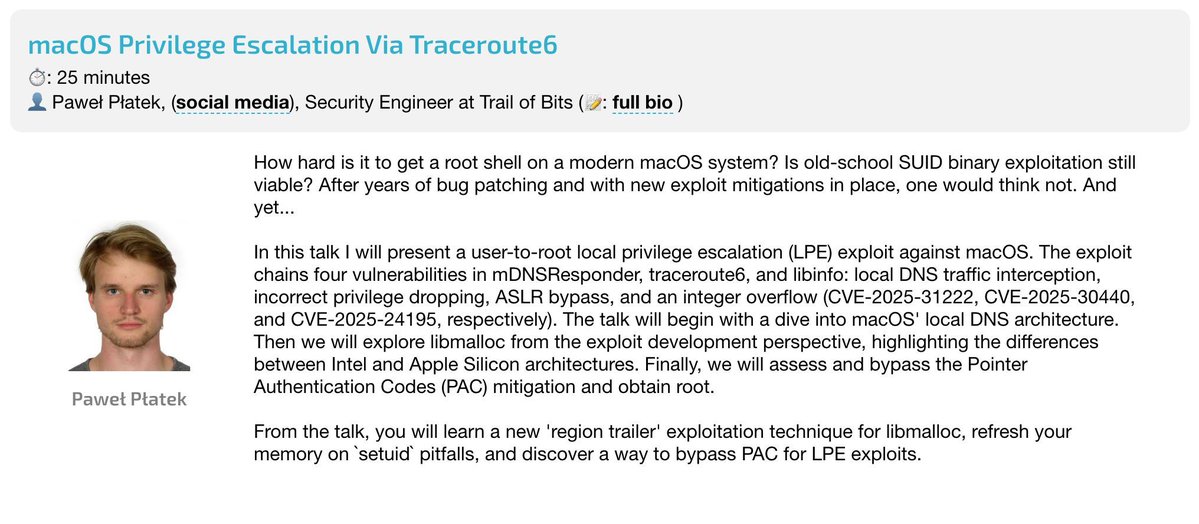
Today (4:00 PM GMT+2) Objective-See Foundation: Paweł Płatek shows a user-to-root exploit on modern macOS by chaining bugs in mDNSResponder and traceroute6. Learn new libmalloc exploitation techniques and PAC bypass methods. objectivebythesea.org/v8/

loved watching alden and Stuart Ashenbrenner 🇺🇸 🇨🇦 present at Objective-See Foundation today! they even got dressed up for the occasion 💙

Starting to think I should have made #OBTS bingo cards - I don’t think I’ve ever heard a speaker use the phrase “bee’s knees” before 😹 Sharvil Shah dropping some jokes along with FSKit knowledge ❤️


Congratulations to everyone at the #obts organization, especially Patrick Wardle Andy Rozenberg also a thank you for the opportunity to help at the CTF Erika Noerenberg [email protected] and Sarah Edwards 👩🏻💻🐈⬛! See you next year!! mahalo \0